EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USConfigure Strict Hub and Spoke Topology
Task: Configure the Topology to work like Strict Hub and Spoke based network where there are three Subnet for each VPN.
- VPN 10: Corp-VPN
- VPN 20: Sec-PCIVPN
- VPN 40: Guest-VPN
Topology should work like follows:
- For all VPN 10 : All Branch VPN 10 traffic must go to DC and then to Branch and VPN 10 traffic must not go Branch to Branch , All DC must send a default route to each branch for outside traffic.
- For VPN 20: Each Branch must have VPN 20 routes for other branch having Next HOP: DC-TLOC
- For VPN 40: No direct communication between branch to branch to any VPN, This VPN should have default route to access Internet only
Topology:
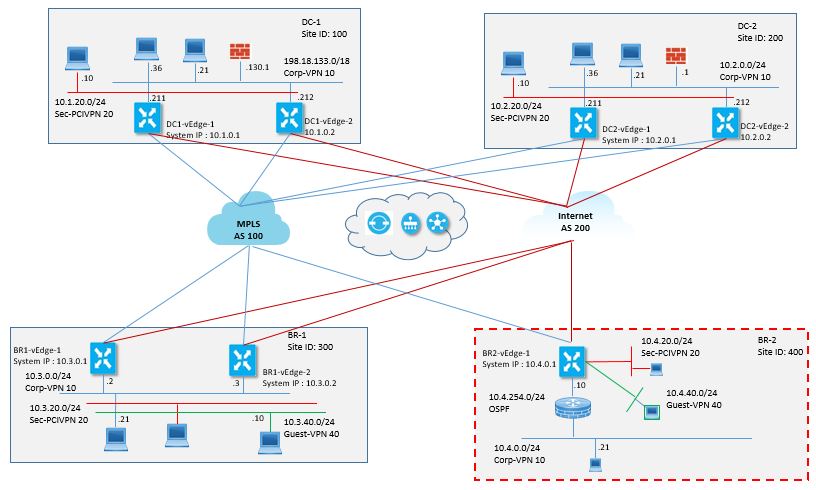
Solution:
For VPN 10 : Advertise branches routes to DC and not to another branch , DC will advertise default route to each branch so that if branch wants to talk to another branch , branch will send the traffic to DC by default route and DC will then route traffic back to remote branch
For VPN 20 : Branch will advertise VPN 20 routes to vSmart and in return vSmart will advertise those VPN 20 routes by setting Next hop as DC-TLOC , so in branch to branch communication via VPN 20 , Branch will send traffic to DC and DC will route it to branch.
For VPN 40 : No communication between branch , so restrict routes exchange between them ,and advertise only default routes in VPN 40 for direct internet access.
Before configuring Hub and spoke topology, let’s verify that all the branches are able to reach to other branches directly over VPN 10 and VPN 20 over IPSEC tunnel.
