EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USISE Integration with DNA Center
Cisco DNA center integrates with Cisco ISE over SSL, pxGrid and External REST API. Here we will see how ISE got integrated to DNA Center.
Certificates in Cisco DNA Center
DNA by default uses self-signed certificates for HTTPS connections and for managing network devices also. The default certificate issued by Cisco System is valid for 1 year and has key size of 2048 bits with SHA-256 RSA Encryption.
Below figure shows DNA center default certificate setting.
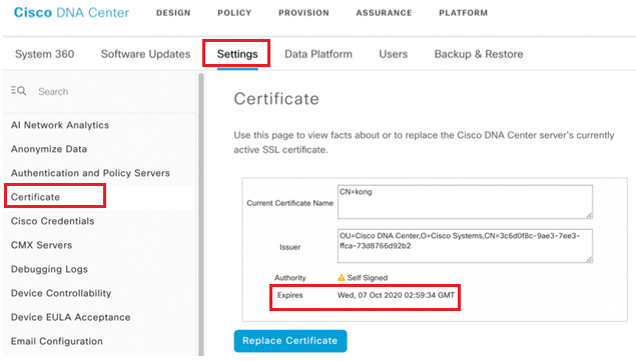
Below figure also provides more details about DNA center self-signed certificate
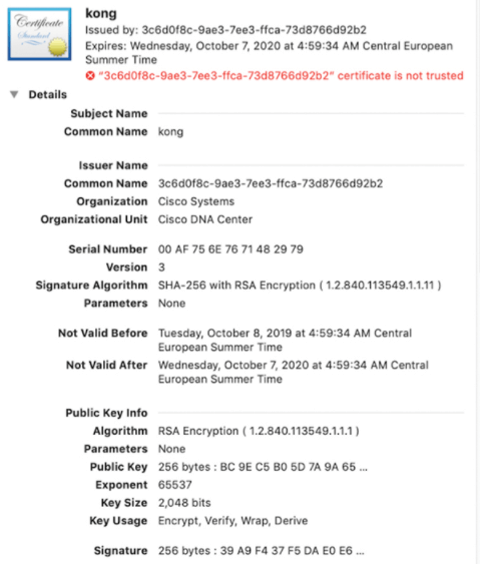
Cisco DNA Center uses Public key Infrastructure (PKI) Certificate Management feature to import, store, and manage X.509 Certificate from trusted CA. The DNA Center supports following import file or PKCS file format.
- 509 certificate (certificate issued by the third-party certificate authority)
- Private key (onlyRSA keys are supported; recommendation is to use a 2048-bit key size or larger)
In this we need to get the valid X.509 certificate and private key from Trusted CA and then replace it with Default certificate of DNA Center. Once it is done all security feature based on X.509 and Private Key will be activated on DNA Center. When Ever any new device request for certificate, DNA Center will now present this certificate to that device.
DNA center supports only one X.509 and Private Key at a time and when second Certificate and its Private keys are imported, the old pair will be replaced.
Certificate on ISE
ISE by default uses its Internal built In CA for Certificates to be used in PxGrid, and uses Self-Signed certificate for admin, EAP, and Portal Services.
Cisco ISE and DNA Center Integration
Before Integration, following prerequisites should be met.
- ISE must run on its minimum Version supported for SD-Access Integration. Refer Cisco.com for more details.
- Enable pxGrid on at least one ISE node, In an ISE deployment there could be maximum 4 pxGrid ISE Nodes. You can assign a pxGrid persona to an existing ISE node acting as a PAN, MnT, or PSN node, but the recommended practice is to use a dedicated pxGrid node to avoid any pxGrid issues caused by other services running on the same node.
- Once pxGrid persona is enabled, it must be in connected state. Cisco pxGrid services use the certificate issued by Cisco ISE internal CA for the services but you can replace it with a third party certificate.
- On Cisco DNA External RESTful Service (ERS) needs to be enabled on ISE. Below figure shows ERS setting in Cisco ISE.
