EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USSecure Host Onboarding in Enterprise
This section will talk about different host onboarding technique in SD-Access fabric and well defined approach towards Cisco Zero Trust Model.
End Point Host Mode in 802.1X
802.1X is the port-based authentication method that restricts unauthorized clients from connecting to LAN through publicly accessible ports. An Authentication server validates each client (suppliant) who is just connected to network access device (authenticator) port before making any services available to that client. Once Client is successfully validated or authenticated, 802.1X enabled port goes to authorize state. And if client is not authenticated port goes to unauthorized state.
802.1X port can be configured by four different method, lets discuss each method one by one.
Single Host Mode
In this only one MAC is allowed on switch port. The switch authenticates the port and keeps it in authorize state. If any second MAC is detected, port goes in Security Violation state. It is used when we have strict restriction of connecting only one device on one port.
Multi-Host mode
In this the First Mac is authenticated and all other subsequent MAC’s bypass the authentication and piggyback on first MAC address authentication.
Multi-Domain Mode
In this mode , when PC is connected behind IP Phone and IP phone is connected to port , both IP Phone and PC are authenticate independently making two different domains. Even though they are conenct3d to same port, IP Phone are kept in Voice VLAN and PC are kept in Data Vlan.
Multi-Auth Mode
In this One Client is allowed on Voice VLAN whereas multiple client are authenticated on Data Vlan. DNA Center by default provision multi-auth mode on all 802.1X enabled ports.
802.1X Phased Deployment
AN end goal of Enterprise to design network that uses 802.1X authentication for every client. And this can be achieved or done in phased approach.
Let’s talk about phased approach in which there are two phases defined for 802.1X implementation.
Phase 1: Monitor or Visibility Mode
In this mode, when user is connected, irrespective of its authentication status, Port are open authentication and traffic is allowed.
Below figure shows that before authentication and after authentication all traffic is permitted. Even though user authentication fails, user is able is to access file servers and rest of the resources available on the network.
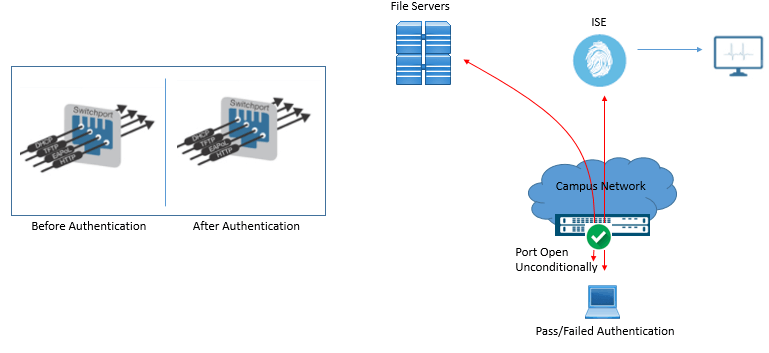
Below command enable monitor mode on the port:
interface GigabitEthernet1/0/10 switchport access vlan 111 switchport mode access switchport voice vlan 112 authentication host-mode multi-auth authentication open -----------------> enables Monitor mode authentication port-control auto mab -----------------> enables MAB dot1x pae authenticator -----------------> enables 802.1X
Phase 2 (a): Low-Impact Mode
This phase has two modes, one is Low-Impact mode and another one is Closed Mode. When the ACL is applied to switch port when Security framework is monitor mode, when then allow very limited network access prior to authentication. Once user or device successfully authenticated, then they get full Network access. Below figure shoes port behavior with low-impact mode.
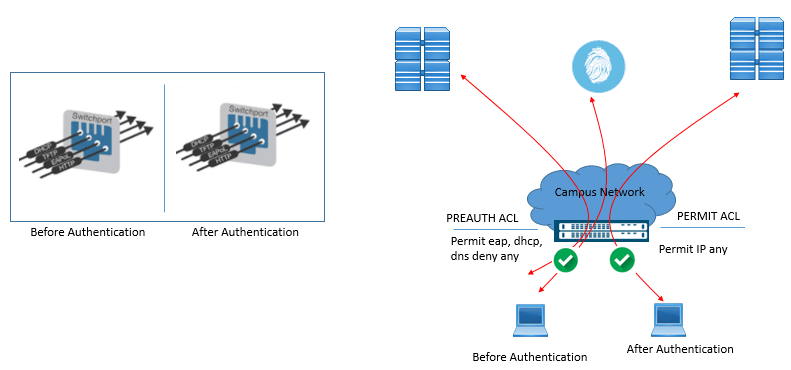
The ACL is configured statically on Switch Access Port, when the authentication & Authorization is successful, policies are pushed down to inform of dACL which are configured on ISE.
Phase 2 (b): Closed Mode:
This mode provides total control over switch-level network access. In this mode, Switch port does not allow any traffic except EAP over LAN (EAPoL) until fully authentication success.
Below figure shows the port behavior with closed mode.
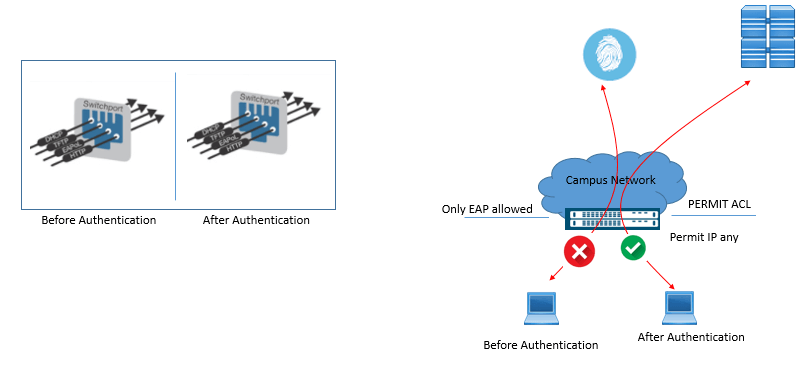
This mode is very much suitable for SD-Access deployment because no default VLAN is assigned at the port level.
Below configuration shows 802.1X port configuration in closed mode.
int GigabitEthernet1/6 switchport access vlan 21 switchport mode access switchport voice vlan 21 no authentication open -------------> enables Closed Mode. authentication periodic authentication timer reauthenticate server authentication port-control auto mab dot1x pae authenticator
Host Onboarding with Cisco DNA Center





LEAVE A COMMENT
Please login here to comment.