EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USConfiguring Client Provisiong Portal, Policy Element & policy
While doing Posture assessment from ISE, End point must have agent installed on it. ISE, ASA or client software provisioning system can be used to install agent to endpoints. If ISE is being used to install agent then in that case, Client Provisioning portal must be configured.
Once User successfully authenticates and request network access , ISE will redirect the client to Client provisioning web portal and allow them to download the posture agents.
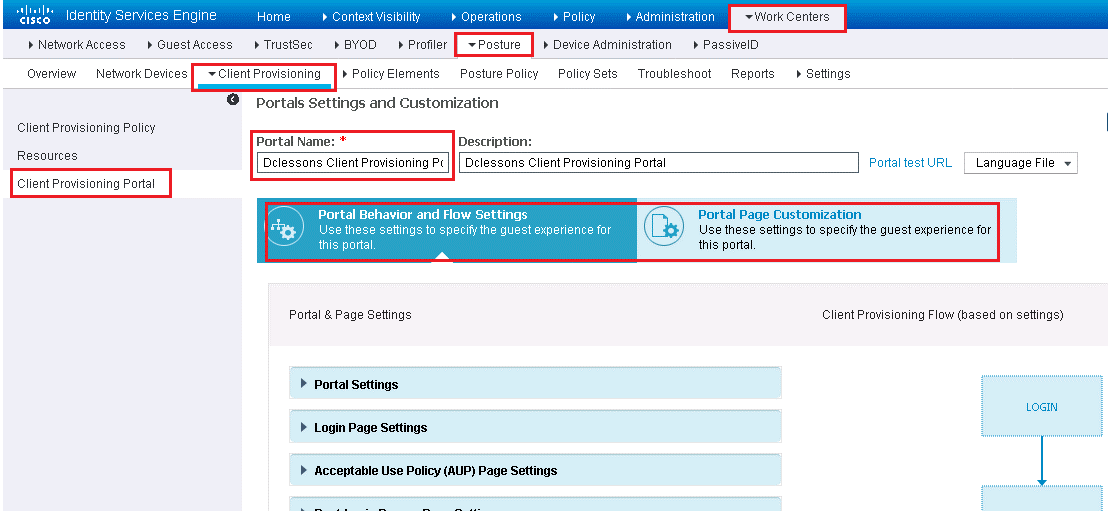
In order to set up, go to Work Centers | Posture | Client Provisioning > Client Provisioning Portal | select the Default portal, | click Duplicate.
Provide name and Description and Click on Portal Setting | Change Port & Interface as per your environment.
Configure Posture Elements
Posture Elements will be further used in Posture Policy and there are three categories of posture policy elements.
- Condition
- Remediation
- Requirement
Below path show these three elements.
Work Centers | Posture | Policy Elements.
Configure Posture Conditions
There are many types of Posture conditions. In order to configure use below path and Figure
Work Centers | Posture | Policy Elements | Conditions.
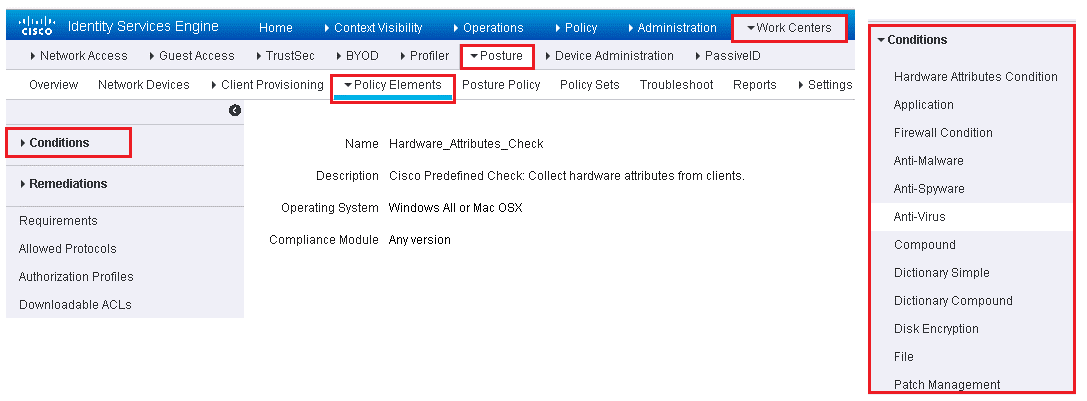
Most of the condition are prepopulated via Cisco.com posture update process. In order to speed configuration & Deployment, ISE has preconfigured conditions. Example:
Cisco-defined simple conditions have pc_ as their prefixes and compound conditions have pr_ as their prefixes. You cannot delete or edit Cisco-defined posture conditions, but you can duplicate them and edit the duplicate.
