EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USNSX Edge VPN Services
IPSEC VPN:
IPSEC VPN is the Method to allow secure and reliable between sites or users over untrusted medium like Internet. IPSEC provide following types of security features:
- Data Authentication: Origin of data should be authenticated source
- Data Integrity: No one can alter data
- Data Confidentiality: No one can see data
To achieve above feature IPSEC uses various types of Authentication, Encryption protocols which should be negotiated before IPSEC tunnel are created and once IPSEC tunnels are created between peer, by using these above protocols , data is encrypted and sent to destination securely.
All these process is handled by a process called IKE (Internet KEY Exchange) and it has two phase.
- Phase 1 validates the two endpoints that want to be IPsec VPN peers and establishes a secure channel between the two.
- Phase 2 establishes the secure channel for the actual IPsec VPN traffic.
Below figure demonstrate the packet walk on site to site VPN and then we will see how IEK phases happens:
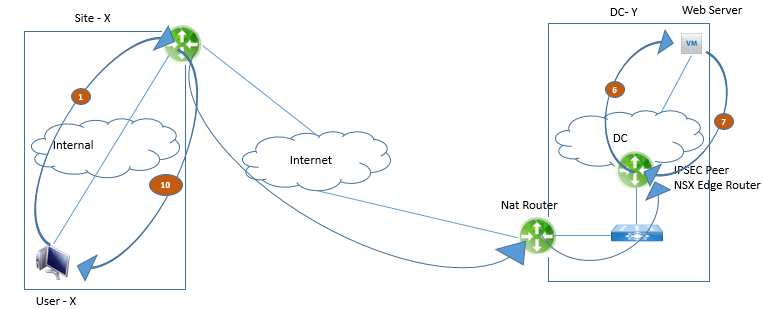
Traffic from user-X toward the web server goes like this:

Comment
You are will be the first.




LEAVE A COMMENT
Please login here to comment.