EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USISE Authorization Policy Elements
ISE Authorization Policy elements is created by user-defined policy rules and provides two policy execution options:
First Matched Rule Policy Apply: It is the default, and works like FW ACL once the first rule is matched, processing of other rules are stopped.
Multiple Matched Rule Apply: ISE processes all rule and combines permission for all matched rules.
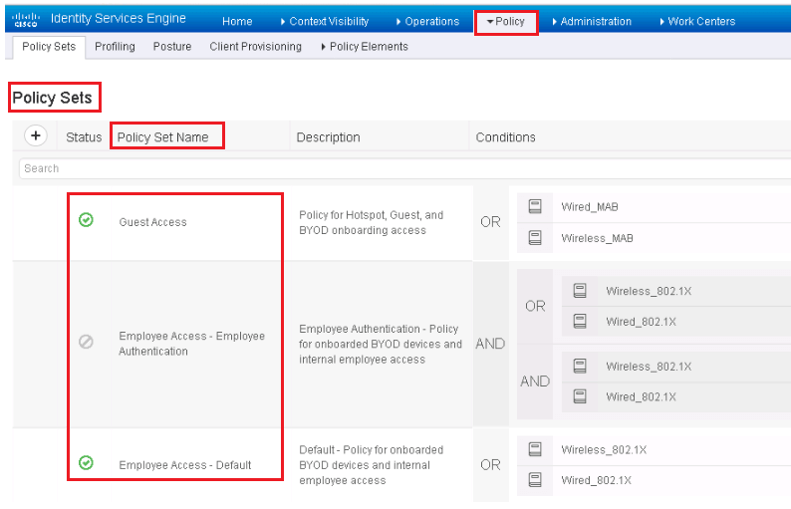
ISE Policy Set
With the Help of ISE policy set, an administrator can break up the authentication and authorization policies in multiple set based on Specific use case. When we combine all these policies we say it as Policy Set.
A Policy set can be combined to create full policy or can be used individually for any specific use case in Network Environment. Policy Set are disabled by default and is necessary to enable it by blow path.
Policy| Policy Sets
ISE Authorization Policy Types
There are three Policy types defined in ISE and each policy types has three section.
- Exceptions Section
- Standard policies section
- Rule section at Bottom.
Exception Policies: These are those policies that are evaluated first and if match is found all other standard and default policy are then not evaluated. This policy rule are used to override standard and default policy rules.
This Exception policy rules are used when there is need to make temporary change to ISE policy.
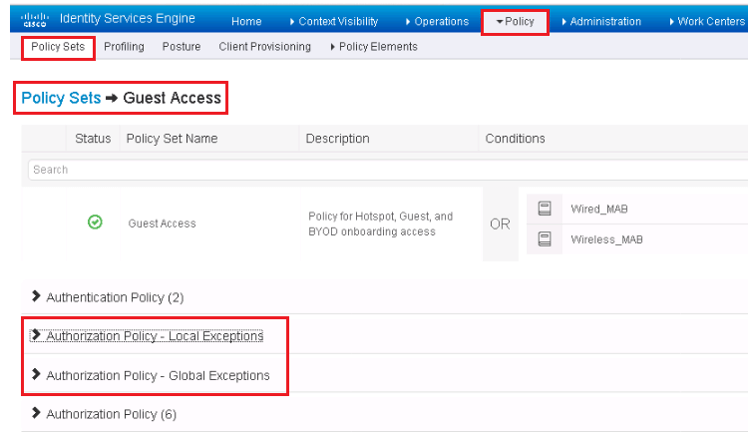
Standard Policy: These are regular policy rules and are used for ISE core functions
Default Rule: At every Authorization rule, default policy is present. If none of Exception and Standard policies are matched then default policy is executed to take certain action. This rule consist simple deny or permit access.