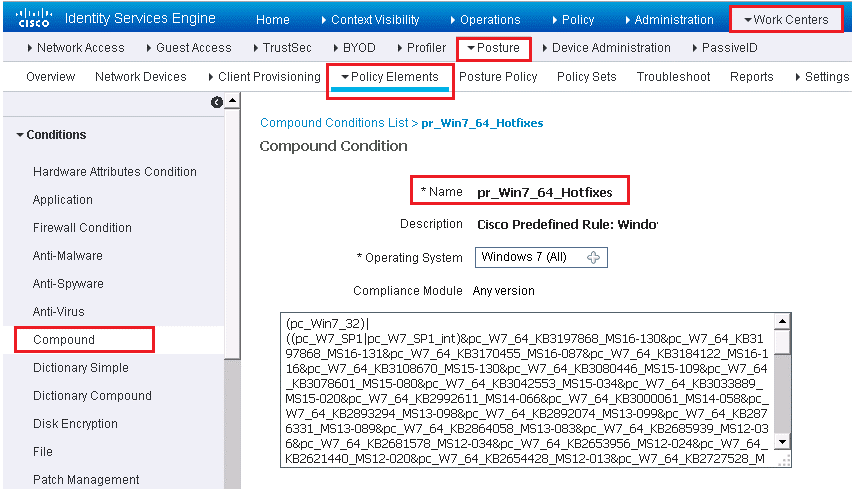
Below figure, shows an example predefined compound condition. This condition checks to ensure that all Windows 7 x64 critical hotfixes are installed. As new hotfixes are released by Microsoft, this rule is auto-updated by Cisco ISE.
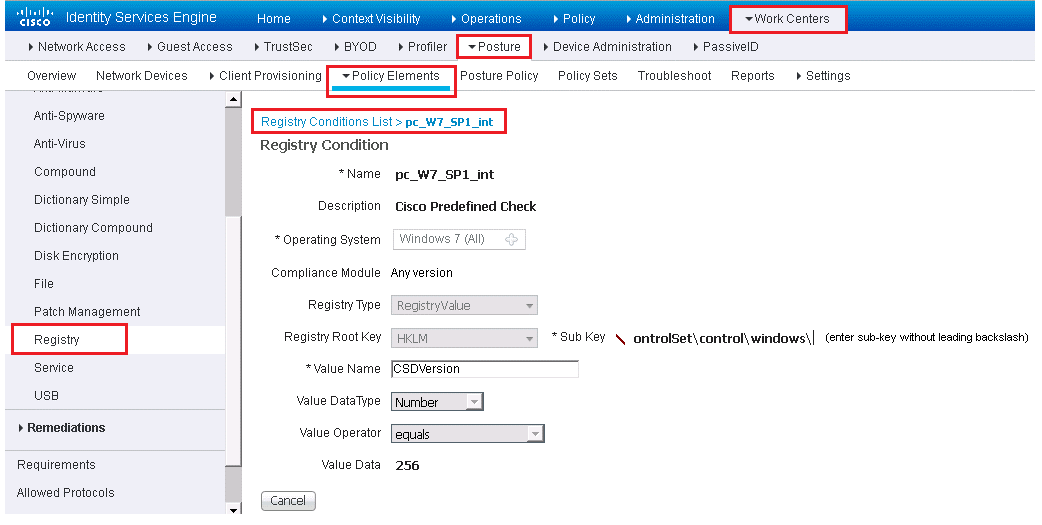
Below figure gives example of Registry condition setting.
The Anti-Virus (AV), Anti-Malware (AM), and Anti-Spyware (AS) compound conditions are similar. By default, ISE provides a check for any AV, AM, or AS installed on Windows and Mac. Also included is a check for any AV or AS definition file that is 5 days old or older than the latest file date for Windows and Mac. Below figure shows predefined AV conditions.
Configure Posture Remediation
These are action that any AnyConenct agent, NAC agent, Endpoint can use to fix any failed conditions to come in to posture compliance.
Below figure shows different ISE remediation categories.
In ISE 2.2 , below figure shows the available remediation actions listed by supported agent type.
