EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USOTV FHRP Isolation & Stability Conditions
OTV FHRP Isolation:
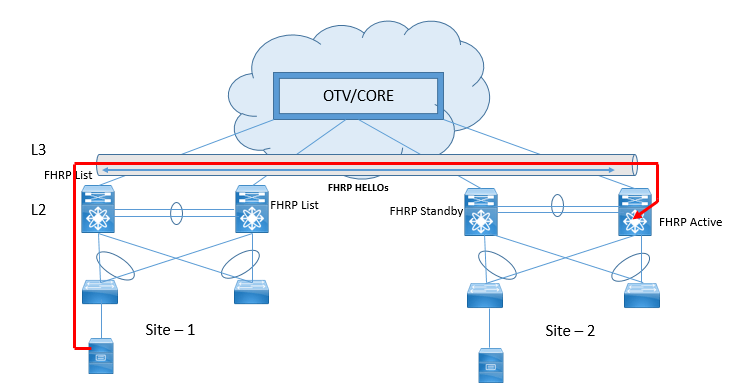
When FHRP is implemented, OTV filter FHRP messages across overlay. This is very much required on OTV domain because by this, same default gateway can be used at different site. Let’s understand what issue will occur if the FHRP isolation is not done by OTV.
Let’s Suppose the VLAN/IP subnet are configured at different site and FHRP message are exchanged between them , which would cause the SITE-2 VLAN acts as FHRP Active and Standby . Now if any host want to reach to its VLAN gateway, it has to travel all across OTV Overlay to another site SITE-2 and route the traffic in different subnet which may cause suboptimal path selection for routing between different subnets.
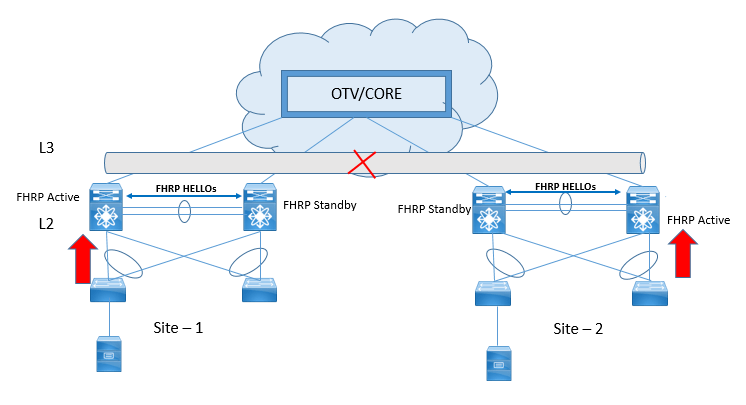
Now let’s suppose OTV provides the FHRP isolation, where FHRP packets are filtered and are not allowed to cross the OTV Overlay, this will cause the same FHRP gateway at both location with same Virtual MAC address on both site and any traffic which has to be routed between different subnets need not to be traversed across OTV Overlay to reach to another site for Gateway.
To enable Filtering two steps are required :
Step1: 1Configure a VLAN ACL (VACL) on the OTV VDC.
The VLAN ACL is required for the traffic that needs to be filtered. The configuration below applies to the HSRP version 1 protocol, which is enabled by default on NX-OS and in bold are highlighted the specific commands required to filter HSRP version 2 packets. Notice how it is also required to apply a specific filter to ensure suppression of the Gratuitous ARP (GARP) messages that may be received across the OTV Overlay from the remote sites. This can be achieved by ip arp inspection filter command.





LEAVE A COMMENT
Please login here to comment.