EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USvEdge Router as NAT Device
A vEdge router can also be used as NAT device on both transport and service side of network. Let’s see and understand how vEdge routers work if we configure NAT on transport or on Service side individually.
NAT on vEdge Router on Transport Side:
In order to provide internet resources access from local site, NAT is configured on Transport side performing both address and port translation (NAPT).
Let’s see the below figure and understand the concepts and how it works
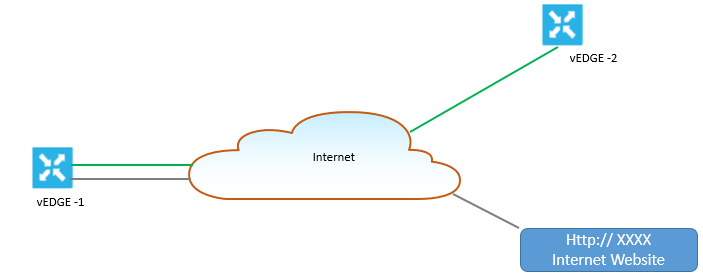
Here vEdge router is configured NAT, so vEdge router will split its traffic in to two ways or think as separate tunnel. Green Traffic will use overlay network and will traverse from one vEdge to another vEdge via usual Ipsec tunnel whereas grey traffic is redirected to vEdge NAT device and then out to public network.
NAT on vEdge router perform both address translation and Port translation, and it establish a translation entry between private address and port with Public IP address and Port. Once this is done, NAT device will allow incoming connection from external host to be established with that private address and port only if that private address and port already established a connection to the external host.
Viptela NAT software supports 64000 NAT flows.
Example:
To understand this lets see the dig.
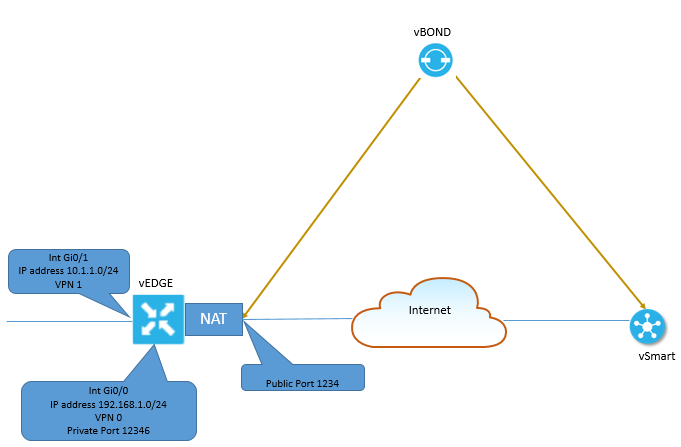
vEdge router splits traffic into two flows, one will go to Overlay network and another will go to public network.





LEAVE A COMMENT
Please login here to comment.