EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USBD VRF & EPG Design consideration - Service Chaining
Different deployment modes of L4-L7 devices:
There are different modes of deploying L4-L7 devices together with service graph.
Transparent Mode: In this L4-L7 device bridge the traffic between two bridge domains and in ACI it’s called as go-through mode.
Routed Mode: In this L4-L7 device is used for routing the traffic between two bridge domains and in ACI is it called as go-to-mode
One Arm Mode: In the L4-L7 device is connected to fabric via single interface over dedicated bridge domains.
Two Arm Mode: In this mode , a Layer 4-7 devices like LB is located on dedicated BD with two interfaces.
Policy Based Redirect (PBR): L4-L7 device is deployed in separate BD and client and server can redirect the traffic based on protocol and port number.
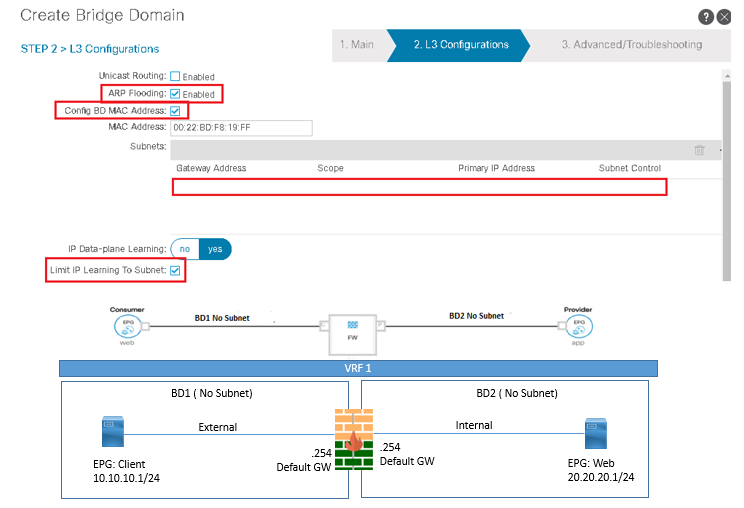
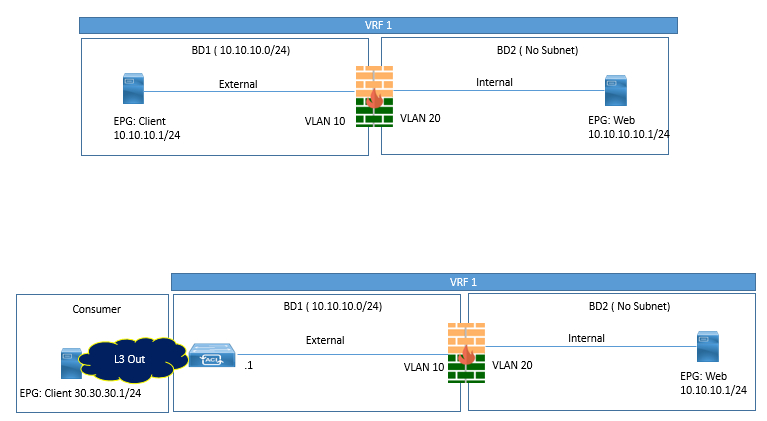
Firewall as Default gateway for clients and Server (Routed Mode)
In this mode, the Clients and server will point to Firewall as default gateway. In this mode, we need to configure BD in L2 mode that means BD with no subnets in same VRF.
Below Figure recommends some setting in BD and this type of design is very much used in POC or in LAB.
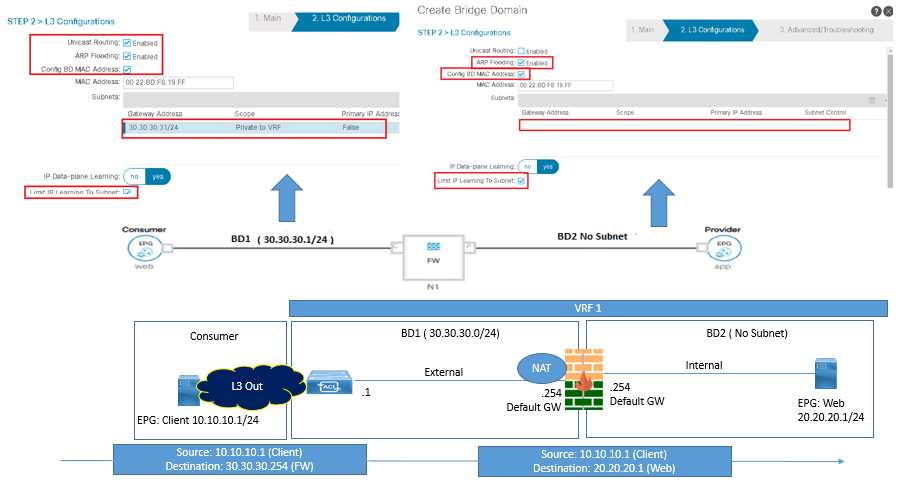
Firewall Not Default gateway for Clients (Routed Mode)
In this mode, one leg of firewall will be towards client side, and will be a part of L3 BD with a configured Subnet. In this Mode, NAT must be configured on the External Interface of FW, because ACI leafs have no information about server subnet behind firewall and hence it will not advertise via L3Out towards Client side.
