EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USAuthentication between vBond & vEdge Router
When Ever a vEdge router is deployed in network, the first two things must be done
- Establish the secure connection with vManage so that it can receive the full configuration
- Establish the Secure connection with vSmart controller so that it can participate in Viptela Secure Overly network
The initial configuration of vEdge contains vBond system IP address or DNS name to establish the secure DTLS connection with it. This IP address is configured manually via initial configuration phase once vEdge is booted to start. Once the authentication between vBond and vEdge done successfully, vBond send the vManage and vSmart IP address to vEdge.
Once it is done, vEdge router tears down its connection with vBond and starts establishing DTLS connection with other two devices.
Below is the step by step procedure how automatic authentication occurs between vBond and vEdge.
vEdge router initiates DTLS connection to public IP address of the vBond, this encryption is provided by RSA and each device automatically generates RSA public and Private Key when it boots.
Once vBond receives the vEdge interface IP address and uses the outer IP address in the received packet to determine whether vEdge router is behind NAT and if it is true, vBond will create mapping of the vEdge Router public IP address and port with its Private IP address.
On this encrypted DTLS channel vBond and vEdge will start authentication process to each other.
Below procedure describes how vEdge router authenticates the vBond
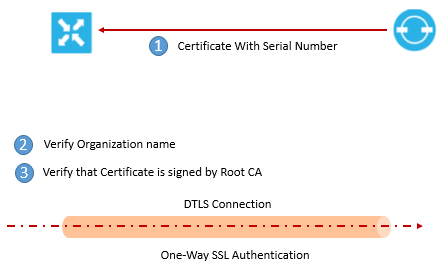
- vBond will send the trusted root CA signed certificate to vEdge Router
- vEdge Router uses it chain of trust to extract the organization name from certificate and match it with its own, if they don’t match it will tear down the DTLS connection.
- If the name matches , vEdge router uses its root CA chain to verify that vBond certificate is signed by root CA , if it is not so then vEdge router will tear down the connection
- And if the Root certificate is validated vEdge router now knows that vBond is valid and after this process authentication of vBond orchestrator is complete
Now let’s see how vBond authenticates the vEdge Router.
- vBond send the 256 bit challenge to vEdge router and this challenge is a random value.
- The vEdge router sends following response for the challenge that include following:
- vEdge Serial number
- vEdge Chassis number
- vEdge Board ID certificate
- 256 bit random value signed by vEdge router Private key
- vBond after receiving this information , compares the serial and chassis number from its vEdge authorized device list file , if there is no match vBond will tear down the connection
- if the match is found vBond check if the signing of 256 bit random value is proper or not by using vEdge router public key which it extracts from Router Board ID certificate , if the Signing value is not matched vBond will down the DTLS connection
- if the value is proper , vBond uses root CA chain from vEdge router board ID certificate to validate that board id certificate is itself valid or not , the certificate is not valid the vBond will tear down the connection





LEAVE A COMMENT
Please login here to comment.