EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USVPC Enhancements
vPC systems provide various advance concepts which can be used to enhance the vPC system. Following are the vPC enhancement we are going to study one by one:
- vPC Peer-Gateway
- vPC Peer-Gateway Exclude VLAN
- vPC ARP SYNC
- vPC Delay Restore
- vPC Graceful Tye-1 Check
- vPC Auto-Recovery
- vPC Orphan Port Suspended
vPC Peer-gateway:
As we are aware that, In HSRP/VRRP systems, Both Nexus switch can route packet to HSRP Virtual VMAC and all upstream traffic will be load balanced through vPC Port-channel in access switches and Access switch sends the traffic to HSRP VMAC of SVI for Routing.
But in some cases like NAS servers, Servers with particular teaming technique might not send the any ARP request to discover gateway MAC address rather they use the MAC address received on the original request to build its response and NAS would reply to client request and these reply will be directed to SVI MAC address and not to HSRP VMAC address.
Due to this it can create the undesired traffic flow in vPC. Let’s understand this by below example:
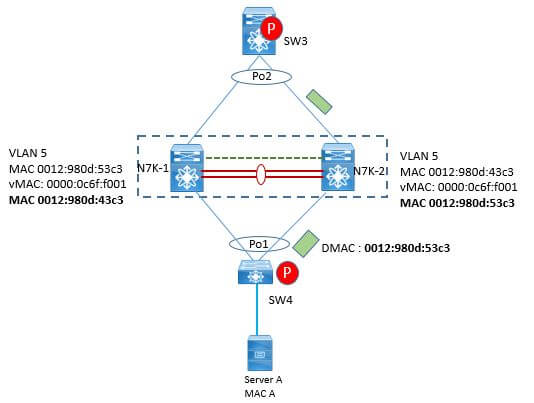
In above figure let’s say,
- NAS sends the IP Packet for destination MAC 0012:980d: 53c3 which is SVI MAC of VLAN 5 on N7K1 using the interface connected to N7K2 due to port Channel hash algorithms.
- Once N7K2 receives this frame and checks the MAC address table and based on result, it will forward this to N7K1 .
- N7K1 will block this packet if this has to be forwarded out to a vPC port due to vPC loop avoidance method.
This issue can be solved easily by Peer-gateway command under vPC Domain. If both vPC peer is configured with this command each of them can route packet out to vPC port because VLAN 5 SVI MAC of N7K1 will also be present on N&K2 and vice Versa , as shown in above figure.





LEAVE A COMMENT
Please login here to comment.