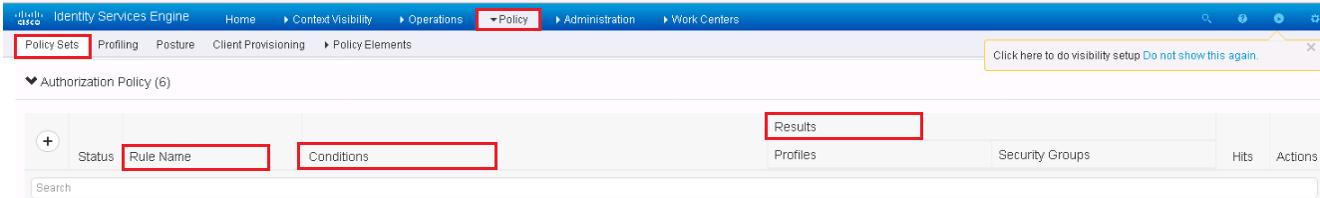
ISE Authorization policy rule are made by combining Policy Elements. Each Policy rule has atleast four Elements.
- Rule Status
- Rule Name
- Identity Groups
- Conditions & Permissions
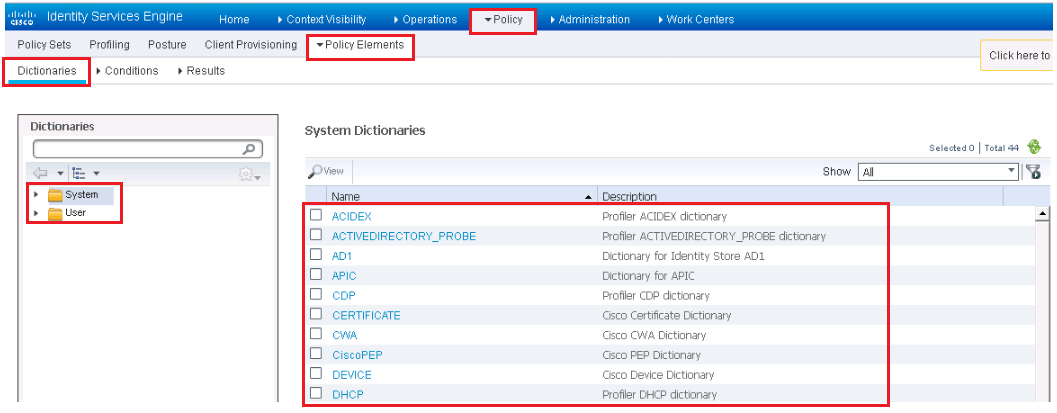
ISE Policy Elements are broken in to three groups.
Dictionaries: These are the objects used to define conditions, policies, profiles etc. These objects are used to categories external data that are received by (Syslog, SNMP Trap, RADIUS,) or ask for (Polling, AD query, RADIUS). ISE has more than 100 of predefined system dictionaries which are read only and cannot be created, deleted.
Conditions: Conditions defines a simple or compound expression which is to be matched against any data. A brief discussion of Conditions are mentioned in below sections.
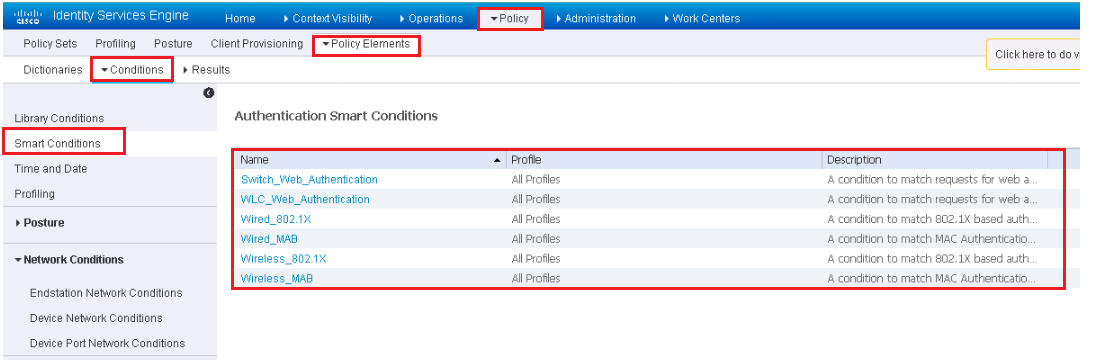
Results: Results defines a group of Network Control Access Privileges. These results are used to define and group authorization permissions. These results are further broken down in to two groups: Authorization Profile and Downloadable ACLs.
ISE Policy rule Conditions
Each ISE rule are defined by certain conditions and there are two type of IE Conditions.
Simple Condition: It consists of an operand (attributes), and operator (=, <,>, etc.) and a value. These simple rules can be saved and can be reused on other rule based policies.
