EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USUCS Organizational Structure
In UCS, Organization can be created and is used for policies, pools, and service Profile. By default, the organization for each category is root. Now based on Enterprise requirement, multiple sub-organizations can be created under root organization.
We can also create nested sub-organization under another sub-organization. These hierarchal configurations in to sub-organization has following benefits:
- Role based Access Control
- Multitenancy
If you want to create sub-organization, follow below procedure
Login to UCS | Under Server | Click on Root and Right-click on root and select create organization
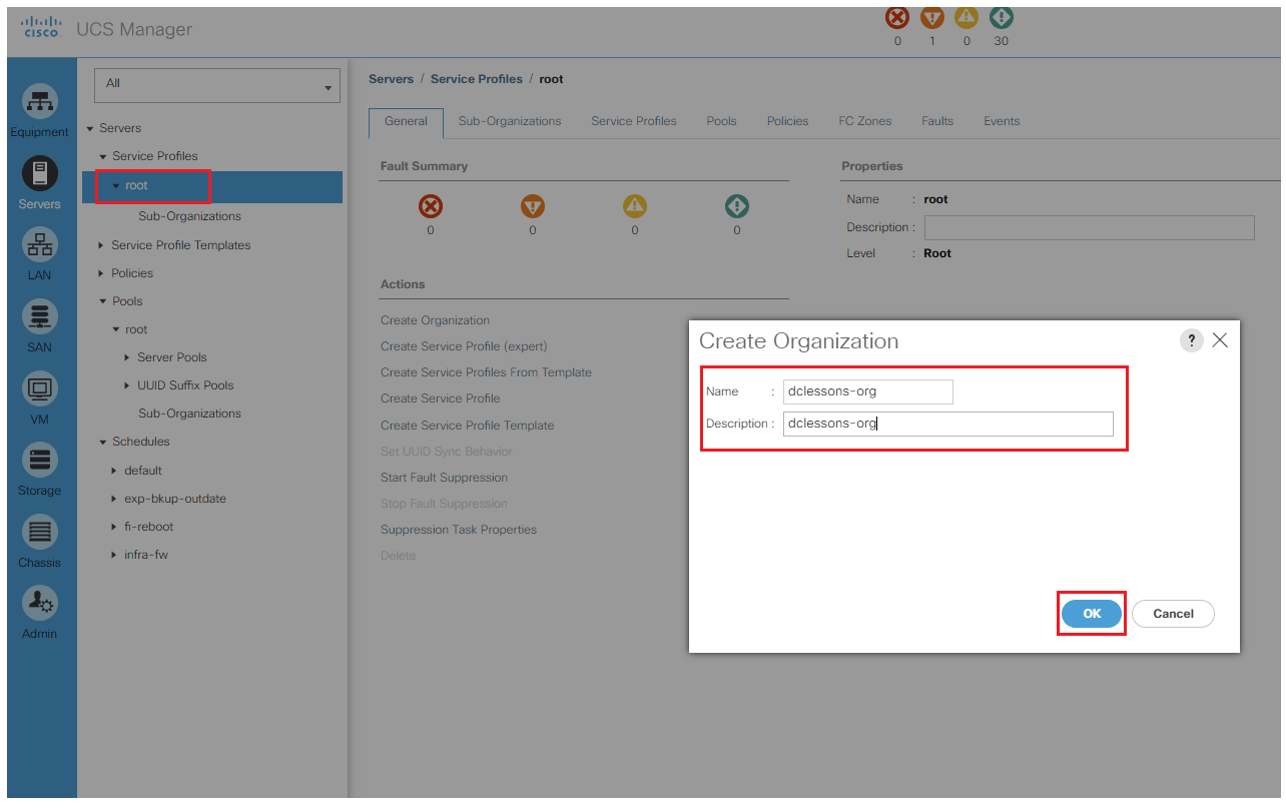
The policies, pools, and other resources configured under the root organization are available to all sub-organizations. Root is the parent organization for all sub-organizations. The resources configured under the sub-organizations at the same level are not shared among the other sibling sub-organizations. A sub-organization under another sub-organization shares the resources of the parent.