This scenarios can also be configured without NAT. In order to achieve this, you need to route peer firewall with ACI Leaf, as shown in below figure. By doing this you can advertise the server subnet out towards client side.
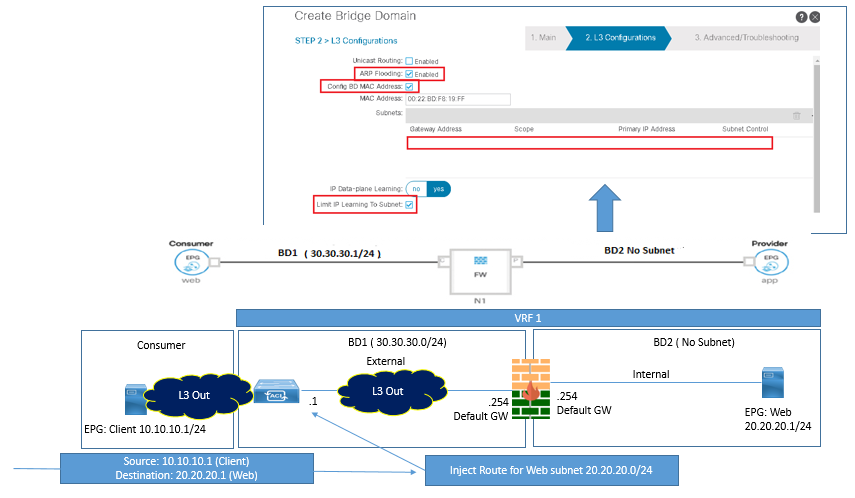
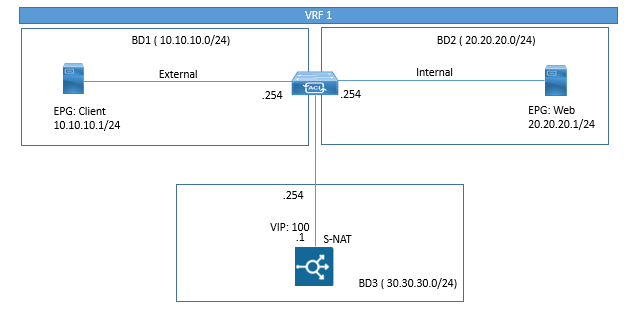
Route Peering with FW (Routed Mode)
Firewall are generally deployed in Network via Routed mode. When a BD is configured in L3 Mode and have a Subnet, in that case, clients will not be able to use firewall address as next Hop. The endpoints will use pervasive gateway subnet as its default gateway where as a firewall consumes one of the IP address in that subnet.
ACI service graph supports route peering with FW. Traffic will flow via firewall which performs state full inspection and forward the traffic towards destination endpoints as shown in below figure
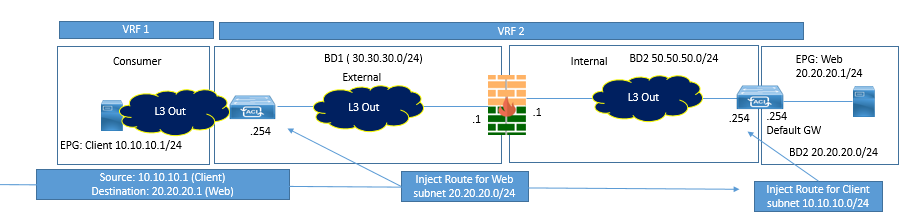
Service Graph with Firewall (Transparent Mode)
In transparent mode or bridge mode, Firewall behaves as a Layer 2 device, this can be understood by two example as in figure below:
In first example client and server are using the firewall as gateway and in second example client is on different subnet.
Service Graph with ADC (One Arm mode with S-NAT)
When Service graph is configured with ADC in one arm mode, we need to configure Source NAT on ADC. When we so, the return traffic will come to ADC only. If you still want to avoid Source NAT, you need to use PBR explained later in other sections.
Service Graph with ADC (Two-ARM Mode)
In this mode, BD do not need to have subnets unless you want Dynamic attach Endpoint feature provided by Service graph. By the way this feature gives you capability to dynamically attach an endpoint as part of your server pool as soon as endpoint is learned by fabric.