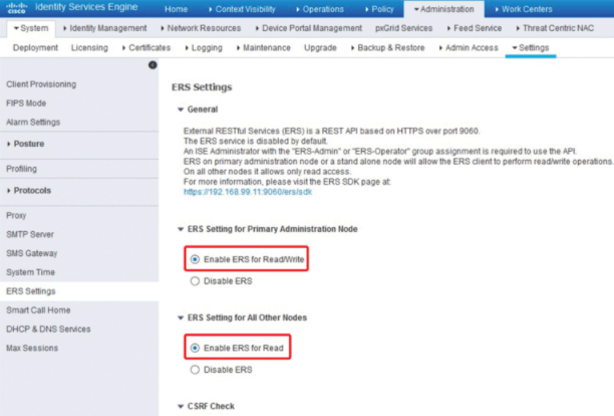
CLI and web Interface Username and password must be configured in Cisco ISE with same credentials of DNA. DNA uses those credentials to login to CLI and web Interface of ISE. Make sure to open TCP port 22,443,5222,8910,9060 for ISE and DNA communication.
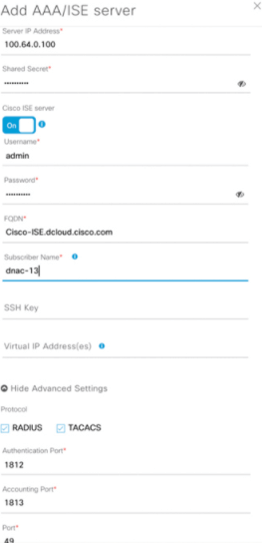
From the web UI of Cisco DNA Center, ISE is added as an “Authentication and Policy Server.” Navigate to System | Settings | Authentication and Policy Servers | Add. In the Add AAA/ISE Server dialog box, the following details are required for ISE integration:
- IP address of ISE PAN in the deployment. Must be Gi0 interface of ISE, NAT is not supported between ISE and DNA
- Shared Secret between network devices and ISE policy Servers.
- Username of ISE using SSH and GUI.
- Password for username for login to ISE via SSH and GUI.
- FQDN of ISE associated with Gi0.
- Enable RADIUS/ TATACS depending whether ISE deployment is used for RADIUS or TACACS
- Authentication port for RADIUS Authentication port 1812.
- Accounting port , default port 1813
- Port for TACACS default 49.
Below figure shows addition of Cisco ISE as AAA Server in Cisco DNA Center.
Once this is done, In Cisco ISE, DNA Center is added as a pxGrid subscriber automatically, if ISE pxGrid setting are configured to automatically accept pxGrid connections. Ese ISE Operator manually needs to accept pxGrid connection request from DNA Center.
Below is the description of Communication flow between Cisco ISE and DNA Center.
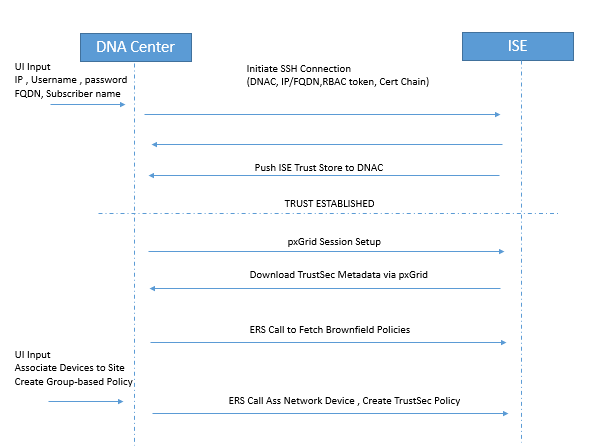
Now to verify that Integration is successful, make sure that ISE status is ACTIVE and System 360 shows ISE nodes as available in DNA Center. Where as in ISE DNA should be listed as pxGrid Client and its should be ONLINE.
Below figure shows Integration success Verification.
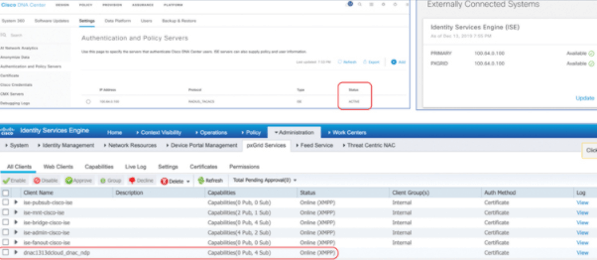
Once Integration is done, DN will be able to read the SGTs and SGACLs that are configured on ISE.





LEAVE A COMMENT
Please login here to comment.