EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USAAA Fundamentals
In this section we will learn Configuring AAA in ISE and we will see its deep dive concepts.
AAA stands for Authentication, Authorization & Accounting. There are two aspects of AAA in Network & Security Field.
- Device Administration
- Network Access AAA
Device Administration:
When access to device is required via Console, SSH, Telnet, AAA is used to control its access. A user can authenticates to Cisco IOS shell and when request goes to ISE, it can either permit or deny user execution of individual command.
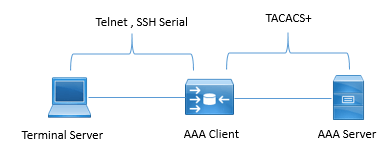
Authenticating device is authenticated once but it is authorized many times during single session in CLI of device.
Network Access:
In this, user identity is learned and based on policy, permit or deny to user access is determined. RADIUS protocol is used between network access device (NAD) and authentication server. Earlier Authentication was done by PAP or CHAP protocol. Currently RADIUS protocol is widely used for Network Access AAA between Cisco ISE and Network Device.
TACACS+:
TACACS+ was developed by Cisco around 1990 and became supported protocol with Cisco ISE 2.0 and prior to ISE 2.0, ACS server was used as Primary AAA server for Enterprise. With ISE 2.0, ISE replaced the ACS for both RADIUS and TACACS+.
TACACS+ uses TCP protocol on port 49 to communicate between TACACS+ client and TACACS+ server.
TACACS+ is protocol used for authentication as well as authorization many times during a single administration session in CLI of device.
TACACS + Authentication Message:
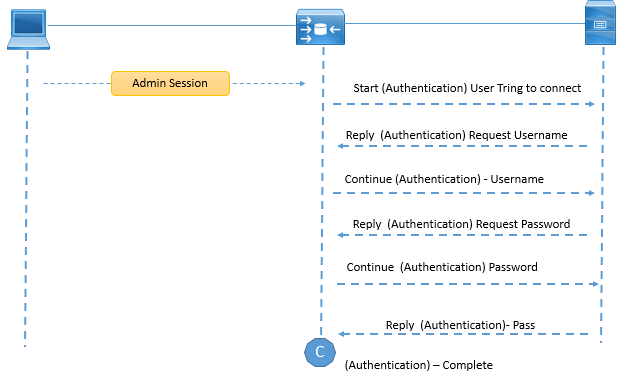
When TACACS+ is used for Authentication, There are three types of Message or packets are exchanged between client (Network Device) and Server.
- START: It is used to start the authentication process or request between AAA Client and AAA Server.
- REPLY: It is the message or packer sent by AAA Server to AAA Client.
- CONTINUE: It is message from AAA Client used to respond to AAA server request for user name and password.
AAA Client sends the START message to start Authentication request, this START message tells AAA server that a client want to authenticate and authenticate request is coming. REPLY message will be sent from AAA Server to AAA Client every time during authentication. AAA Server send REPLY message to Client to get Username and password. AAA Client will send the username with CONTINUE message, once AAA Server receives the username, it will respond to AAA Client with REPLY message asking for password.
AAA Client will send password with CONTINUE message and server will finally send REPLY message with authentication –pass or fail status.
Below is the possible value AAA Server will send to AA Client with final REPLY Message are as follows:
- ACCEPT: User Authentication succeed and authorization process can begin if AAA Client is configured for authorization.
- REJECT: User authentication is failed, login is denied to end user and AAA Server may ask for authentication again.
- ERROR: An Error occurred during authentication process. AAA Client will reattempt for authentication.
- CONTINUE: AAA User asked for additional information, this message is not same message type discussed on main Authentication process discussed above. This Message type is used for item such as password change, or requesting for second authentication or token.
TACACS+ Authorization & Accounting Message:
Once authentication is done, only two message type is used for authorization between AAA Client and AAA Server.
- REQUEST: When Client request for authorization, this REQUEST message is used. The Authorization may be to access Shell, or to authorize specific command and we say as request for authorization for specific Service. Each Service may be communicated with attribute-value (AV) value pairs.
- RESPONSE: This message is send from AAA Server to AAA Client with result of authorization request asked by AAA Client.





LEAVE A COMMENT
Please login here to comment.