vManage | Monitor | Network | Select BR2-VEDGE1 | Tunnel
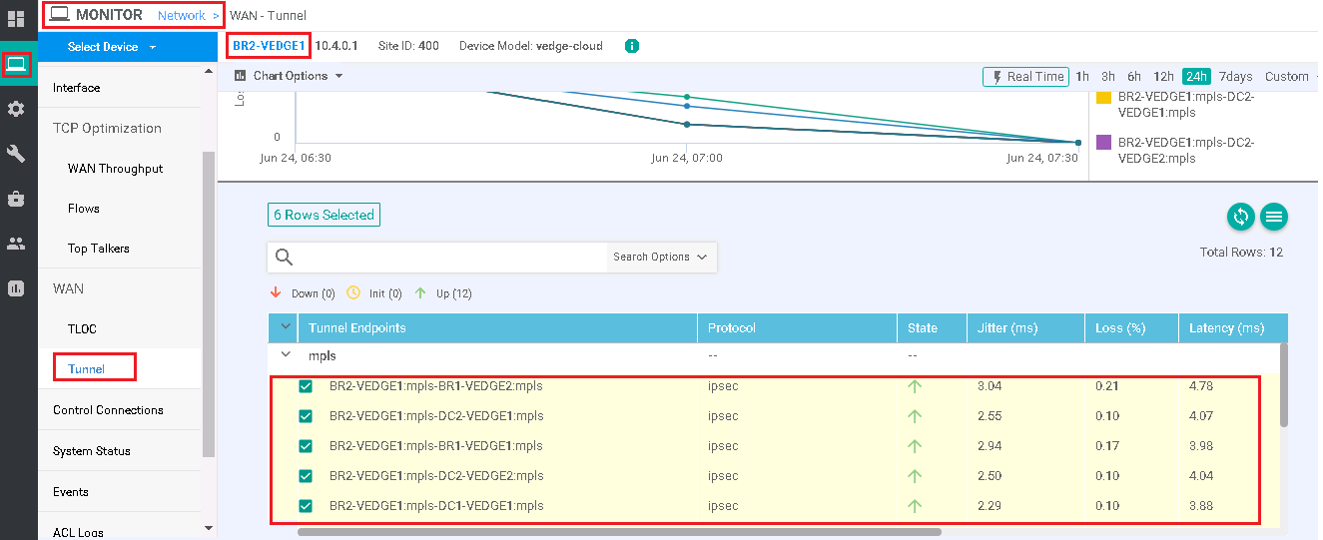
This will show that the BR2-VEDGE has full Mesh IPSEC tunnel to all other branches and DC sites.
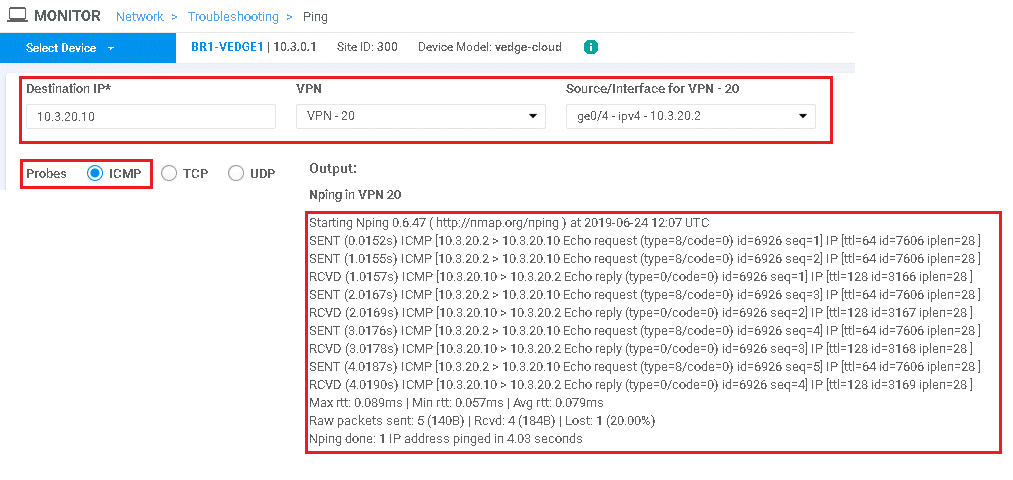
Select Troubleshooting | PING | under connectivity Section