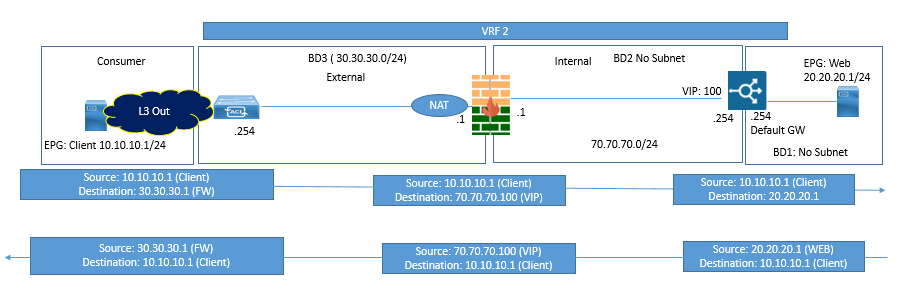
Service Graph with Two Service Nodes (FW in NAT & ADC in Two arm mode)
In this Mode, ADC can be your server default gateway else you need to enable SNAT on ADC. Firewall node till needs NAT as ACI leaf does not know about web server VIP behind FW.
Service Graph with two service Node (FW in no NTA and ADC in two arm mode)
In this mode, ADC can be your server default gateway else you need to enable SNAT on ADC. Firewall will not need NAT because its route peering with ACI leaf that will reach the VIP behind the FW through regular routing.
Service Graph with IPS:
IPS can be integrated with ACI via Service Graph in Un-Managed Mode only because, till the time of writing there is no device package available for Managed Mode Service Node for IPS.
In Unmanaged mode, each leg of IPS must be connected to different Leaf Switches because each leg of IPS will use same VLAN encapsulation to pass layer 1 traffic and service graph in Unmanaged mode does not support per-port VLANs.
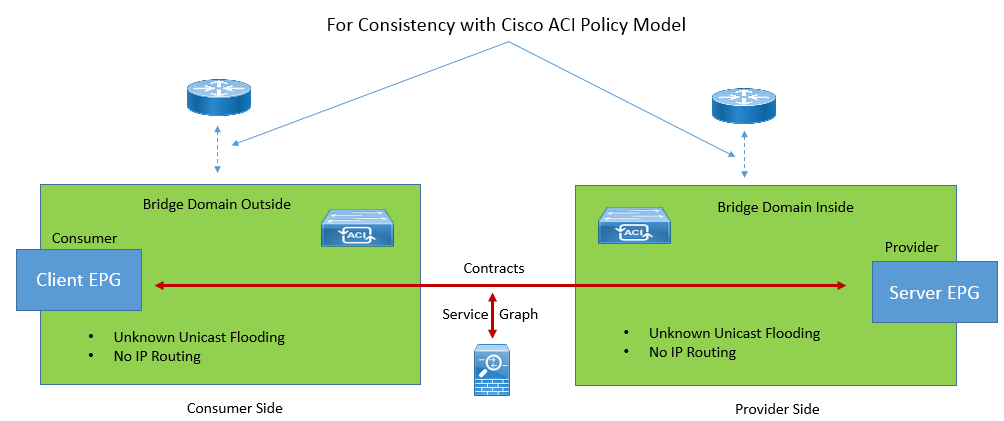
BD Design Consideration:
When we design the BD o for L4-L7 deployment, we generally considers two BD, one for Outside and one BD for inside.
Following are the default BD configuration option mostly used in deployment:
- Unknown Unicast flooding
- AR flooding
- No routing (except if the BD is acting as default gw for Servers or for L4-L7 device)
- No subnet ( except if the BD is acting as default gw for Servers or for L4-L7 device)
Below figure shows the basic deployment solution:
Here Two BD ae there one is connected to outside interface and one is connected to inside interface of L4-L7 device , there are two EPG , One is associated with BD used of outside and one EPG is associated to BD used for Inside. A VRF is associated to each BD which is not used for routing of traffic but used to simply meet the object model of ACI.