Example: Device Type = Switch
Compound Condition: It consists of two or more Simple condition and are connected by AND or OR operator. These compound conditions can be saved and reused in other rule based policies.
Example = (Device Type = Switch) AND (AD Group = Employee)
Authorization Results
Whenever Authorization policy rule is matched, the Authorization results define what permissions are allowed. These results are further broken down in to two groups: Authorization Profile and Downloadable ACLs.
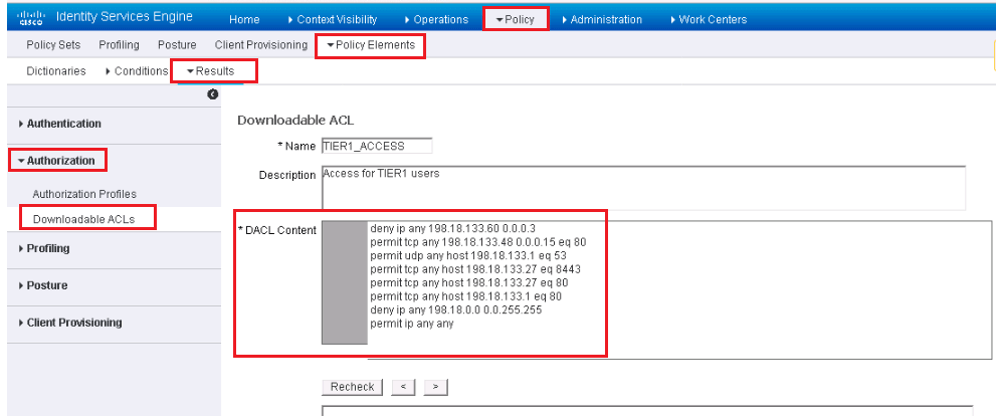
Downloadable ACLs: dACLs are ACLs that can be dynamically downloaded on-demand from ISE to Cisco Devices. Once these dACLs are configured on ISE, the dACLs then are added to an authorization profile. These dACLs consists of multiple ACE and have following attributes.
- Source and destination protocols
- Source and destination IP address
- Protocol source and destination ports
- Remark:
- Cisco syntax for a TCP ACL
- All ACL have an implicit denyat the end of them
To configure dACLs follow, below path:
Policy | Policy Elements | Results | Authorization | Downloadable ACLs and click Add
Authorization Profile: It consists of set of permission that are granted for any Network Access request. These profile attributes are delivered by RADIUS, this RADIUS code is configured in the profile along with one or more attributes-value pairs (AVP).
Some of the Common permission settings are Access_Accept/Access Reject, dACL name, Airespace ACL Name, VLAN, and Reauthentication timers.
To configure an authorization profile, go to Policy | Policy Elements | Results | Authorization | Authorization Profiles and click Add
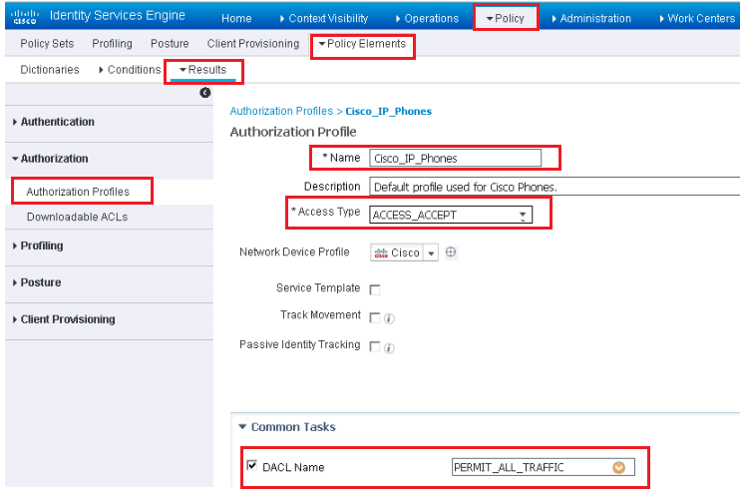
Below are some fields used for Authorization Profile
- Name
- Description
- Access-Type
- Service Template
- Track Movement
- Passive Identity Tracking
Final Section of Authorization Profile is common task , which contains collection of commonly used permissions, which are presented in plain-English but are converted in RADIUS attributes and AV pairs.




LEAVE A COMMENT
Please login here to comment.