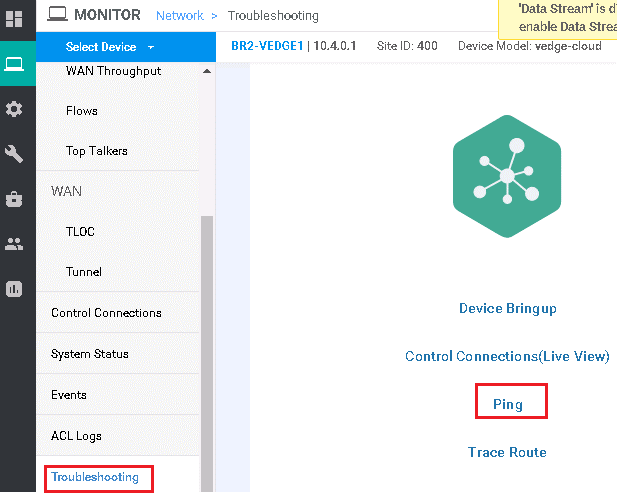
Select destination IP: 10.3.0.21 (Branch 1), VPN 10 and Source Interface in VPN 10 | Start
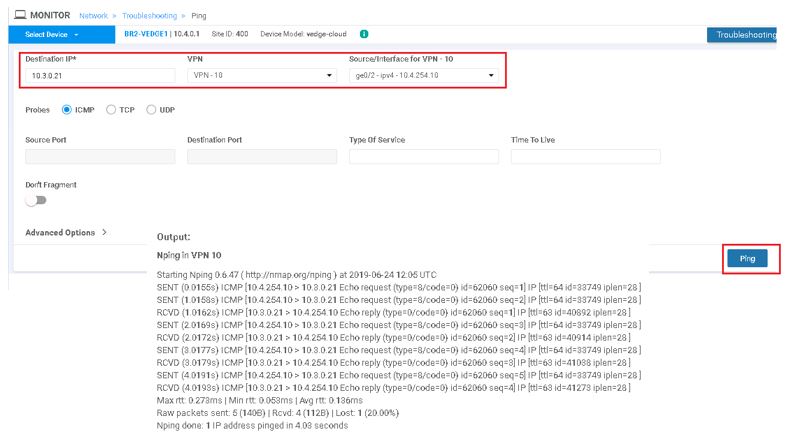
So same activity for VPN 20
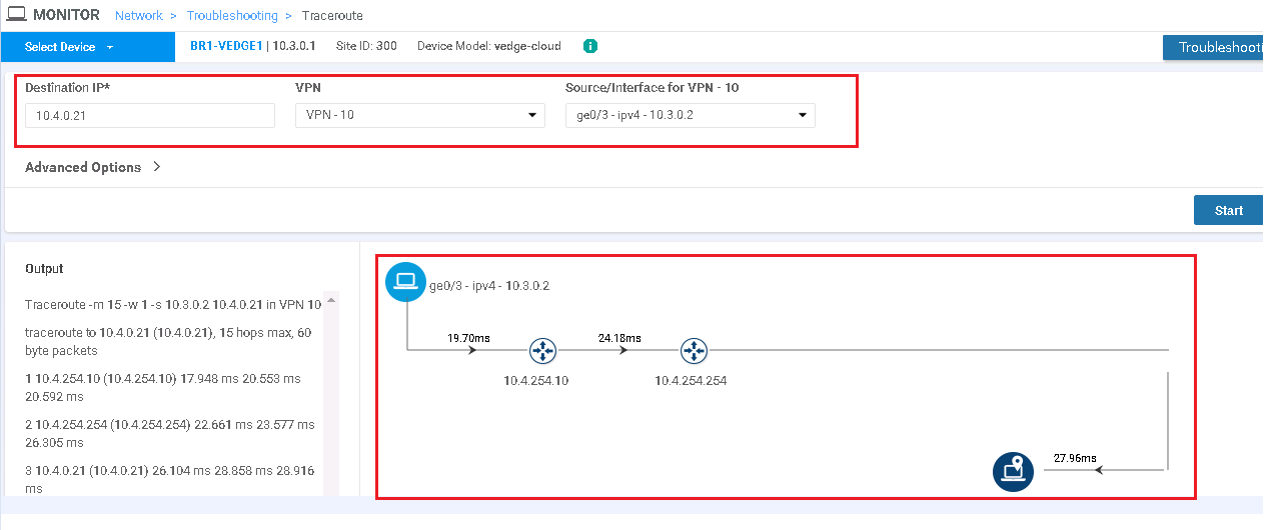