Role Based Access Control
UCS RBAC provides granular control over the user security privileges. Combined with UCS organizations, RBAC delegates and controls the user access privileges according to the role and restricts user access within an organization boundary defined for the tenant in case of multitenancy.
Access privileges provide the users with the capability to create, modify, or delete a specific type of configuration. UCS provides some predefined roles and it is also possible to create custom roles based on requirements. The roles are a collection of different privileges. Hence, roles can be assigned to users according to their job requirements.
In UCS, a user's authentication can be configured from various resources including the following:
- Local user
- LDAP (Active Directory, OpenLDAP, and so on)
- RADIUS
- TACACS+
Active Directory Integration
We will now configure the AD/LDAP authentication integration for UCS. We will integrate UCS Manager to the Microsoft Active Directory domain controller. On the AD side, appropriate user groups should be created that can be used to provide mapping to UCS roles that provide privileges to the AD authenticated users accordingly.
Perform the following procedure to enable Active Directory authentication:
- Log in to UCS Manager.
- Click on the Admin tab in the navigation pane.
- On the Admin tab, click on User Management to expand its content.
- Click on LDAP in the navigation pane and click on Create LDAP Provider in the work pane:
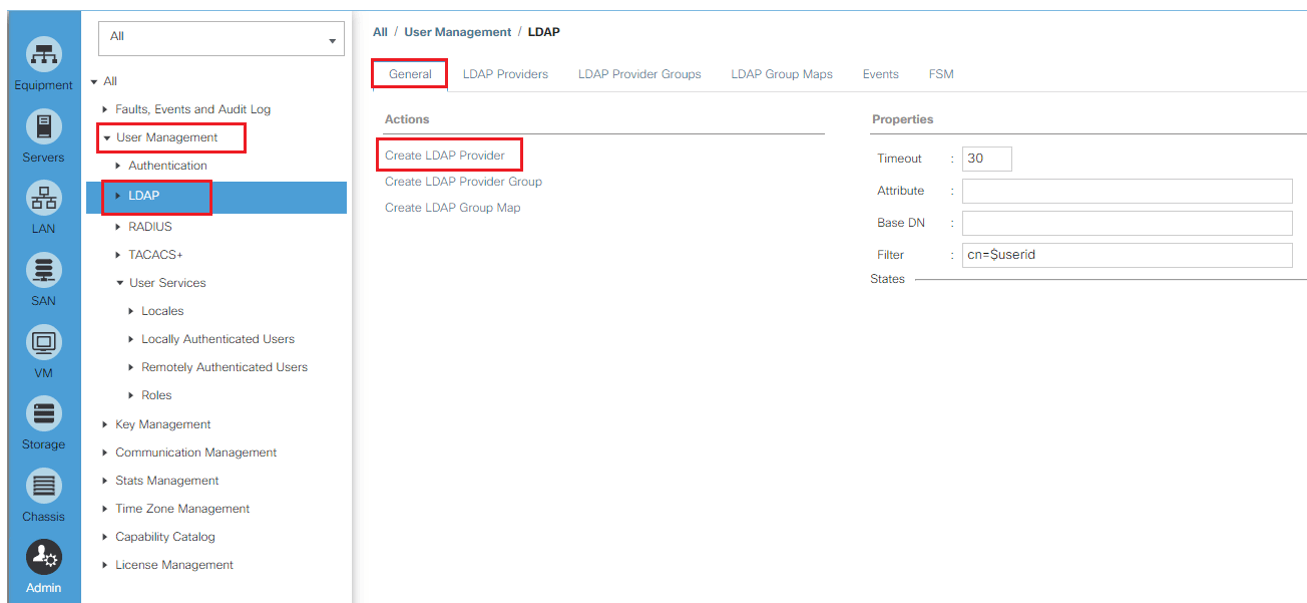