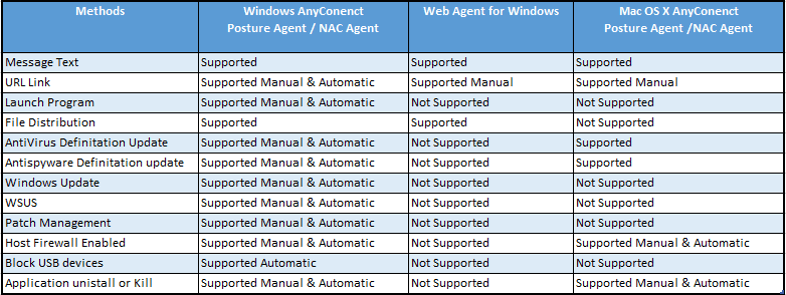
Now if the remediation action is manual, then in that case, end user will get the NAC agent popup with instruction, user will need to click and perform the action.
If the action is automatic, NAC agent will perform the actions automatically.
Below are steps to create or edit remediation actions.
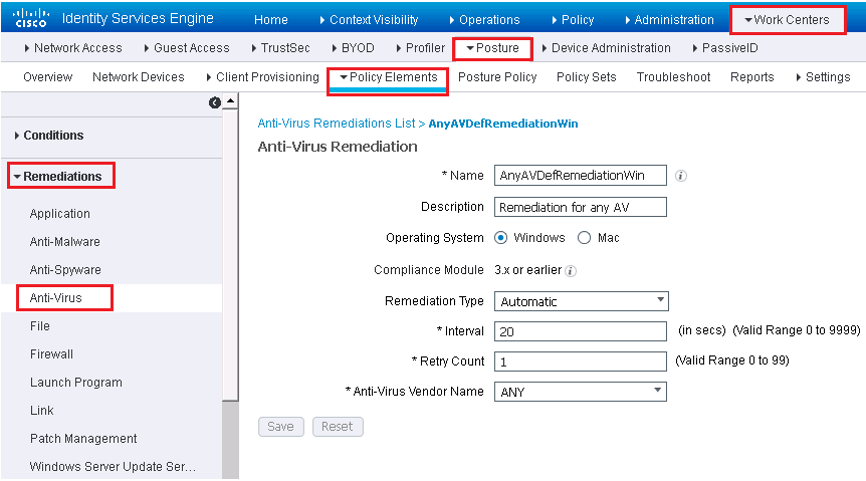
Work Centers | Posture | Policy Elements | Remediation | Select remediation Type
Fill the fields as per below figure
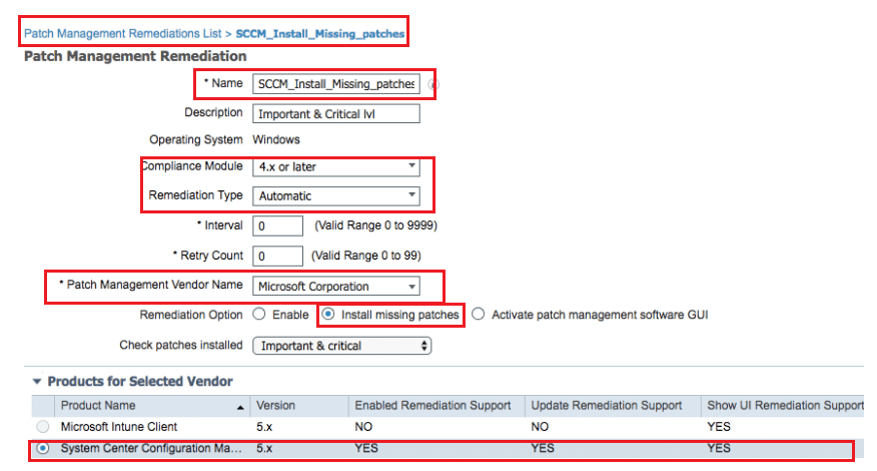
Also create the patch management rule in addition to Corporate AV remediation rule. Patch management is only supported by Windows OS. ISE remediation natively support 20 Patch Management Vendors. Below example shows a Windows System Configuration Manager (SCCM) update rule.
Configure Posture Requirement
Posture requirement is a set of compound conditions and its associated remediation actions that is linked with a role and with an Operating Systems. When Clients connects to network, it must meet the necessary requirements during posture evaluation to become compliant in network.
There are some predefined ISE posture requirement that can fulfill the AV,AM, USB and AS use cases.
In order to create the Posture requirement in ISE GUI, use below method.
Work Centers | Posture | Policy Elements | Requirements.
Click the drop-down arrow at the right end of a row and select Insert New Requirement or Duplicate to duplicate an existing one.
