EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USSD-WAN Viptela Templates
Cisco SD-WAN Viptela provides various types of templates that is used to configure various configuration parameters via one Go and without CLI.
Following are the Template Benefits:
- Scalable: you don't need to enter all the configuration commands needed for each device.
- Used in Zero Touch Provisioning (ZTP) the device pulls the configuration from the template, allowing you to commission a device without accessing the console port.
- Designing templates for a location such as campus, branch, home office, or data center, and all you have to do is to add site-specific values to the csv file that gets imported in the template to build the device configuration.
- Controlled deployment and Single source of truth
Template Planning:
Before creating templates plan on the following
- Identify the device
- Chassis number of the device
- Identify the number of interfaces active
- Circuit (transport) connections
- Plan for an IP addressing scheme
- Site id
- Hostnames
Configuration Elements in a Device
Following are the parameter that is required to configure any device, as defined in below figure and these all parameter can also be configured by various Templates on vManage.
VManage: Types of Templates
Device templates are similar to configuration groups, and they contain a complete operational configuration for a device. Device templates are supported both on Viptela OS and IOS XE based devices. You can create device templates by consolidating individual feature templates. With feature templates, each individual feature is configured within its own template and each feature template can be used by multiple device templates. This differs from feature profiles used in configuration groups, where the individual features are grouped into a feature profile and each feature profile, along with all individual features, can be used in multiple configuration groups.
Each device template is specific for a type of device. For each device type, if multiple devices have the same configuration, you can use the same device template for them. For example, many network routers might have the same basic configuration, so you can configure them with the same templates. You specify the differences in the templates using configuration variables. If the configurations for the same type of devices are different, you create separate device templates.
You can also create a device template by entering a CLI text-style configuration directly in Cisco vManage. Typically, you upload a text file containing the configuration text (or cut the configuration text from a text file and paste it into Cisco vManage). You can also directly type the configuration text into Cisco vManage.
Templates exist on two basic levels:
- Device template
- Feature template
Device Template:
Device template are those specific to vEdge Model, but it can also be possible to create multiple Device template for same model due to location and function in network. Each device template can contain a number of feature template. This Device template cannot be shared between other vEdge Models, whereas Feature template can be shared across several models.
Device templates are described as follows:
-
Device templates define the complete operational configuration of a device.
-
They can reference several feature templates.
-
They are model-specific (device type).
-
No device templates are defined in a new installation, by default.
A device template consists of several feature templates. Each feature template defines the configuration for a particular Cisco SD-WAN software feature. Some feature templates are mandatory, indicated with an asterisk (*), and some are optional. Each mandatory feature template, and some of the optional ones, have a factory default template. For software features that have a factory default template, you can use either the factory default template (named Factory_Default_feature-name_Template) or you can create a custom feature template. You can define templates in Cisco vManage GUI under Configuration > Templates. No device templates are defined in a new installation by default.
Feature template:
Within a feature template, some configuration commands and command options are identical across all device types. Others—such as a device system IP address, its geographic latitude and longitude, the time zone, and the overlay network site identifier—are variables that change from device to device. When you attach the device template to a device, you are prompted to enter actual values for these command variables. You can either enter the values manually, by typing the values for each variable and for each device, or you can upload an Excel file in CSV format that contains the values for each device.It represents the configuration related to particular feature like System, VPN, Interface, OSPF, etc.
The roles of feature templates and how they are used:
-
Feature templates represent individual building blocks of the configuration.
-
Feature templates are device model-specific.
-
Feature templates are attached to devices by using device templates.
Device Template & Feature Template Configuration Sections
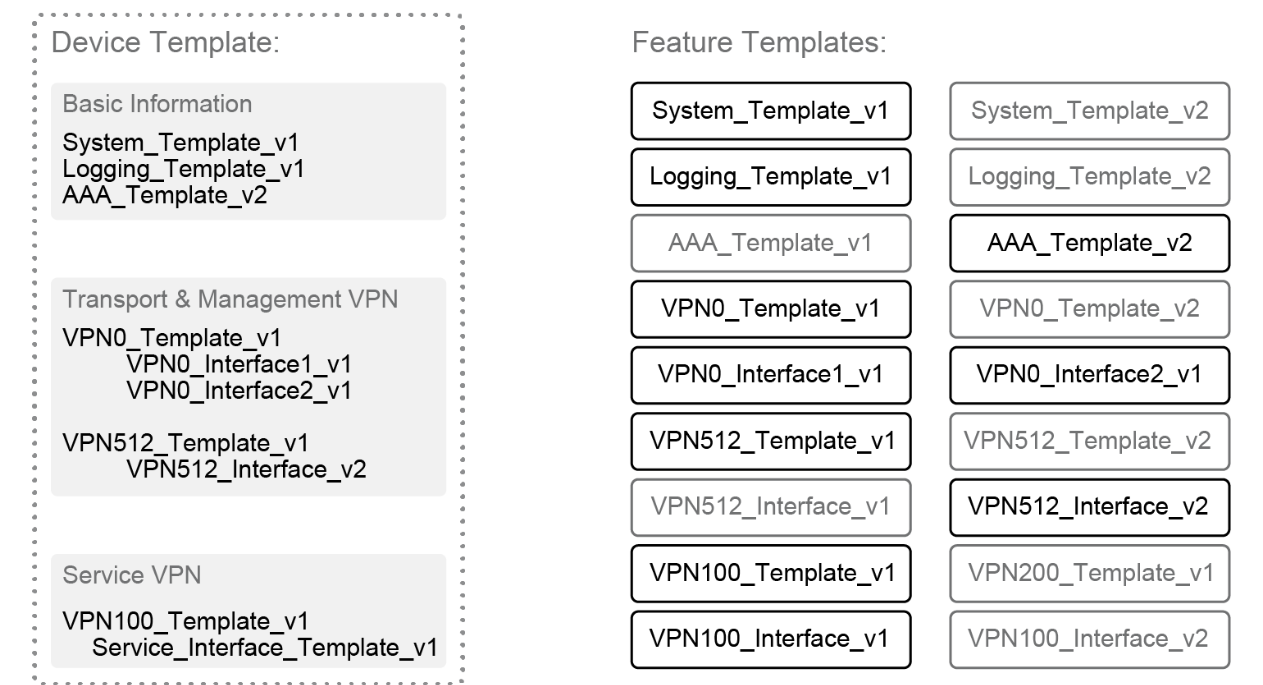
Below figure gives over all view of Device template components, a device template is made up of feature template grouped in to following Sections:
- Basic information – It includes system, logging, AAA, OMP, BFD, security, archive, and NTP feature templates.