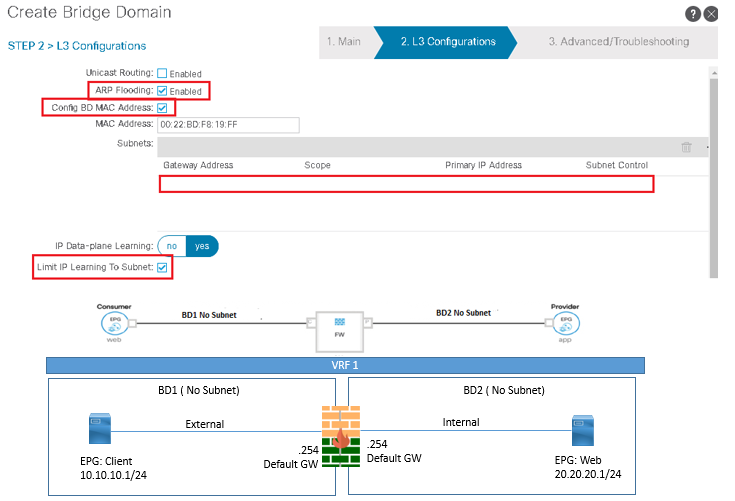
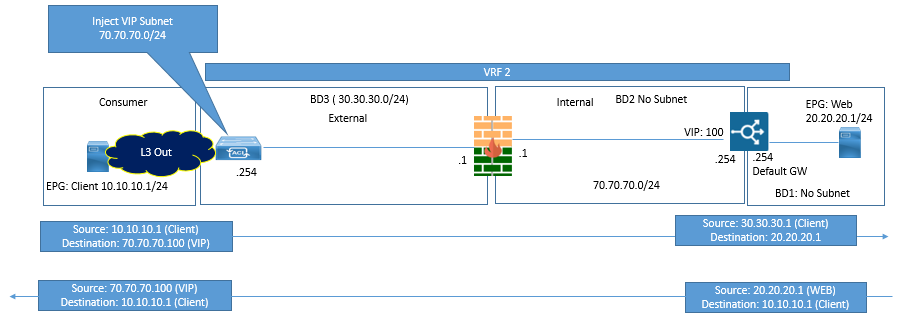
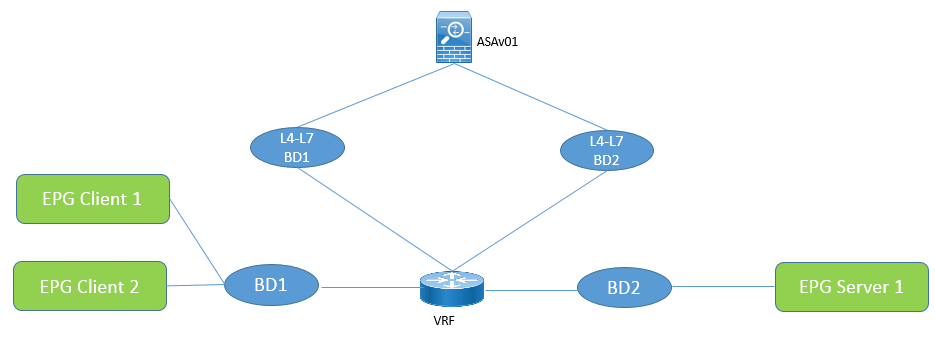
Now if you want to use the graph with redirect model, then you need to define one or Two BD on which this L4-L7 device will connect and must have data-plane learning disabled and GARP detection enabled. These BD will not be used to connect the endpoints.
Below figure will demonstrate, as Service Graph example showing on which BD Cisco ACI performs Layer 2 and Layer 3 Forwarding.
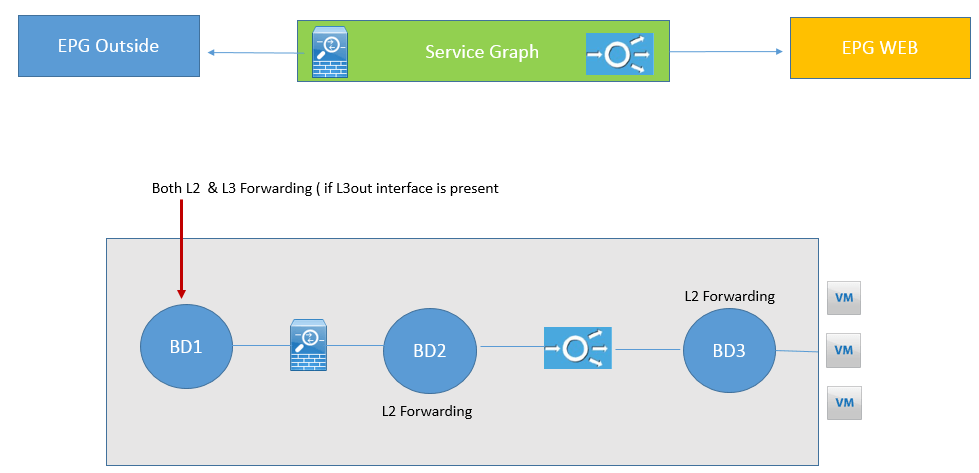
In figure, if BD1 has subnet configured and is GW for FW that traffic is switched at Layer 3, Now if BD2 is Next of LB is outside interface of FW and Next hop of FW inbound interface is load balancer in this traffic is switched at layer 2. Now in BD3 GW for Servers is LB so that traffic is switched at Layer 2.
In this scenario, you should enable Limit IP learning on BD1, else mapping DB can learn the IP address of endpoints from BD3, as if they were on BD1.
Tuning BD:





LEAVE A COMMENT
Please login here to comment.