AAA Authentication Function
When any device sends an authentication request to AAA, TACACS+ Protocols works behind and ensure the Authentication, Authorization and Accounting functions for that device. Below figure define how TACACS+ perform authenticate once and authorize many function like access to Router CLI, Command sequence used on that device, etc.
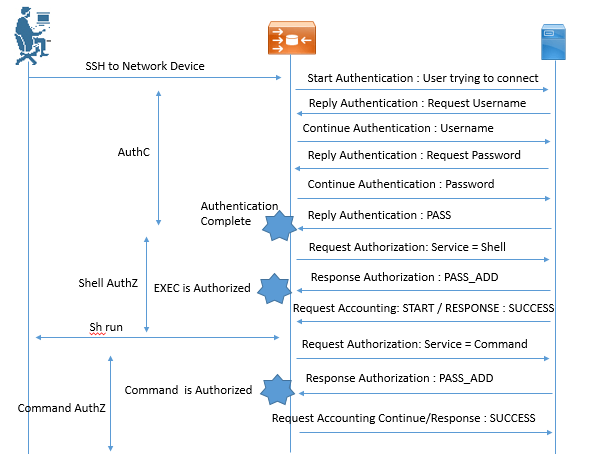
Device Administration in ISE
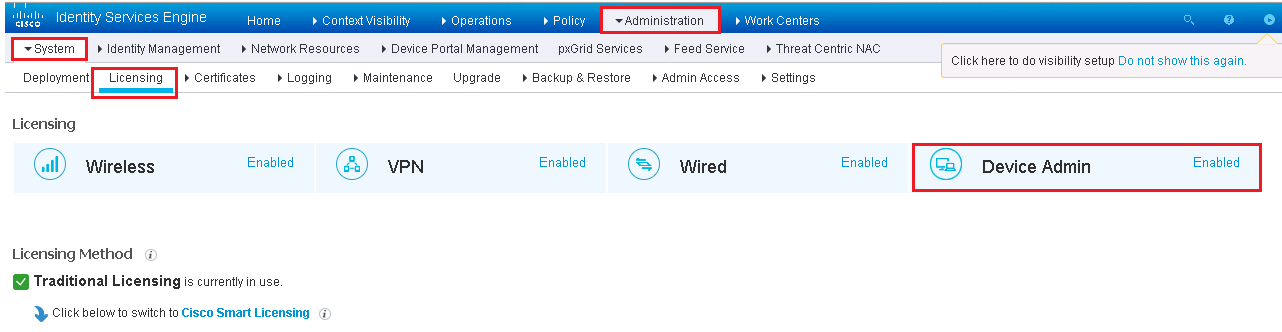
TO enable TACACS+ on ISE, we need a single license called Device Admin, It is a single license that is applied to entire ISE cube and is valid for maximum number of Network Device.
Below figure show device Admin license is enabled.
In order to learn the deployment model of TACACS+, below list shows which model is best for your organization.
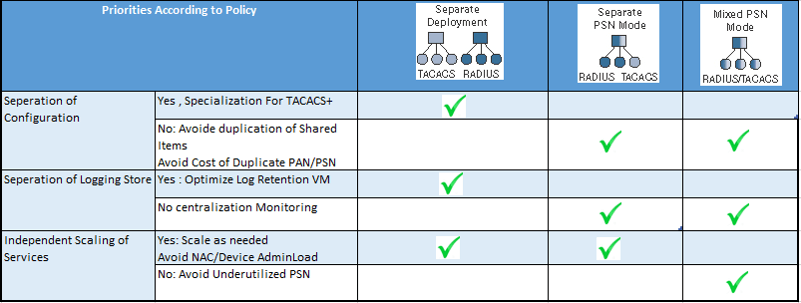
Now here we will see how these deployment are done and what are the ISE architecture related to those environment.
