EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USConnecting AWS & On-premises Network
If we want to connect our On-Premises network to another Network in WAN, below are some options available
- Connectivity via Internet
- Via VPN Client, user can connect to office and Application
- Via Site-to-Site VPN, to connect from one location to another location
- Via Leased Line or Optical Fiber to connect collocation and DC Sites.
In AWS, there are two options available for connecting on-premises network to VPC.
- Direct Connect
- VPN with Virtual Gateway
Connecting On-Premises with VPC via VPN (Virtual Private Gateway)
Amazon VPN gateway is very cost-effective Managed Service Solution available to connect the On-Premises to AWS VPC. VPN gateway is logical network gateway device, which establish IPSec VPN tunnel from AWS VPN to on-Premises VPN Device.
For each VPN connection, two public tunnel endpoints are created, which enables automatic failover from VPN Gateway device, as shown in below figure
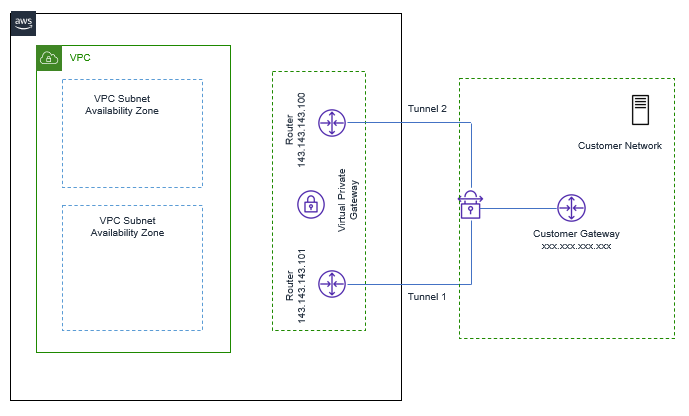
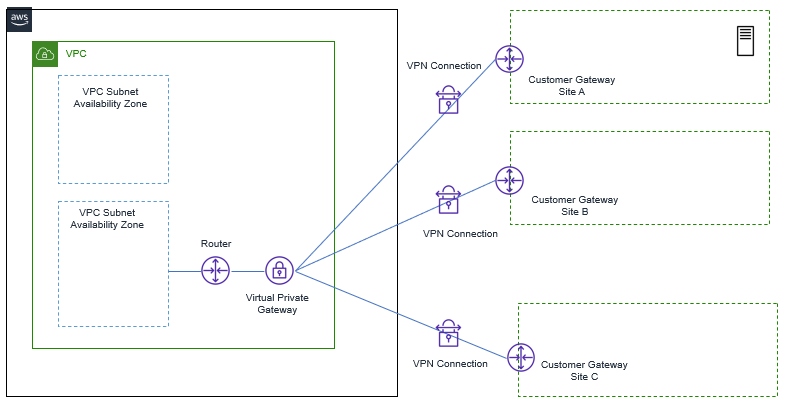
With this Service, from one VPN gateway, we can be able to connect to Multiple remote sites, but no transient traffic can pass through VPN gateway.
VPN Gateway Limits
- By Default, Each AWS Account, has limit to create up to 50 Site-to-Site Connection Per region and up to 10 Site-to-Site connection Per VGW.
- The VGW supports NAT Traversal out of box, can be configured to use 2–4-byte ASN.
- Each VGW supports 1.25 GBps throughput via IPSec VPN.
Securing VPN
Each AWS VPN IPSec tunnel supports following protocols for Authentication, Key Exchange, Traffic transmission phase.
- IKEv2 and AES256 Encryption
- SHA-2 Hashing
- Diffie-Hellman groups.
Now for traffic between Server & Client, which are not on VPN, for those type of traffic ( traffic with in VPC or traffic inside on-Premises) , security can be achieved by using HTTPS, SSL Encryption or TDE for database.
Connecting On-Premises with VPC via Direct Connect
When we see that we cannot meet our throughput requirement via VGW or to use huge Virtual instance of VGW for our throughput requirement, it will not be economical.
In that case, we can use better option, to have fast, reliable, Private link – called AWS direct Connect.
