EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USHSRP Concepts
FHRP is the first hop redundancy protocols which provides 24*7*365 days active gateways to all hosts configured in DC. There are three FHRP protocols available which we will be discussing here.
- Hot Standby Router Protocol (HSRP)
- Virtual Router Redundancy Protocol (VRRP)
- Gateway Load balancing Protocols.
We will discuss one by one in detail and how it behave in VPC environment.
HSRP:
HSRP is the Cisco Propriety Hot Standby Router Protocol. Which has following characteristics:
- It enables two or more router to provide first-hop redundancy for all IP traffic
- In HSRP one router is Active and one in standby and all other are in listen state,
- Active router is responsible for ARP resolution and forwarding all traffic.
- All the routers/switch participating in HSRP for a Single VLAN must be in same group.
- HSRP can support 16 groups at maximum.
- The Active router has virtual IP address which in turn has Virtual MAC address for ARP resolution.
- If Active router fails then standby will resume the active state with same Virtual MAC address.
- There is no preemption by default, if any point of time, Active Router who was failed comes if U P than it will not resume its status as Active by its own.
- HSRP hello packets are used to elect the Active and Standby router, those who has Highest Priority will become active router and second priority will become standby router on multicast address 224.0.0.2.
- Hello Timer is 3 sec and Hold Down timer is 10 sec.
- Default Priority of router is 100 and if all router has same priority then Highest IP address of device will be used to elect the Active and standby.
- In Nexus HSRP is enabled by enabling feature command.
- In HSRP, HSRP packets can also be secured by HSRP authentication method.
- HSRP uses plain-text or MD5 method to secure its packets.
HSRP/VRRP Behaviour in vPC
Whenever we configure the HSRP and VRRP in vPC domain , it behaves or operates in active-active mode, means all the ARP request and replay are handled by HSRP Active but for data traffic both Active and Standby acts as active-active . From a control plane standpoint, active-standby mode still applies for HSRP/VRRP in context of vPC; the active HSRP/VRRP instance responds to ARP request. HSRP and VRRP operate in active-active mode from data plane standpoint, as opposed to classical active/standby implementation with STP based network.
If any traffic is send to HSRP standby, instead of sending to HSRP Active over vPC peer-link it acts as Active gateway and forwards the traffic to northbound.
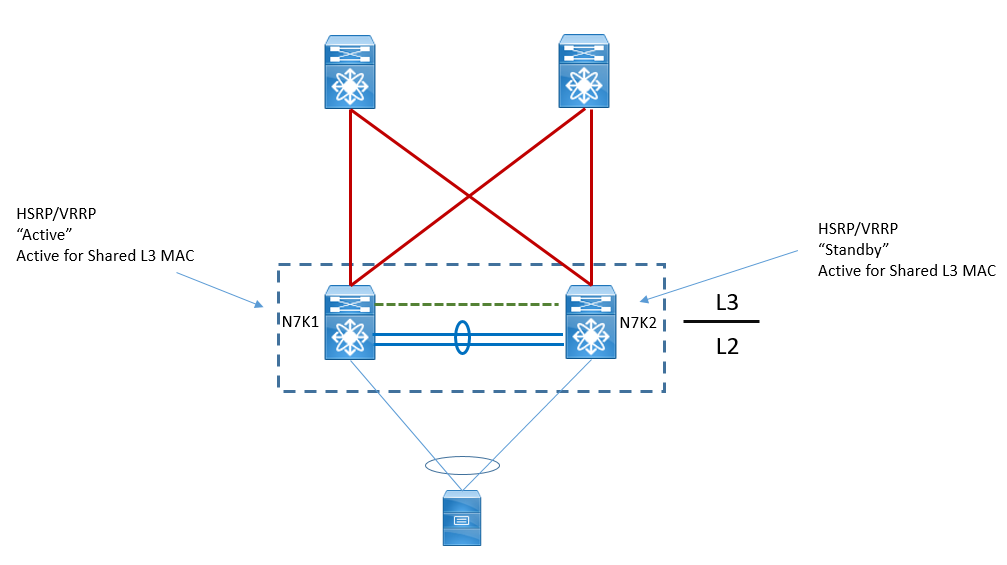
The standby HSRP/VRRP vPC peer device just relays the ARP request to active HSRP/VRRP peer device through vPC peer-link.Here also same vMAC is used as Gateway MAC address at both Active and Standby switch. You can see this by following output:





LEAVE A COMMENT
Please login here to comment.