EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USAccess & Fabric Policies
ACI does not allow to put VLAN on any interface , and in multi-tenant environment a VLAN range is allocated to tenant.
Fabric and Access policies must be configured before tenants configuration
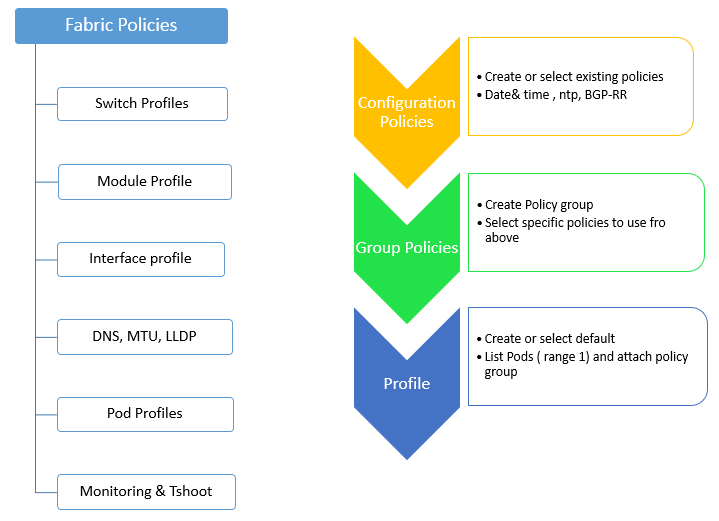
Fabric Policies:
Following are the Fabric Policies that are mostly configured :
Profiles:
- Switch: specify which switches to configure with call home or power supply redundancy feature
- Module: specify which spine switch modules to configure and associated monitoring policy
- Interface: specify which fabric interfaces to configure and associated monitoring policy
Global policies: specify DNS, fabric MTU default, multicast tree, and global LLDP settings
Pod profiles: specify date and time, SNMP, managements access protocols, COOP nodes and type, IS-IS, and BGP route reflector policies
Monitoring and troubleshooting policies: specify what to monitor and how to handle faults and logs.
Following flow is used to configure Fabric policies:
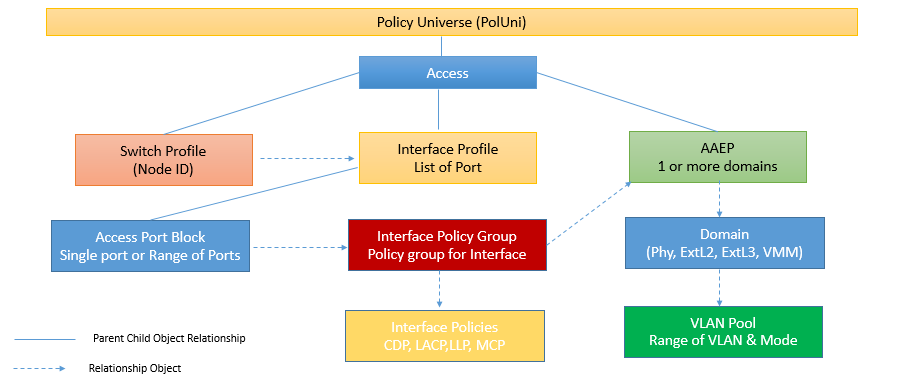
Access Policies:
Access Policies are used to configure port-level policies like CDP, LLDP, LACP etc and how they are programmed on physical Hardware.
Below are three main objects used in order to create the Access Policy.
- Policies: It is used to define all important characteristics of an interface which is being applied to an interface or Switch directly.
- Policy Group: This Group all individual policies to create a policy group, which can be later reused on different Switch.
- Profiles: They are used to tie the policy group to specific interface and switches.
Switch Policies:
When we want to configure switch specific parameters in ACI fabric, we use Switch Policies. These Policies can be grouped together for common functionalities and applied to specific switch nodes.
Switch policy can be created by using three different main categories.
- Policy: These are used to define switch wide setting such as COPP or VPC domain.
- Policy Group: It is used to combine different policies as a one group. If any changes done to policy group, any switch profile using policy group will be updated.
- Profile: Switch Policy group is tied in to Switch Profile, and then is applied in to fabric node. It is recommended to configure Switch profile as one to one mapping of physical nodes to switch profile. It is also recommended to have one switch profile for two switches which are part of VPC domain.
