EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USSegmentation Overview
Network Segmentation allow network to isolate different LOB or users from each other unless specific policy allows to communicate between them.
There are some use cases where segmentation are used.
- Requirement to keep business units Separate from guest users
- Requirement to group prefixes in to unique route table
- A SP requirement to provide VPN service to its customers
- Requirement to provide selective access to business partners.
- Isolation of traffic between regular user & Guest users.
- When Extranet partners are allowed to access selective part of network
- PCI/HIPP network needs to be separated due to regulatory requirements.
Now when we configure Segmentation or VPN on device , it is limited and local to that device only and if we want to extend this function throughout network the VPN or segmentation information needs to be sent or carried throughout network.
There are following approaches used to provide this network segmentation:
- At every device and on every link define grouping policy to group prefixes
- Define group policy at edge device to carry the segmentation information to immediate host.
Let’s see how routing information is propagated inside VPN
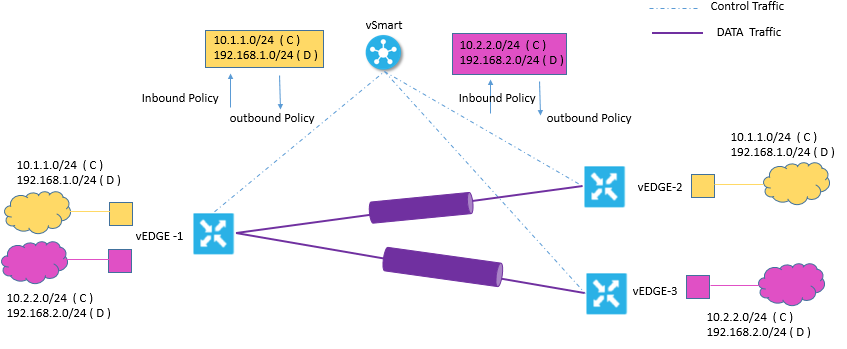
- VEdge-1 subscribes to two VPNs, yellow and Violet s it has two route table
- The Yellow VPN has prefix 10.1.1.0/24 (either directly through a connected interface or learned via the IGP or BGP).
- The Violet VPN has prefix 10.2.2.0/24 (either directly through a connected interface or learned via the IGP or BGP).
- vEdge-2 subscribes to the Yellow VPN so it has one route table
- This VPN has prefix 192.168.1.0/24 (either directly through a connected interface or learned via the IGP or BGP).
- vEdge-3 subscribes to the Violet VPN so it has one route table
- This VPN has prefix 192.168.2.0/24 (either directly through a connected interface or learned via the IGP or BGP).
Now each router has OMP connection to vSmart controller and they will share the routing information to controller. On vSmart controller, based on enforced polices by network admin, it can take action like drop routes, change TLOC, Change VPN id etc which is applied inbound or outbound direction.
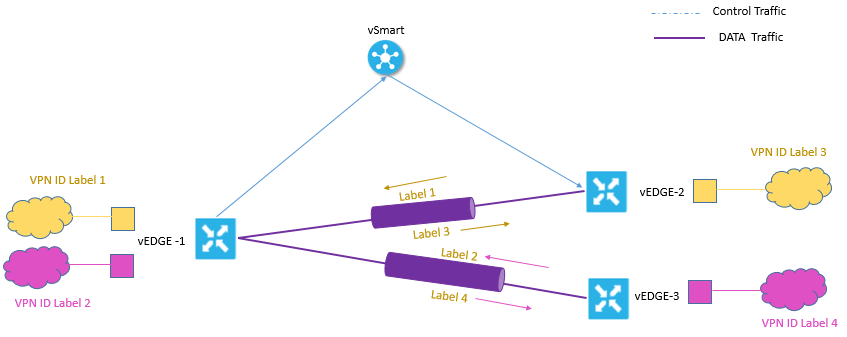
Now Based on VPN ID, these routing information is propagated across Viptela network. As soon as VPN is configured on vEdge router, it associates a Label to it and vEdge router sends the Label with VPN ID , to vSmart controller and then vSmart will propagate this vEdge-to-VPN ID mapping information to other Edge routers in the domain. And then the vEdge router will use this label to send the traffic to correct VPN and vice Versa
This can be understood by below diagram:
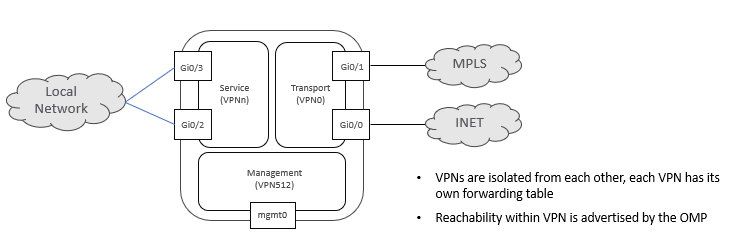
Cisco SDWAN solution provides segmentation via VPN. There are three different types of VPN in Cisco SD-WAN Solution.
- Service VPN: These VPNs are used for user traffic and are defined across Overly and terminated over LAN side of routers. We can have multiple Service VPN in the fabric and have multiple topologies for different VPNs. These VPNs have range value from 1 to 511.
- Transport VPN: This VPN is used where Physical WAN underlay transport terminates. This VPN is referred as VPN 0 and is assigned as WAN VPN and cannot be changed.
- Management VPN: This is for Out of band management Interface. It uses a VPN value 512, that cannot be changed.
Let’s understand the network Segmentation by below figure.
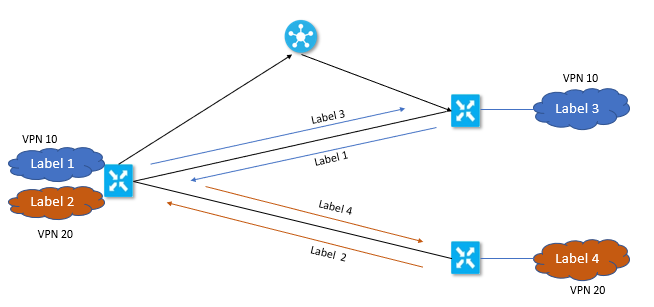
Each Data packet will carry a VPN ID that identifies it, to which VPN it belongs to on Overlay. Once VPN is configured on WAN Edges, it will have a label tied to it. Now When WAN edge build the control plane, It will send its label information along with VPN ID to vSmart controller. vSmart will distribute this VPN-ID mapping information to other WAN Edges in the network. The remote WAN Edges in the network will then uses these labels to send traffic for appropriate VPNs.
In Cisco SDWAN, Control plane and Data Plane are separated, due to which it allows us to build different topologies per VPN. Example: Hub & Spoke Topology, Point-to-Point topology, Full Mesh topology.
Dual Stack:
Dual stack feature is supported on vEdge and vSmart on VPN 0. If you want to enable dual stack configure IPV4 & IPV6 address on tunnel interface, based on traffic pattern, it will select either IPV4 or IPV6 interface




LEAVE A COMMENT
Please login here to comment.