- Transport and management VPN – It includes the templates used to configure VPN 0 and VPN 512, which includes BGP, OSPF, VPN interface, VPN interface cellular, VPN interface GRE, and VPN interface PPP feature templates.
- Service VPN – It includes the templates used to configure the service VPNs, which contains the BGP, IGMP, Multicast, OSPF, PIM, VPN interface, VPN interface bridge, VPN interface GRE, VPN interface IPSec, VPN interface Natpool, and DHCP server feature templates.
- Additional templates - it includes banner, Simple Network Management Protocol (SNMP), bridge, localized policy, and cellular feature templates.
Following are some Feature Template description:
- System - Configure basic system information, such as site ID, system IP, time zone, hostname, device groups, GPS coordinates, port hopping, and port offset.
- Logging - Configure logging to disk and/or to a remote logging server.
- AAA - Specify the authentication method and order and configure Radius, TACACs, or local authentication, including local user groups with different read/write permissions.
- BFD - Specify the BFD app-route multiplier and poll interval and specify the hello and BFD multiplier for each transport.
- OMP - Change the graceful restart timers and advertisement timers and hold timers; change the number of paths advertised; configure an AS overlay number; choose which local protocols will be advertised into OMP; and change the number of equal-cost paths installed in the vEdge router.
- Security - Change the rekey time, anti-replay window, and authentication types for IPSec.
- Archive (optional) - Archive the full running configuration onto a file server within a time period specified.
- NTP (optional) - Configure NTP servers and authentication if required.
- VPN - Change the ECMP hash, add DNS servers, advertise protocols (BGP, static, connected, OSPF external) from the VPN into OMP, and add IPv4 or v6 static routes, service routes, and GRE routes.
- BGP (optional) - Configure the AS number, router ID, distance, maximum paths, neighbors, redistribution of protocols into BGP, hold time, and keepalive timers.
- OSPF (optional) - Configure router ID, distance, areas, OSPF interfaces, reference bandwidth, default information originate, metrics, metric type, and SPF timers.
- VPN Interface configuration - Configure an interface name, the status of the interface, static or dynamic IPv4 and v6 addressing, DHCP helper, NAT, VRRP, shaping, QoS, ingress/egress Access Control List (ACL) for IPv4 and 6, policing, static Address Resolution Protocol (ARP), 802.1x, duplex, MAC address, IP Maximum Transmission Unit (MTU), Transmission Control Protocol Maximum Segment Size (TCP MSS), TLOC extension, and more. In the case of the transport VPN, configure tunnel, transport color, allowed protocols for the interface, encapsulation, preference, weight, and more.
- VPN interface bridge (optional) - Configure layer 3 characteristics of a bridge interface, including IPv4 address, DHCP helper, ACLs, VRRP, MTU, and TCP MSS.
- DHCP server (optional) - Configure DHCP server characteristics
- Banner (optional) - Configure the login banner or message-of-the-day banner.
- Policy (optional) - Attach a localized policy.
- SNMP (optional) - Configure SNMP parameters, including SNMP device name and location, SNMP version, views, and communities, and trap groups.
- Bridge (optional) - Define layer 2 characteristics of a bridge, including the VLAN ID, MAC address aging, maximum MAC addresses, and physical interfaces for the bridge.
- Routing protocol templates, such as BGP or OSPF, and VPN interface templates are configured under a VPN. DHCP server feature templates are configured under a VPN interface.

Comment
-
AU
The course helped me upgrade my skills and knowledge regarding in-depth networking. The software-defined wide area network has given me the confidence in designing, installing, arranging, and managing SD-WAN solutions in wide networks in a very short period of time. I would recommend this to everyone who wants to excel in their networking career.
-
MA
After the successful completion of the course, I was able to build a lab at home from scratch with all the necessary steps. The training is very detailed, I was able to set up the controllers, and I received step-by-step instructions to configure ntp and sync all controllers with a ca server to be able to install certs. thank you.




LEAVE A COMMENT
Please login here to comment.