Large Deployment
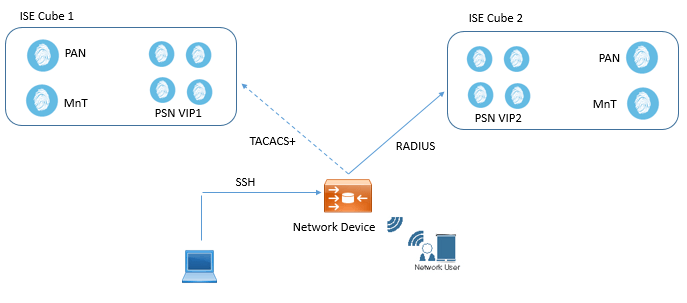
In Large Deployment, It is best to use different ISE cubes for Network Access and Device Administration.
Below figure shows two different ISE cubes, Cube 1 is used for TACACS+ and Cube 2 is used for RADIUS. PAN and MnT are also used as dedicated.
Medium Deployment
In Medium deployment, you should use only one ISE cube with two dedicated PSNs for network access and Device administration. Here one set of PSN will be responsible for RADIUS traffic and other will be used for TACACS+. In case of disaster you can choose to send the RADIUS traffic to PSN handling TACACS+ or vice versa.
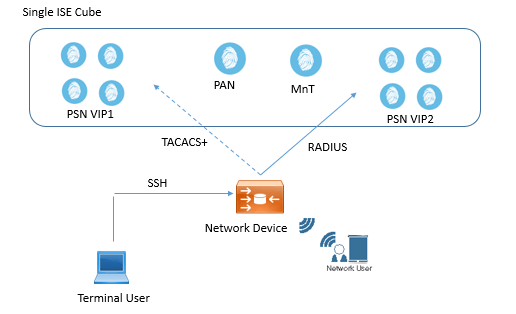
Small Deployment
In this type of deployment, single small cube is used, or you can also use one single standard ISE that will perform all functions. In this all PSN will handle all type of traffic (TACACS+ and RADIUS).
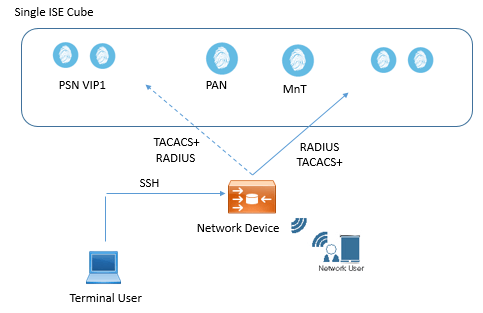
How to Enable TACACS+ in ISE
In order to enable TACACS+ in ISE, you must have device Administration License. Now below are the steps used to enable TACACS+ in ISE.

GENERAL FAQ
Cisco ISE device administration oversees who can access network devices such as routers, switches, and firewalls. It utilizes the TACACS+ protocol and provides all three: authentication, authorization, and accounting, which helps to manage who can reach the appliance for administrative purposes.
TACACS+ serves as the foundation for setting up device administration in ISE. When someone connects to a device, TACACS+ checks who they are (authentication), confirms the person has permission to do what’s requested (authorization), and logs what they’ve done (accounting). It lets only the right people change your network devices.
Yes. To use TACACS+ for device administration, the Device Administration License is required. It is one license that you apply to all your ISE deployments, and it accounts for all your network devices.
The most common deployment models are as follows:
• Big Deploy: Utilizes two ISE nodes (cubes) for TACACS+ device admin and RADIUS network access.
• Medium Deployment: It will require to use of one cube with dedicated PSNs for every function.
• Small Deployment: Everything TACACS+ and RADIUS runs on a single ISE cube or node.
The best option for you will depend on your network size and redundancy requirements. TACACS+ and RADIUS can be deployed as standalone deployments or as a cohesive deployment serving both protocols. Whether you dedicate a separate instance of each is more of a security and operational policy decision. If your current separation of deployments is serving you well, continue with them separated.
Yes, you can. In small to mid-sized environments, a single ISE cube can handle both RADIUS and TACACS+ traffic. For larger deployments, it’s better to separate them into dedicated setups to improve scalability and performance.
Once you add the Device Administration License, you will be able to enable TACACS+ from your ISE setup. It requires that you enable TACACS+ services, and then define your network devices, and possibly policies to limit who can access and do what commands.











LEAVE A COMMENT
Please login here to comment.