EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USTrustSec
VLAN assignment and dACL are two important parameters used to control access to network, buts its size grows expontiently when network expends and there are large requirement of network access.
As network grows, it very difficult to manages them, as their size increase very large as per below formula for ACEs.
(# of sources) × (# of destinations) × permissions = # of ACEs
Let say I have 1 Source and 6 destination and if we require 4 permission then total number of ACE require would be:
1 source × 6 destinations × 4 permissions = 24 ACEs
So Implementation and later management of these ACE is very complex task. To overcome these challenges, TrustSec was developed.
TrustSec is next generation access control enforcement, developed to address the issue of above challenges of ACE increase.
TrustSec assign a tag called Security Group tag or SGT, to user/device’s traffic at ingress, and then enforce the access everywhere in infrastructure.
Example: Guest user is assigned SGT so that it can isolated to non-Guest Traffic throughout infrastructure.
Below are some common SGT groups provided by ISE.
- Network Infrastructure:SGT assigned to all the switches, routers, WLCs, and firewalls within the organization.
- Network Services:SGT is assigned common services servers like (DNS, DHCP, NTP, and so on).
- Executive:To classify executives’ traffic and simply to ensure that executives will never be denied access to anything.
- Sales:SGT assigned to sales traffic of organization.
- Finance:SGT assigned to Finance traffic of organization
- HR:SGT assigned to HR traffic of organization.
- Line-of-Business-1:SGTs are used for different lines of business, and those lines of business cannot have access to each other’s data.
Security Group tags
It is 16 bit value that ISE assigns to users or endpoint session upon login. Network infrastructure see these SGT as an attributes and put this information as Layer 2 tag in to all traffic for that particular session.
Defining SGT’s:
ISE acts as SGT controller, and has dedicated work center related to TrustSec. ISE comes with large number of predefined SGT’s with assigned icons as shown below.
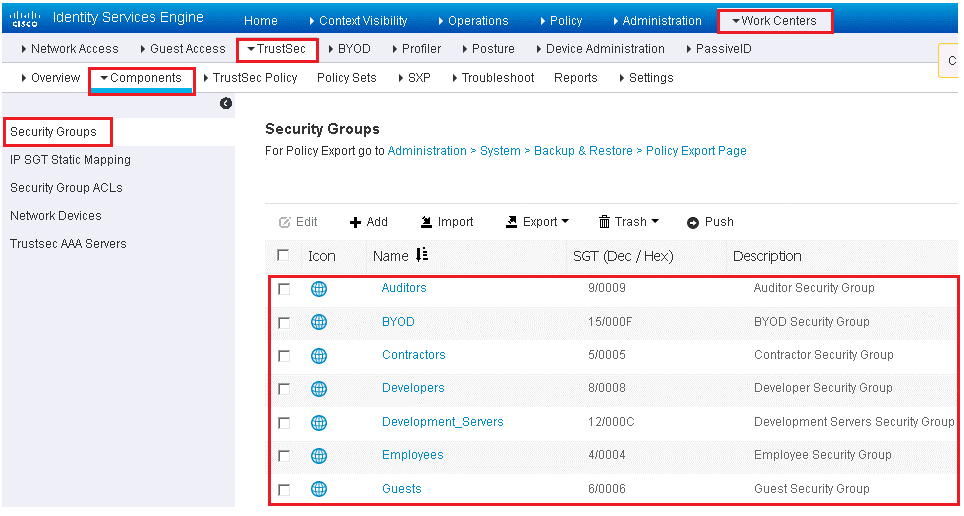
To view these SGT, follow below path: Work Centers | TrustSec, with this path you can also cre ate your own SGT’s. Here notice that one default SGT, Unknown with value 0. This SGT will be used when a traffic arrives and has no SGT tags.
Classification
It is a process classifying any traffic and assigning a SGT. All Supported Cisco Switches and wireless Controllers supports assignment of SGT.
Transport: The Process of communicating the assigned SGT to upstream Network Infrastructure via Native tagging or via Peering Protocols is called Transport.
Below Example shows one access switch that has native tagging, and packets gets tags on uplink port. There is also a non-native tagging switch, which is using a peering protocol to update the Tags to its upstream switch. In both cases, upstream switch continues to tag traffic throughout the infrastructure.
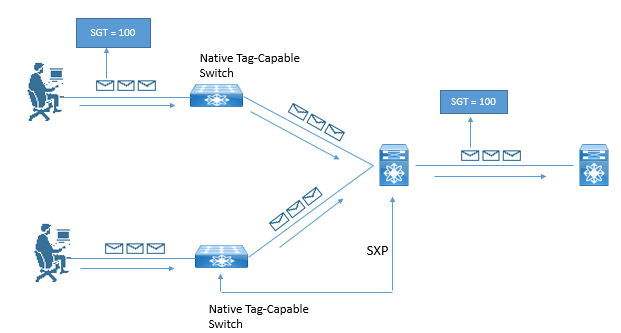
There are following ways to assign the tags.
- SGT can be assigned dynamically, and be downloaded as the result of an ISE authorization
- It can be assigned manually at the port level
- It can be mapped to IP addresses and downloaded to SGT-capable devices.
Now we will see each method one by one:
Dynamically Assigning SGT via 802.1X
ISE has some preconfigured example of TAG assignment. You can use below link to see these:
Work Centers | Network Access | Policy Sets | Default | Authorization
Below are the steps to add Security Group tag as an authorization result:
Step 1. Click Edit to edit your existing authorization rule.
Step 2. Click the + sign under Permissions.
Step 3. Click the + sign next to the authorization profile.
Step 4. Choose Security Group.
Step 5. Select the appropriate Security Group to apply.





LEAVE A COMMENT
Please login here to comment.