EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USNSX DFW Configuration
Task:
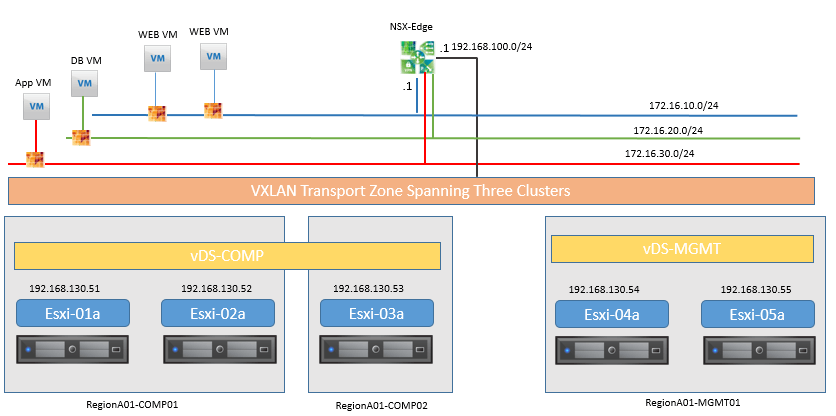
- Verify that web-01a is able to reach to web-02a , app-01a and db-01a Subnet for these three servers are
- Web : 16.10.0/24
- App: 16.20.0/24
- DB: 16.30.0/24
- Create a 3-tier Security Group named DCLessons-Web-Tier-SG and select object type VM , and then select both web-01a, web-02a
- Create Three Tier Access Rule name DClessons-3tier-rule with source any, destination DCLessons-Web-Tier, and enable Service HTTPS, SSH
- Create another new Rule, to allow Web Security Group to allow access to App Logical Switch over port 8443.
- Create Another Rule to allow App-Logical Switch to access DB-logical Switch DB switch over port 80.
- Test the connectivity
Topology:
Solution:
Login to the vSphere Web Client
- Test 3-tier VM to VM connectivity using Putty | Click on the PuTTY shortcut on the desktop taskbar
- Select web-01a.corp.local
- Click on Open
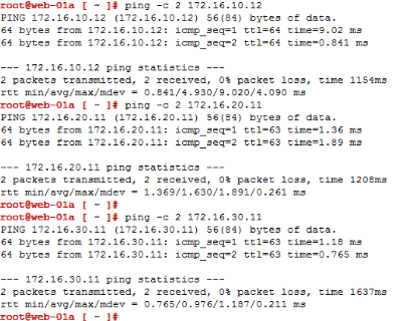
First you will show that web-01a can Ping web-02a by entering :
- ping -c 2 172.16.10.12
Now test connectivity between web-01a to app-01a and db-01a:
- ping -c 2 172.16.20.11
- ping -c 2 172.16.30.11
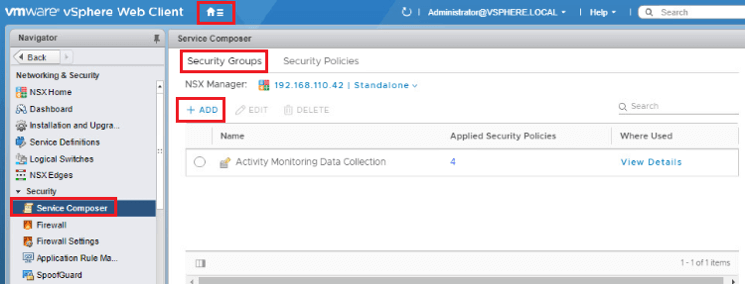
Create 3-Tier Security Groups
- Click Home | Networking & Security | Click on Service Composer.
- Select Security Groups. Note: there may be existing security groups to be used in another lab module
- To add a new security group click the + ADD icon
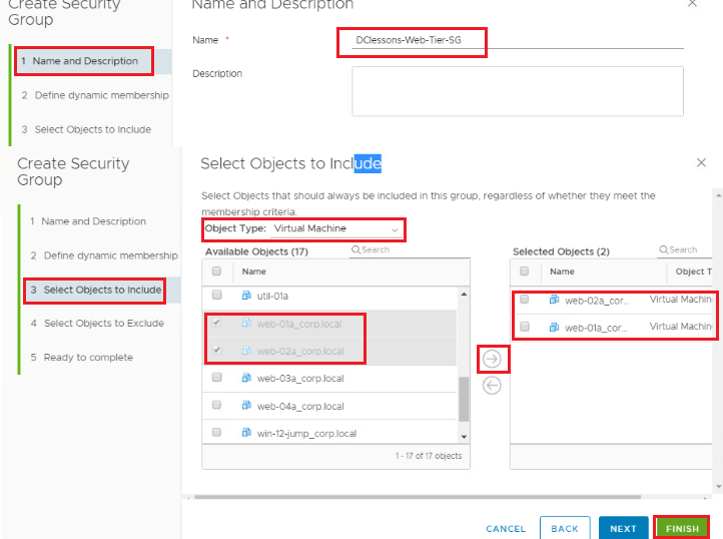
- Once selecting the + Add then choose Name this first group "DClessons-Web-Tier-SG"
- Click the "Select objects to include" section
- Pull down the Object Types and select Virtual Machines
- You can filter by typing "web" into the search widow
- Select web-01a
- Click the Right Hand arrow to push the VM to the Selected Objects window
- Repeat for web-02a
- Click Finish
Create 3-Tier Access Rules
- On the left hand menu, select Firewall
- In middle of screen select the + ADD SECTION button to add another Firewall
- section above the "Flow Monitoring & Trace Flow Rules-Disabled by Default (Rule 1)" row.

Comment
You are will be the first.




LEAVE A COMMENT
Please login here to comment.