In the pop-up window, provide the following AD configuration details:
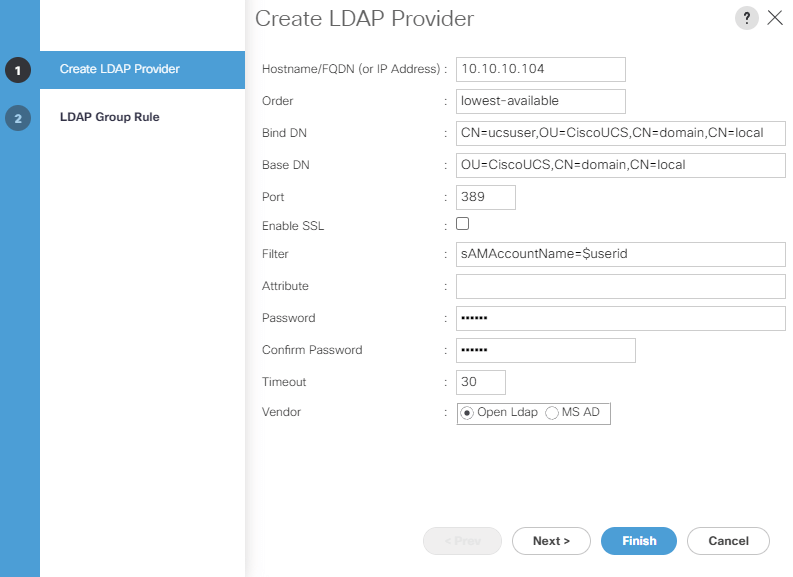
- Provide a DNS hostname or IP of the domain controller.
- Type in lowest-available in the Order field.
- Provide the distinguished name (DN) of the user with read and search permissions in the Active Directory in the Bind DN field. It is recommended to use the normal user or service account with read permissions only and not an administrator account for Bind DN.
- Provide a specification location of the AD where the search should start in the Base DN field. You may start from the root of the AD for smaller organizations. For a large AD implementation, it is recommended to start the search from the OU where the AD users/groups are located.
- Type 389 in Port and leave Enable SSL unchecked for regular communication without SSL or check Enable SSL with the appropriate AD port.
- Type sAMAccountName=$userid into the Filter field.
- Leave the Attribute field blank.
- Type in a password for the bind user configured in step 3 and reconfirm the password. Type in a Timeout value in seconds
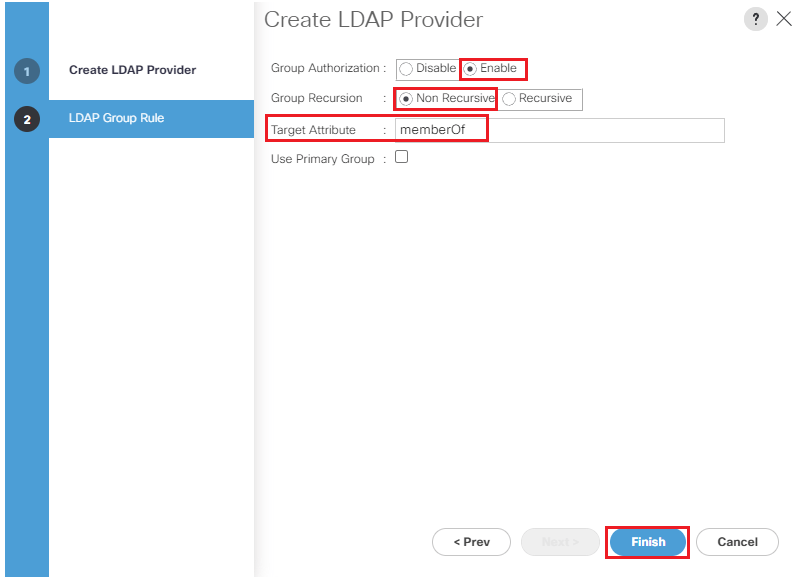
- Click on Next and configure Group Authorization by clicking on the Enable button.
- Leave the other two settings, Group Recursion and Target Attribute, with the default values.
- Click on Finish.
- Repeat the steps for the other domain controllers
Create an LDAP provider group adding all domain controllers in the provider group and perform the following steps:





LEAVE A COMMENT
Please login here to comment.