For VPN 10 Select | trace Route | destination IP 10.4.0.21 | VPN 10 | Select Source Interface | Start
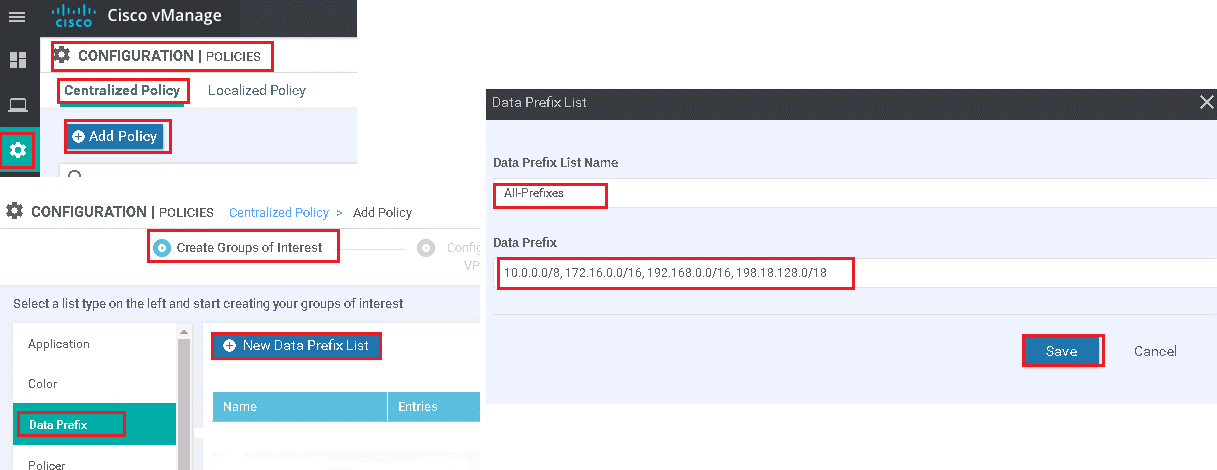
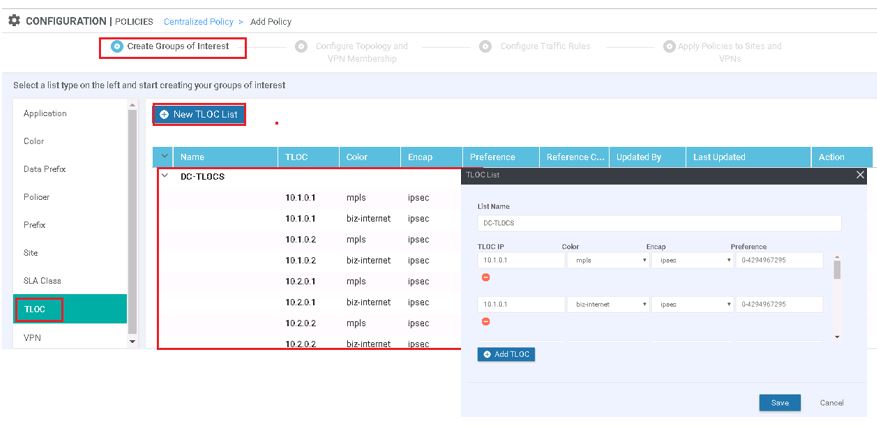
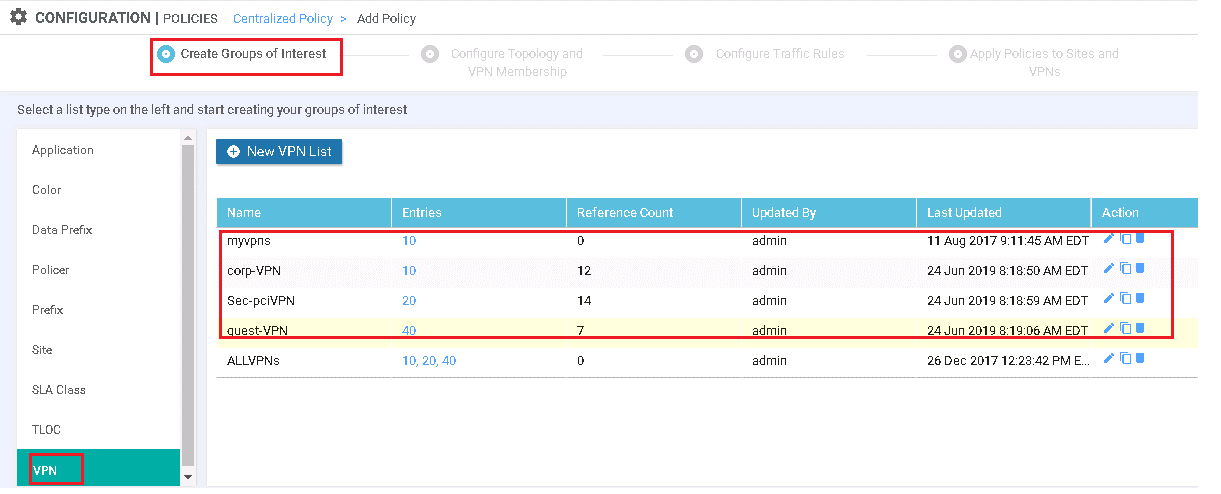
Now Create Application or Groups of interest for all components like DC, Sites, DC-TLOC, Data-Prefix Group.
