EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USAuthentication between vSmart & vBond
The first two devices that starts validation and authentication to each other are vSmart and vBond over Viptela Overlay network. This Validation and authentication is initiated by vSmart controller.
When you begin to Provision the vSmart, you will add the DNS name of vBond orchestrator or IP address of vBond. When vSmart controller send request to vBond, vBond is primed to reply because:
- vBond is aware that its role is to authenticate system , as this information is included in vBond configuration
- The vSmart serial number is download from vManage and provided to vBond orchestrator
If vBond is not started, vSmart will send the authentication request periodically until authentication is successful.
VSmart controller initiates the encrypted DTLS connection to vBond, this encryption is provided by RSA and each device automatically generates RSA public and Private Key when it boots.
Over this secure channel, vSmart controller and vBond authenticates each other, so to start with let’s see with vSmart controller authentication of the vBond orchestrator.
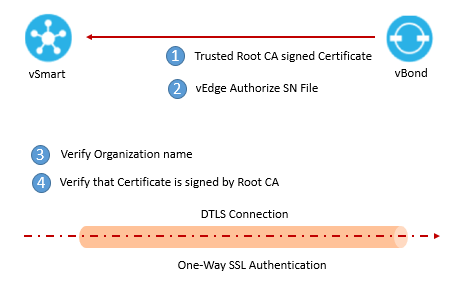
- vBond send the trusted root CA signed certificate to the vSmart controller
- vBond also sends the vEdge authorized serial number file to vSmart Controller.
- vSmart extract the organization name from certificate and its compares with its own organization name configured on it. If the match is not correct vSmart will tear down the DTLS connection
- If it matches , then it will use the root CA chain to verify certificate , if Certificate signature is correct vSmart confirm that certificate is valid and if signature is not correct vSmart will tear down the connection
Once these checks are performed, vSmart confirm the authentication of vBond orchestrator and is complete





LEAVE A COMMENT
Please login here to comment.