EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USISE Accounting & Auditing Policy
This feature enable ISE to track the user and administrative activity. This function is used in preventing, detecting and minimizing impact of Security Compromise.
ISE collect logs of each activity, and tis logs allows to track, Alert, and analyze when something goes wrong.
This also helps in auditing the compliance of any system, like Payment Card Industry Data Security Standard (PCI DSS) .
Here we will see some the Compliance Rule defined under PCI-DSS and will see how these compliance rules are configured in ISE accounting & Auditing policy.
ISE policy for PCI 10.1: Ensuring Unique Username and Password
Each administrator must have unique username and password so that their activity can be audited. Below figure shows example of creating a Local ISE super administrator account.
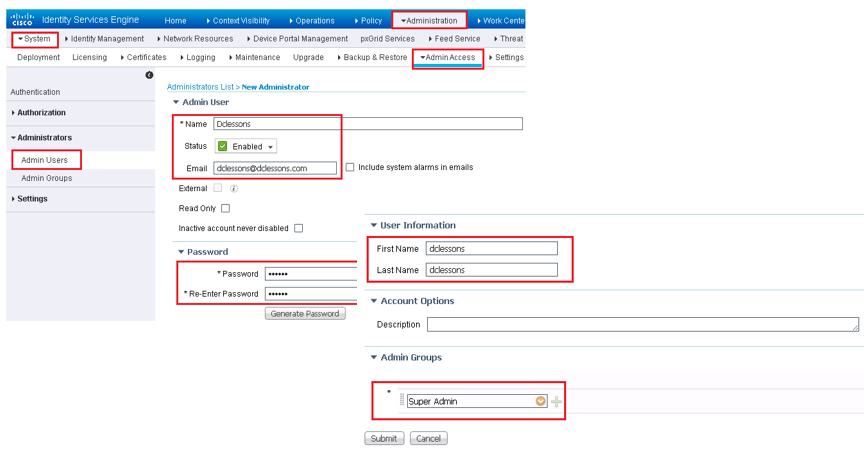
Each Admin must have proper level of Privilege required to perfume the day to day operation activity. To achieve this ISE built in administrator authorization permission or Manually Custom administrator permission can be created.
There are two administrator authorization permission in ISE.
- Menu Access: It determines which menu the administrator can see
- Data Menu: It allow to grant full or no access to ISE Interface like Admin Groups, User Identity Groups, Endpoint Identity Groups, Locations, and Device Types.
Below figure shows Menu Access permission screen and can be access from: Administration | System | Admin Access. Here you see some menu is allowed and for some is blocked.
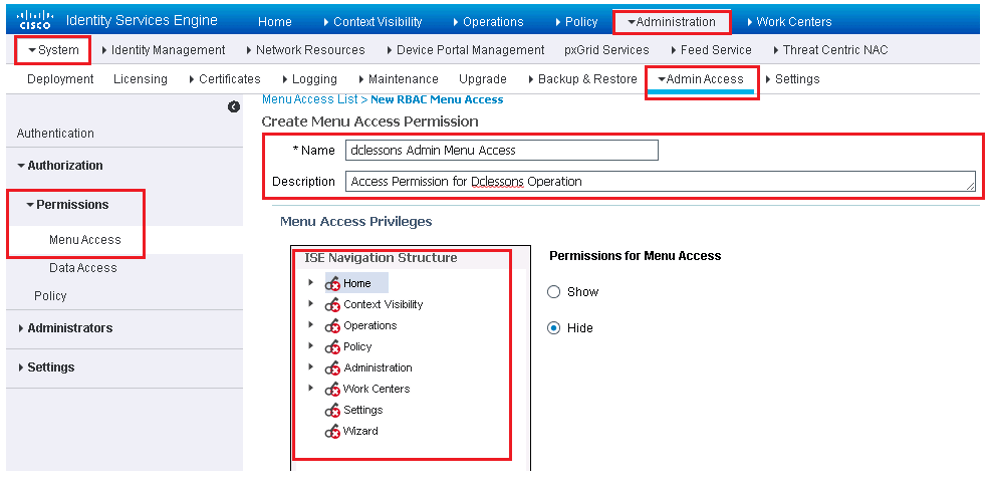
ISE policy for PCI 10.2 & 10.3: Audit Log Collection
This Section tells about type of audit logs that should be enabled in ISE which comply PCI-DSS 10.2 requirement.
Audit logs that ISE can create are broken in to logging categories, as shown in below figure.
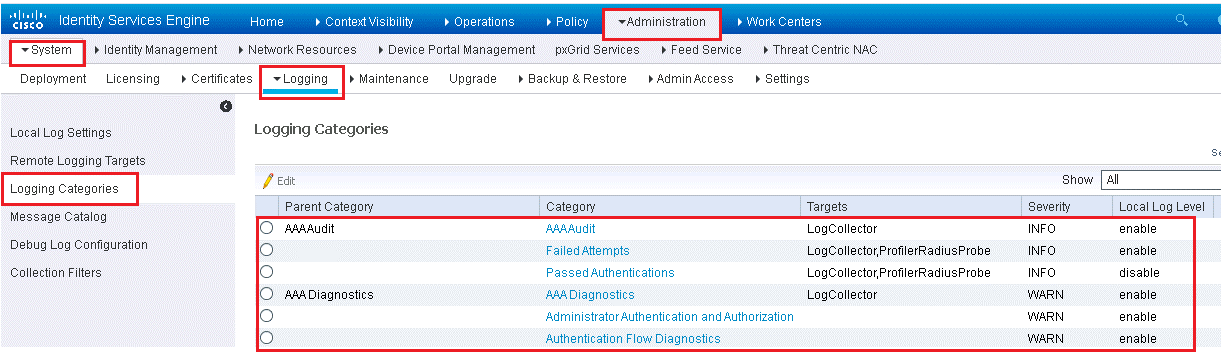
This can be accessed from Administration | System | Logging | Logging categories.
As Best Practice, all of these categories must be enabled for Logging.
In above Figure, target column shows to which logging servers, messages will be sent for logging and Storages. These Target are UDP Syslog’s server or Secure Syslog Server.





LEAVE A COMMENT
Please login here to comment.