vManage | Configuration | Policies | centralized Policy | Add Policy
Data-Prefix Group: Contains all RFC1918 Prefixes and all other prefixes known for this Topology
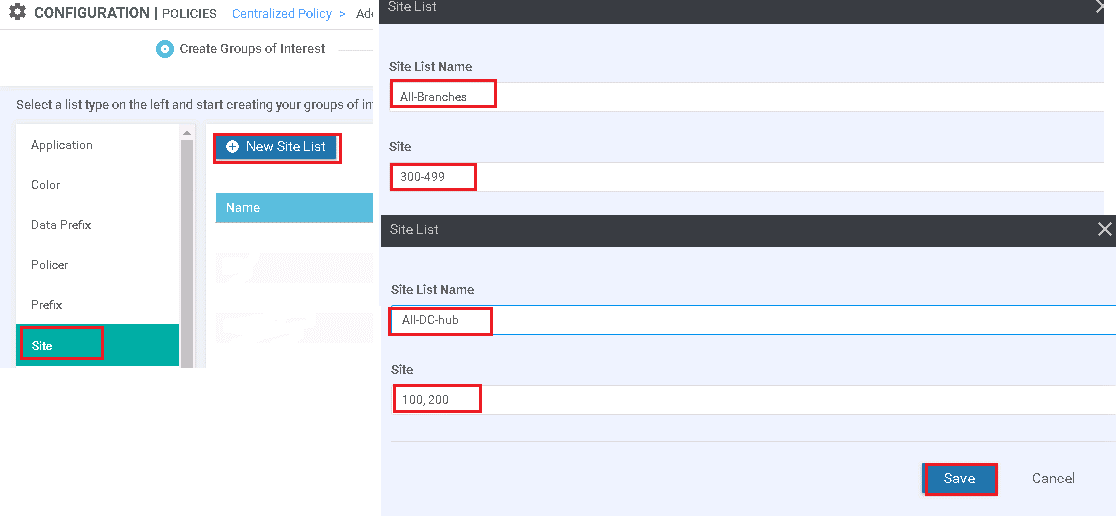
Site Group: Contains All-Branch List, All-DC-hub list Site IDs.
DC-TLOC: Contains all TLOC from two DC vEdge Devices
VPN-Group: contains all VPN group for VPN 10 (Corp-VPN), VPN 20 (Sec-PCIVPN), and VPN 40 (Guest-VPN).
Click Next to move to Configure Topology and VPN Membership Section, here we will configure Custom Control Topology, this topology allow to manipulate OMP and TLOC routes on vSmart.
Click on Add topology | Custom Control (Route & TLOC)

Comment
-
DA
DClesson’s configure strict hub and spoke topology is the best online study material available. They have explained everything in detail and with relevant diagrams and sketches.
-
BA
This is a step-by-step guide to configuring strict hub and spoke topology that helped me configure creative and powerful networking solutions in the cloud for the following common use cases. This topology can require the configuration and maintenance of many virtual circuits.




LEAVE A COMMENT
Please login here to comment.