Let’s suppose you have four leaf switches having ID 201, 202, 203, 204 then you will create four leaf profile named Leaf 201, Leaf 202, Leaf 203, Leaf 204. But let's suppose you have one VPC domain between Leaf 203 and Leaf 204 then one additional Switch Profile vPC-Leaf-203-204 needs to be created.
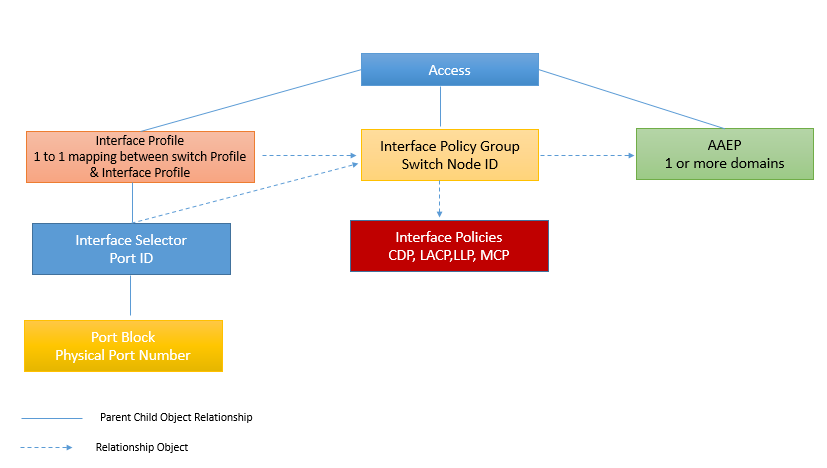
Interface Policies
Interface policies are grouped together for end host connectivity that have common functions.
These policy can be created by using three different main categories
- Policies: It is used to define all important characteristics of an interface which is being applied to an interface or Switch directly. Ex: CDP, LLDP. LACP etc.
- Policy Group: This is used to combine all policies together, as a one group. If any changes done to policy group, any switch profile using policy group will be updated.
- Profile: Interface Profile, is used to map interface to an interface selector. This Interface profile will also be mapped with Switch Profile. This Interface profile is used to create a link between Interface Policy Group and leaf switch, on which policy is to be deployed.
It is recommended to configure Interface profile as one to one mapping per switch. It is also recommended to have one interface profile for two switches which are part of VPC domain.
Let’s suppose you have four leaf switches having ID 201, 202, 203, 204 then you will create four interface profile named Leaf 201, Leaf 202, Leaf 203, Leaf 204. But les suppose you have one VPC domain between Leaf 203 and Leaf 204 then one additional interface Profile vPC-Leaf-203-204 needs to be created.
Global policies:
It include DHCP, QoS, VLAN Pools , Domain and AAEPs ,Physical and external Layer 2/Layer 3 domains contain the port and VLAN IDs
In global policies, VLAN Pools, Domains and AAEP is used.
VLAN Pools:
A VLAN Pool is used to define a range of VLAN that are allowed to be deployed on ACI fabric. With ACI, the pool created can be extended on physical interface.
Another use of VLAN pool is that, it creates the list of VNID range assigned to each VLAN. It is used to break unnecessary broadcast BPDU, Flooding Encap, when these features are configured or used in.
Third benefit of VLAN pool is for VPC switches. When two switches are in VPC domain, VPC and orphan port learned endpoints are synchronized between the two switches, and then the VNID must be same in order for synchronization to be successful. When a VLAN is mapped to an EPG that is deployed in VPC pair the domain from which that EPG is deployed, must not have overlapping VLAN pool.
Domains:
When we deploy an EPG to switch port, a VLAN is reserved for that specific EPG Switch Wide. Having this process can create a problem, when a single tenant uses up all VLANs available on switch. In Order to prevent from this, we can limit the no of VLANs that any tenant can deploy on an interface.
In relation to this, In ACI VLAN pools are mapped to domains and are not directly mapped to interface. Now these domain are mapped to an AAEP. On the domain itself, admin can restrict which tenant has access to which specific domain and access to that particular VLAN pool.
There are five types of domains:
- Physical Domain: It is used to deploy static path attachments to an EPG.
- Virtual domain: VMM domain are used when integrating virtual domains with Cisco APIC.
- External Bridged domain: It is used when we create an external bridge network.
- External Routed: It is used when creating an external routed network.
- Fibre Channel: Fibre channel domains are used to when fibre channel devices are used to connect to ACI fabric.





LEAVE A COMMENT
Please login here to comment.