AWS Direct connect allow us to establish a dedicated layer 2 network connection between your network and Direct connect Location rack.
When there are following requirement as mentioned below, we can use Direct Connection Services
- Lower Latency
- Predictable Performance
- Higher throughput
- Large amount of data, needs to be transferred daily between on-Premises and AWS
- Security & Compliance requirement, for not to use Internet Link.
Below dig shows how AWS Direct Connect can be used to connect AWS VPC to On-Premise’s network.
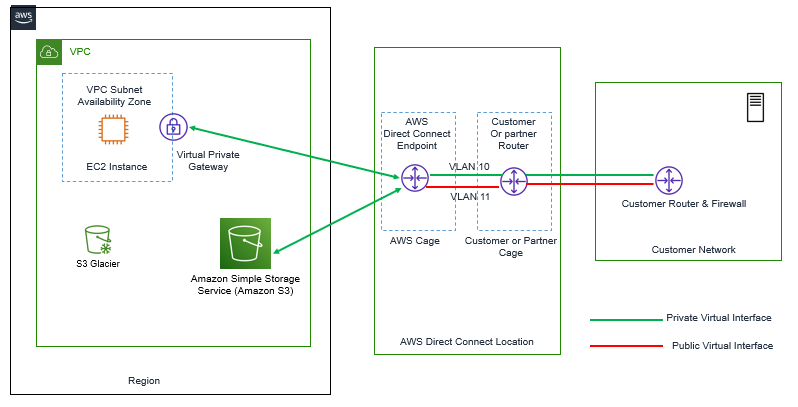
When we want to connect the Customer network to AWS VPC, two types of connection is required.
- Connection between AWS region and Direct Connect Location
- Connection between Direct Connect Location and Customer Location
For Connection between Direct Connect Location and AWS, we need to deliver the Router and terminate the optical link between AWS Direct Connect Location rack and AWS and for Second part of connectivity, we will have to explore options that how you can connect your on-premises Location to Direct Connect Location.
Now in order to connect to different VPC and public AWS endpoints, we have to create a VLAN that will connect us to each private or public interface created. A private interface will allow connection between VPC and On-Premise’s network, optionally you can establish a VPN connection over Direct Connect Link to encrypt your traffic.
Now When a Direct Connect provider uses MPLS, connection and uses different VLANs to connect to On-Premise’s network to Direct Connect location, other than VLAN used by AWS to Connect to VPC. In that case we have to use Q-in-Q VLAN Encapsulation to provide ability to connect to different AWS resources.
Let’s Understand this via an Example, a Direct Connect Provider uses VLAN 23 for MPLS Connectivity between Direct Connection Location & Customer On-Premises DC. Whereas in AWS We are using VLAN 10 and VLAN 11, each connecting to Separate VPC. Now this will require to enable Q-in-Q between our On-Premise’s network device and Customer Router present in Direct Connect Location, which is connecting to AWS also. In this Q-in-Q connection, VLAN 10, VLAN 11 are encapsulated to VLAN 23 while in transit on MPLS link.
Requirement of Direct Connect Solution
- In Order to use the AWS Direct Connect Solution , Customer must be located in an area which are being serviced by an AWS Direct Connect partner.
- Need for device, that support Single-Mode Fiber Connection with 1000BASE-LX or 10GBASE-LR transceiver.
- Device must support , Port Speed and full duplex mode configuration manually .
- Device must support BGP , BGP MD5 Authentication along with 802.1Q VLAN Encapsulation across entire connection.
How to Secure Direct Connect
The Direct Connect link is used to connect Private network, but this link might be passing through several Service provider device, due to which, the traffic can be sniffed in between on any of the compromised device or even can be compromised on compromised links between devices.
In order to secure your traffic, We can enable IPSec VPN tunnel on direct connect link, which encrypt the traffic passing between on-premises and AWS VPN.
The only Drawback of securing links via IPSEC tunnel is that we have to use same VGW for establishing IPSec tunnels, So Limitations of VGW devices applies here.




LEAVE A COMMENT
Please login here to comment.