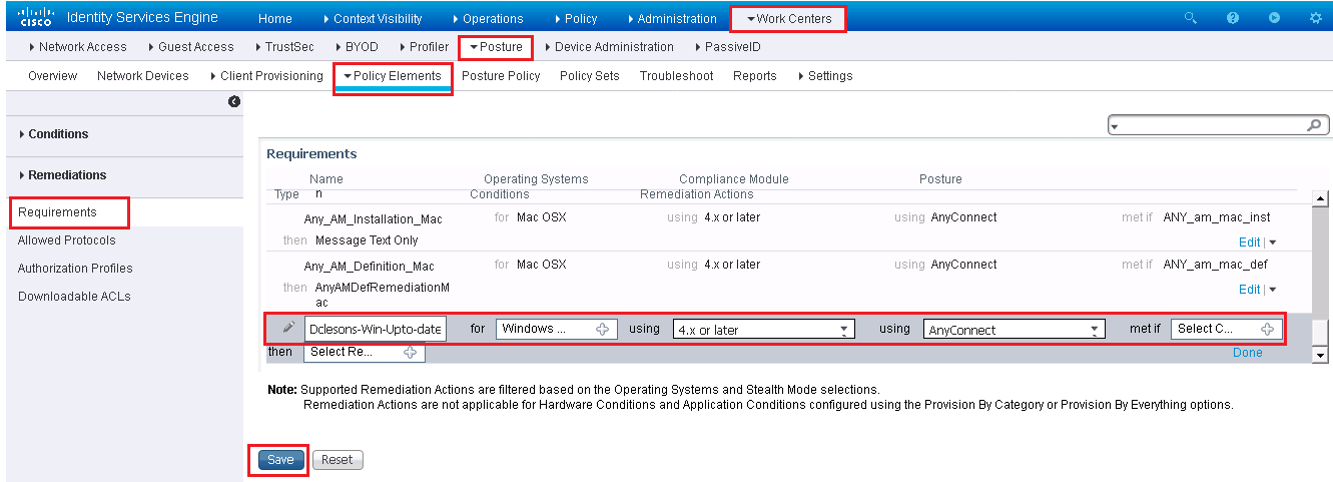
The requirement in above figure called Windows Up-to-date applies to all Windows 10 endpoints and is met if the condition pr_AutoUpdateCheck_Rule is true. Otherwise, the remediation action of WSUS_Remediation is executed. Create the requirements that you need for your environment and host security policy.
Configure Posture Policy
In order to configure Posture Policy, use below path:
Work Centers | Posture | Posture Policy
A posture policy maps posture requirements to selection criteria such as operating system, identity or external group, or other conditions. This allows you to define different posture policy rules, which you can individually enable or disable, for the various client and user types. Each requirement listed within a posture policy rule has its own status setting of Mandatory, Optional, or Audit ( below figure shows the options).
Mandatory means that the requirement must be met in order for the endpoint to be allowed on the network. Optional means that if the endpoint fails the requirement, it still passes onto the network but any automatic remediation actions are executed. Audit only logs the requirement result and does not affect the client’s ability to access the network nor execute any automatic remediation actions. Audit requirements are transparent to the end user.
Below figure shows the posture policy table along with an example policy. No policies are configured by default. If you have created policies, to add a new one just click the drop-down arrow at the far right of a rule and select either Duplicate or Insert.
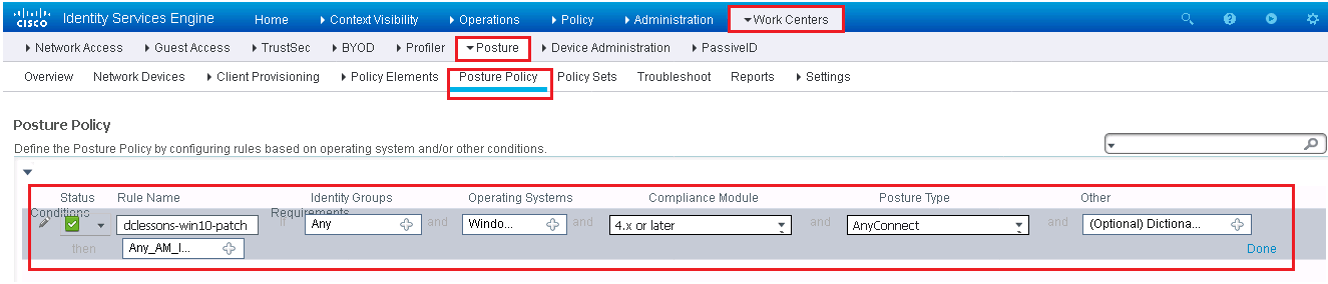
It is very essential to use the Audit mode to configure your policy and test it as per expectation.
Above example policy ensures that all Windows 10 endpoints with Domain Users logged in have an up-to-date antimalware program. If the requirement fails, then the assigned remediation action kicks off an AM client definition file that updates automatically.





LEAVE A COMMENT
Please login here to comment.