EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USCisco ISE NACP Components
ISE NACP consist of various different policies, when combined provides a context aware network access to an Enterprise. Below are the list of policies that are used in ISE NACP.
Authentication Policy: This Policy verifies the users or Devices Identity and also provides Unauthenticated Guest Access.
Authorization Policy: This policy provides user or device what they are authorized to do in Network and this policy is enforced when a rule is matched. Example: BYOD policy
Host Posture Assessment Policy: This policy collects information about user or device and based on that a particular security level or security rules or Security action is provided to that user or device. ISE can also be integrated with third party Mobile Device Management (MDM) to collect information about mobile devices such as iPhones or iPads.
Device Profiling Policy: This policy is set based on type of device accessing to Network. It is an agentless solution, which tracks the device behavior on network passively and determine the type of device. Example: If an iPhone or iPad is connected to network do not allow them to connect or access Datacenter Network.
Enterprise Common Network Access Security Goals:
When you are deploying ISE Solution, below are Goals that needs to be addresses.
- Need to enforce a consistent Context based dynamic Segmentation Security Policy across whole Network Infrastructure.
- There are need to get full visibility about devices connected to wired or Wireless network. (Who, What, How, Where).
- Need to Protect internal and External Network from unauthorized access
- Proper Authentication of all users who have access to network or want to access wired or wireless network.
- Proper Authorization is to be done for all users or devices that want network access.
- Once Network Authorization is done, Need to Assign TrustSec SGT to all Wired or Wireless and VPN users.
- Based on user and device attribute, risk, profile and role, need to provide differentiated network access.
- All Non Guest Mobile devices must be registered or enrolled in corporate mobile device management System.
- All workstations, and Macs must run an approved antimalware and there Personal FW should be up to date.
- All Non Guest Machine must run an approved software version or OS and should be up to date.
- All those device who are running banned OS and Software APP, must be denied network Access.
- All Guest Devices traffic must be segmented based on what is to be accessed.
- Any users or device when on compromised state , must be alerted or Quarantined on network
Some of the Enterprise prefer to deploy ISE solution gradually and want to enforce security policies incrementally. Below are list of best practices of Policy Enforcement Phases.
- Deploy Wireless Guest User security policy in Wireless Enterprise Infrastructure.
- Deploy Wireless Authentication and its authorization access control policies.
- Deploy policies which provides visibility profile of users and devices for Wired or Wireless network
- Deploy Mobile Device Provisioning and its enroll procedure in to MDM System.
- Deploy wired 802.1X and MAC Authentication Bypass (MAB) for AAA in Monitor mode.
- Deploy Wired 802.1X for AAA in Low Impact Mode and then Closed mode.
Decision Matrix for NASP
Below figure describes the correct and exact Network Access Security policy that is enforced for any given user.
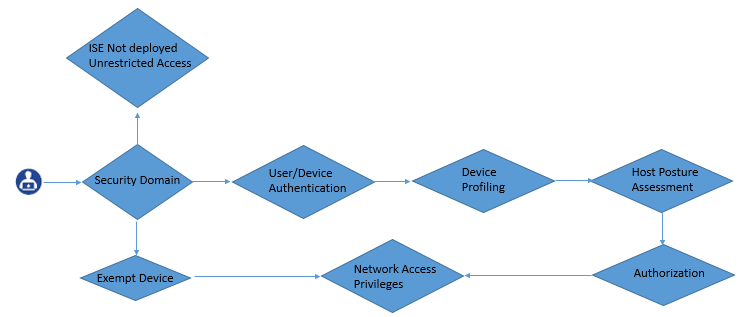
Security Domains
Security domains are those group of things or object that requires common risk profile under a common Network Access Security Policy. Below are some example of Security domains:
- Remote Access
- OOB Management
- Internet Access
- Guest Access
- Wired User and Network
- Wireless User and Network.
ISE Authorization Rules
These rules defines what a user or device would be able to perform activity or would be able access the network. These rule are evaluated from top to down and upon match the rule evaluation is stopped.
Below are some common permission that is controlled by authorization rules:
- Access Type (Accept or Reject)
- For a Client Traffic, apply a TrustSec SGT.
- Downloadable ACLs
- Assignment ACL
- To Wireless Client Traffic, Assign ACL in Cisco WLC
- Permission to Voice Domain
- Initiate Web Authentication
- Execute Switch Auto Smartports Macro
- Apply an Interface Template
- Periodically assess host vulnerabilities
- Filter-ID—Sends ACL via RADIUS filter attribute
- Reauthentication—Decide if you want to maintain connectivity during reauthentication
- MACsec Policy—Sets 802.1ae link-by-link encryption
- Network Edge Authentication Topology (NEAT) Which allows you to authenticate network devices (such as switches) to other network devices via 802.1X
- ASA VPN attributes
- Client posture assessment
- Network Scanner—NMAP
- Acceptable Use Policy
Rules Consideration for Host Security Posture Assessment
In this we will learn the criteria, how to include host posture in to enterprise Network Access Security Policy Document.
In this ISE uses Cisco any connect Posture Agent which are of two types:
- Temporary Agent
- Full agent
Temporary Agent can be installed directly on to Client via Browser and does not have rights to perform remediation action for user, whereas Full agent is loaded to device and offers remediation for device that fails security test like Antivirus software not up to date. Some remediation task are file distribution, Link distribution, auto-update rule for antivirus, antispyware, windows OS patches , and client FW rule.
These all posture assessment and remediation configuration is done using ISE GUI.
Below are the rules and requirement structure in ISE.





LEAVE A COMMENT
Please login here to comment.