EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USAmazon Virtual Private Cloud
Amazon VPC allows us to create our own virtual private network within AWS in following ways
- Help in selecting own private IP subnet space
- Configuring Routing tables
- Network gateway
- Security policies
In a region, multiple VPC can be created and they are logically isolated even if they share IP address Space. Once any address space is assigned it cannot be changes after VPC is created.
There are two types of Network Platform available within AWS.
- EC2-Classic
- EC2 VPC
EC2-Classic was originally launched with a single, flat network shared between another AWS customers.
Below figure describes Amazon VPC, with address space of 10.0.0.0/16 with two different subnets 10.1.1.0/24 and 10.1.2.0/24 placed in different availability zone.
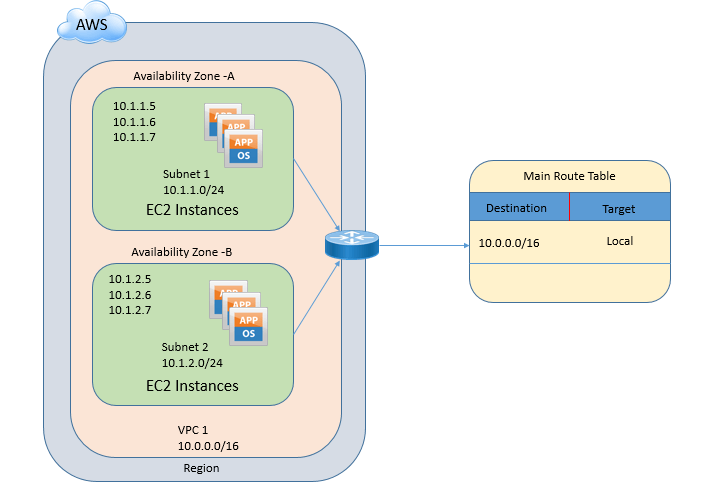
An amazon VPC consists of the following components
- Subnets
- Route tables
- DHCP options sets
- Security groups
- ACLS
An Amazon VPC has following optional components.
- Internet Gateways
- Elastic IP (EIP) address
- Elastic Network Interfaces
- Endpoints
- Peering
- NAT & NAT Gateway
- Virtual private gateway
Subnets:
Subnets are the IP address ranges which is assigned to EC2 Instances, Amazon RDS databases, and other AWS resources.
Once VPC is created, one or more than one subnets is assigned in each availability zones, subnets present in one availability zones cannot be spanned to another availability zones. Subnets may be public , private and VPN-only.
- Pubic Subnets:
Associated to routing table which directs the subnets traffic to VPC IGW. Instance which are running in a public network, they will be able to access internet by default and these instances can also be made to public internet by assigning Public or Elastic IP to them.
Public IP assigned to Instance is sourced from Public IP Subnet pools and are attached to instance randomly, whenever instance gets started.
When an instance using public IP address fails or is restarted or shutdown, it will not maintain same public IP address.
- Private Subnets:
Associated to routing table which does not directs the subnets traffic to VPC IGW.
Instance running on private network can communicate with all instances in all subnet that exists in that VPC. We can control traffic between all subnets through VPC network access control list and defines rules for communication.
Private Subnet can also be connect to other network via NAT gateway for outbound traffic , as well as VPN gateway or Direct Connection , that allow private subnet to communicate without on-premise systems.
- VPN-only:
Associated to routing table which directs the subnets traffic to VPG and does not have route to IGW.
Route Tables:
Route table is collection of destination routes, which is looked up by Network device to route traffic from one destination to another. Route table can be modified and we can add your own custom routes. Route table can also be used to specify which subnets are public, private and VPN-only. Each route table contains a default route which is also called as local routes.





LEAVE A COMMENT
Please login here to comment.