EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USSDWAN NAT Scenarios
In SDWAN below are various type of NAT Deployment used.
- Full Clone NAT
- Symmetric NAT
- Address restricted Cone NAT
- Port Restricted Cone NAT
Full Clone NAT
It is also called as One to One NAT or Static NAT. In NAT address and ports are always open. All External Host initiating connections to this port are allowed and translated to internal host. You can have Multiple full cone NAT configured using same public IP , but ports that are being translated internally must be different per internal port.
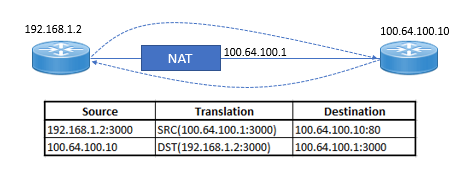
Traffic initiated from inside host to outside host with Source port 3000 will have its Source IP in the IP header translated to outside zone with source IP of 100.64.100.1 SRC IP: 192.168.1.2 translated to 100.64.100.1
When Outside initiated connection to 100.64.100.1:300 , the destination IP in IP header will be translated to inside zone with destination IP of 192.168.1.2 by NAT device. DST IP: 100.64.100.1 translated to 192.168.1.2.
Symmetric NAT
Symmetric NAT is also called as Dynamic PAT. It has advantages to allow large number of hosts behind single IP address. It is deployed where large number of users needs to access Internet and admin do not want to allocate individual IP to each user.
In Symmetric NAT , it allows port range up to 63,335 hosts behind a single IP address.
Below Figure explains Symmetric NAT
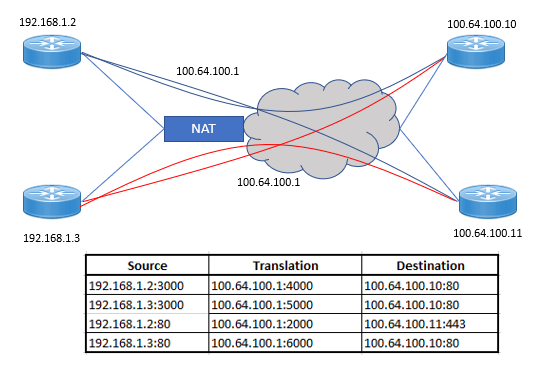
here are four hosts. Two are behind a NAT device configured with symmetric NAT. The two hosts are initiating various connections to the external hosts of 100.64.100.10 and 100.64.100.11. Let’s review these conversations:
Here are four hosts. Two are behind a NAT device configured with symmetric NAT. The two hosts are initiating various connections to the external hosts of 100.64.100.10 and 100.64.100.11. Let’s review these conversations:
- Traffic is being initiated from 192.168.1.2 connecting to the external host 100.64.100.10 with a service running on port 80. As with all TCP/UDP conversations, there is a source and destination port in the header. In this case, the source IP of 192.168.1.2 and the source port of 3000 will be translated to 100.64.100.1:4000. In most TCP/UDP conversations, the source port is selected randomly by the sending host.
- Similar to conversation 1, traffic is being initiated from 192.168.1.3 connecting to the external host 100.64.100.10 with a service running on port 80. In this case, the source IP of 192.168.1.3 and the source port of 3000 will be translated to 100.64.100.1:5000. Since the NAT device is translating the source port and source IP, you can see that we’re able to achieve great scale with symmetric NAT.
- In this conversation, host 192.168.1.2 is connecting to an external host with the IP of 100.64.100.11 running a service on port 80. The source IP and source port will both be translated to 100.64.100.1:2000.
- In this conversation, host 192.168.1.3 is connecting to an external host with the IP of 100.64.100.11 running a service on port 443. The source IP and source port will both be translated to 100.64.100.1:6000.
Address Restricted Cone NAT
This type of NAT works same as Full Cone NAT , except it only allows external hosts to communicate to internal host , if that host has communicated with external host before any port. The External host can then initiate a connection with internal host on any port that have been NATed.
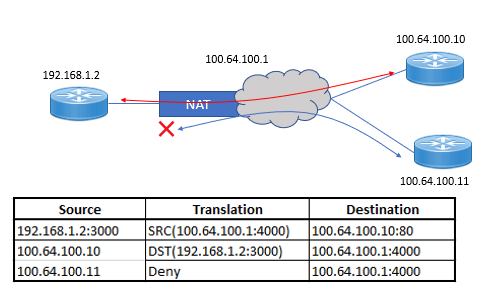
There are three hosts. One host is behind a NAT device, where the NAT configured is address restricted full cone NAT. The internal host is initiating connections to the external host of 100.64.100.10. Let’s review the conversations:
- The host behind the NAT device has initiated a connection to the destination IP of 100.64.100.10. The source IP is translated to 100.64.100.1 and the source port is translated from 3000 to 4000.
- Since the internal host initially connected to 100.64.100.10, 100.64.100.10 can now connect to 100.64.100.1 port 4000, and this traffic will be allowed. The destination IP and port will both be translated to 192.168.1.2:3000.
- When 100.64.100.11 tries to connect to 100.64.100.1 on port 4000, the traffic will be denied because the internal host has never initiated a connection to 100.64.100.11 previously.
Port Restricted Cone NAT
This NAT type is similar to restricted cone NAT , except it uses the port number as a filter. When an internal host connect to a remote system, it connects to a destination port. This port is then added to the NAT filter, and if any external host wants to communicate with the internal host, it must have the same source port that the internal host used as its destination port. If any external host uses a different source port, the traffic will be denied. If another external host uses the same source port, it will be allowed.
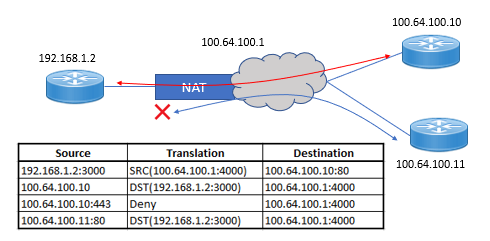
There are three hosts. One host is behind a NAT device. The NAT configured is port restricted full cone NAT. The internal host is initiating connections to the external host of 100.64.100.10. Let’s review the conversation:
- The internal host of 192.168.1.2:3000 initiates a connection to 100.64.100.10 with a destination port of 80.
- Because the internal host had previously connected to 100.64.100.10 on port 80, the external host is only allowed to initiate a connection to the internal host if it uses a source port of 80.
- In this example, the same external host that was allowed with a source port of 80 is trying to use a source port of 443. This is denied because the internal host has never connected to 100.64.100.10 on port 443.
- Here, another external host of 100.64.100.11 is trying to connect to the internal host. Since the internal host initially communicated to a destination on port 80, the second external host is allowed to communicate with the internal host as long as its source port is 80.
Below table describes the NAT type and Data plane status:





LEAVE A COMMENT
Please login here to comment.