EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USQOS Policing & Shaping
Traffic Shaping When and Where:
There are two main reasons for which traffic shaping is used.
- To shape the traffic at same rate as policing
- To avoid the effect of egress blocking
Let’s discuss the both scenario one by one.
Shaping at same rate as Policing:
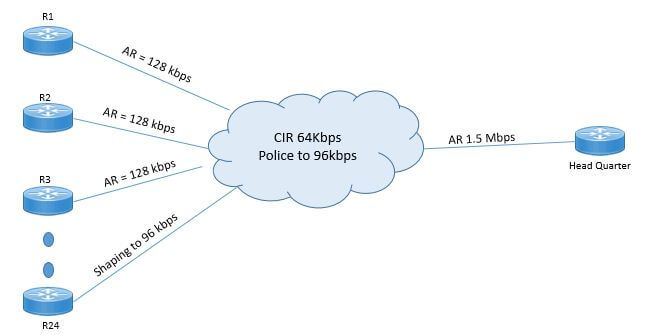
Let’s suppose you have branch site from branch 1 to branch 24 and there is one head quarter. Branch 1 does not shapes the traffic and whereas branch 24 shapes the traffic to 96kbps. In both cases WAN Switch is configured to police the traffic at 96kbps and CIR of each case is 64kbps.
Let’s suppose branch 1 let’s say send the traffic more than 96kbps, now WAN Switch will police the traffic and will cause the traffic drop. Branch 24 will delay the packet due to shaping and WAN switch will not discard the packet but some packet will experience more delay and jitter.
So to avoid the situation each Branch should shape the traffic with same rate as policing.
Avoid Egress Blocking:
Egress Blocking occurs when packets try to exit from Multi-Access WAN but cannot exit due to network congestion. Let’s take the previous example and suppose that shaping and policing is configure at 96kbps. Now If all branch from Branch 1 to branch send the traffic, about 2.25 Mbps of traffic needs to be exit to reach to headquarter but the Access rate of main router is 1.5 Mbps causes the egress blocking.
To avoid this situation, ALL Virtual Circuits at branches should shape the traffic to CIR of 64kbps due to which the cumulative offered load will not exceed the access Rate at Main site.
How Shaping works
Shaping only occurs when the physical clock rate of media exceeds a traffic contract. Any router can only send the traffic in and out at its physical clock rate To get the average bit rate over time lower than clock rate , router needs to send packets for some specified period to time and then not to send any packet for another time period.
Let’s understand this by this example, R1 has 128 kbps access rate and CIR of 64 kbps and a network admin wants to shape the traffic to match the 64kbps.Now in this case R1 has to send the traffic on link half of the time and if R1 does this and send the traffic half of the time at 128kbps it can get the average rate 64kbps over time.
So R1 will shapes the traffic at 64kbps with access rate 128kbps.
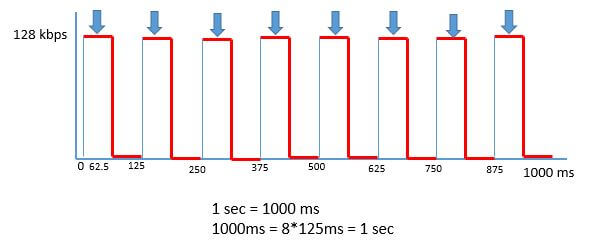
Now Tc defaults to 125 ms for many tools and application now R1 at the end of 125 ms would send the traffic to 62.5 ms and for next 62.5ms will be ideal and this will be done for next 8 interval to meet 1 sec thus R1 will send the 64kbps traffic with Access rate 128kbps.





LEAVE A COMMENT
Please login here to comment.