EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USGoogle Security
As we know that, Google has already invested a lot in securing its Environment and infrastructure due to its various progressive Security layers. Let’s understand these Security layers one by one.
Securing Low level Infrastructure
Google provides various physical layers of Security – Access to limited number of employees in their DC, Biometric identification, metal Detection, Vehicle barriers etc are some of the security layers, Google use for their Datacenter.
Google also uses cryptographic signatures over low-level components such as Kernel, BIOS, base OS, to ensure server machines are booting with correct software stack.
Securing Service Deployment
It is a code or application that developer has developed and want to run on Google Infrastructure. Each Service that runs on Google Infrastructure will have associated service account identity and is used by client to ensure communication with an intended server. Google also uses cryptographic authentication and authorization for inter-service communication at the application layer.
Securing Data Storage
Google uses secured keys from key management system to encrypt data before it is stored in physical storage, which helps google infrastructure to isolate itself from potential threats such as malicious disk firmware.
Securing Internet Communication
Google LAN and WAN infrastructure needs to be protected from DoS attack. Google uses Cloud Armor, to protect itself from DoS attack. Multi-factor authentication is also very much used in securing Internet Communication.
Operational Security
Google uses Code libraries and framework that eliminates XSS vulnerabilities in Web apps. It also uses various tools to automatically detects security bugs.
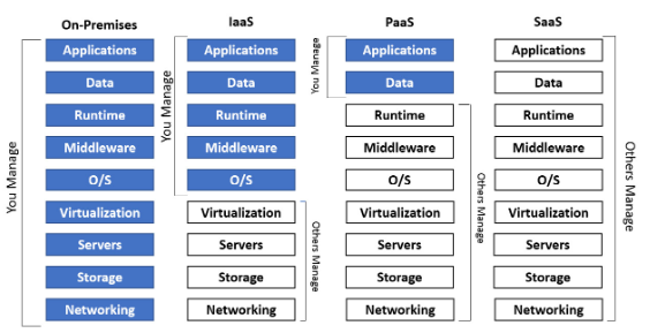
Cloud IaaS, PaaS, SaaS Model:
In Cloud, Not Everything is responsibility of CSP, It is based on model which each Enterprise uses in its cloud Architecture. Below diagram Shows what customer is expected to manage in each service model and what each CSP will be managing.
Cloud Identity
Cloud Identity is GCP service, also called as Identity-as-a-Service (IDaaS) Solution. It is used to provide access to Cloud resources from single pane of glass for Enterprise or organization. It is also uses as a standalone product for domain-bases user account and groups.
Cloud Identity is used to manage users in cloud. In order to use this feature , your domain name must be enabled to receive the email.
There are two editions of Cloud Identity.
- Free Subscription
- Premium Subscription: Offers additional features such as device management , Security and Application management.
Cloud Identity is not managed via GCP console but is managed by Google Admin Console. Using this you will be able to add users, Create Groups, assign members, disable users.
When we want to add users, it is very time-consuming task. In order to overcome this issue, GCP Google Cloud Directory Sync (GCDS) is used. As we know that many organizations use LDAP database such as Microsoft AD, using GCDS, Enterprise can sync Microsoft AD or LDAP AD to Cloud Identity.
This Synchronization is one Way, that is from On-Premises to GCP Cloud.
Cloud Identity is also used for Authentication, GCP stores and manage all authentication and password by default. We can also include two-step verification process by using multi-factor tools.
We can also use Single-Sign-On (SSO), which is a SAML 2.0 based authentication that also include MFA. We can also used Cloud Identity to set password complexity method, in order to align Enterprise Password compliance and Policy.
Resource Manager
With GCP resource manager, Enterprise can create and manage a hierarchical grouping of objects such as Organizational folders and Projects together.





LEAVE A COMMENT
Please login here to comment.