EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USNSX Dynamic Security Group Configuration
Task :
- Create a Dynamic Security Group named DCLessons-DY-Web-SG and match the condition definition based on Platform VMware , VM which has name starting Web , comes under this Security Group.
- Now restrict the web-01a to talk to wab-02a by creating Security policy and by Appling it to above Security Policy Group.
Solution:
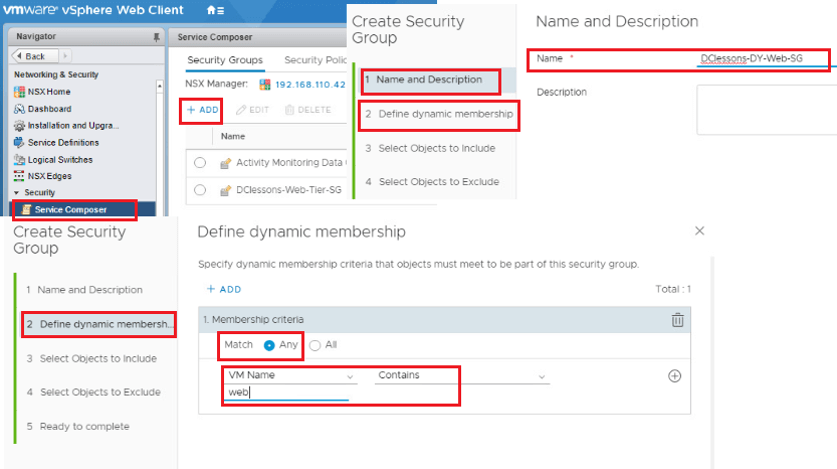
Click the Service Composer on the left panel
- Ensure Security Groups tab is selected
- Select +ADD to create new Security Group
- Enter "Dclessons-DYWeb-SG “ Security Group in the Name dialog box
- Click Next
Open the Object Drop Down box
- Select VM Name from the first Criteria Details drop down list
- Verify Contains is selected in the middle drop down of the page
- Enter web in the dialog box
- Click Finish
Validate Dynamic Security Group Membership
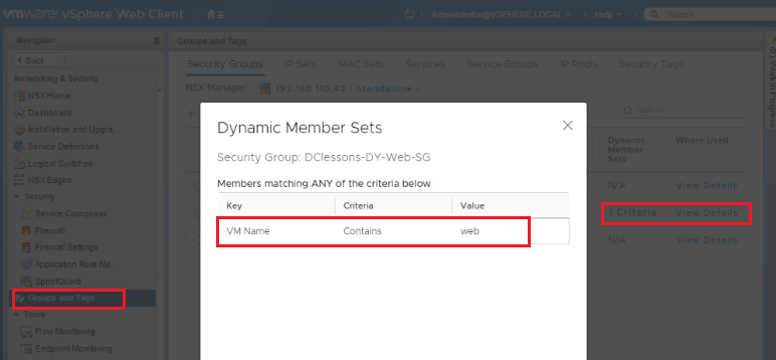
- Select Groups and Tags
- Notice newly created Security Group with NO Static Members
- Dynamic Security group has been defined with criteria
- Double click on "1 Criteria" to see the logic for this dynamic security group
Create a New Security Policy
- Select Service Composer
- Select the Security Policies tab in the Service Composer panel
- Click +ADD to create Security Policy
- Type in "Block Web-to-Web Traffic" in the Name field
- Click Firewall Rules in the left panel
- Click the +ADD icon to add a New Firewall Rule

Comment
You are will be the first.




LEAVE A COMMENT
Please login here to comment.