EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USNSX Architecture & Manager
In order to move data traffic and manage the network there are three different types of planes working on any device. These three different types of planes are as follows:
- Management Plane
- Control plane
- Data Plane
Management plane:
Management Plane are those who are responsible for management traffic of any device .It helps in configuration and management of any network device. Management plane instruct control plane, to enable control plane to provide support for data plane traffic.
Control Plane:
Control plane is used to make data traffic flow from source to destination , It is the control plane who build 2 MAC address table at Layer 2 or Routing table at Layer 3 with help of various routing protocol like OSPF, EIGRP, BGP etc. Control plane supports data plane, all the Routing table are present in RIB table of Network device.
Data Plane:
When RIB is populated, the content of RIB is copied to FIB table which is used by Network device to forward traffic, with the help of data plane any network device send the traffic at exit interface after consultation of FIB.
In short, Management plane instruct the network device “what “it will be doing, Control plane says “how “ it will is going to perform or do that and finally data plane is used by network device to perform or execute the operation.
NSX Architecture:
NSX Architecture is also composed of the three above planes, the following are the NSX main components which are based on three planes and are well shown in below figure:
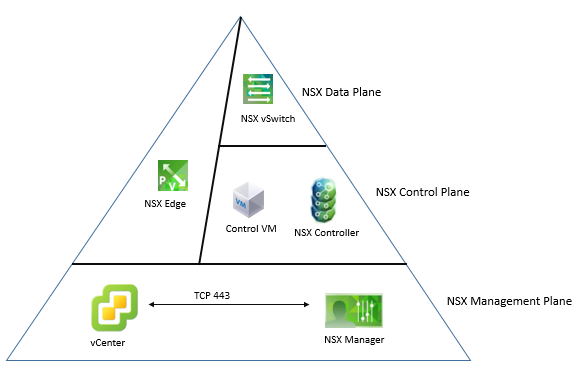
The component of NSX are:
- NSX Manager
- NSX Controller
- NSX vSwitch
- NSX Edge Service Gateway
NSX Manager:
NSX manager is in Management plane of NSX. In NSX vCenter communicates with NSX manager via HTTPS (SSL, TCP Port 443).





LEAVE A COMMENT
Please login here to comment.