EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USNetwork Address Translation:
NAT is method of changing the Source IP of destination IP of packet. The Router that does the NT translation is called as NAT Router.
NAT router that changes the Source IP is called as SNAT and the NAT Router that changes the destination IP is called is DNAT.
If an ingress packet arrives in the router matching a particular source IP, the source IP is changed for a predetermined one and then the packet is sent on its way. The same logic applies if doing DNAT. The NSX Edge supports SNAT and DNAT.
The configurations for applying NAT are done via NAT rules. For NAT rules to be effective, an interface must be identified, and the direction of the packet flow is based on this interface. Packets arriving at this interface are considered ingress packets, and packets going out of this interface are considered egress packets. If an SNAT rule is applied to an interface, the source IP address of the ingress packet is changed. If a DNAT rule is applied to an interface, the destination IP of the egress packet is changed. The NAT router keeps a NAT table of all translated IPs so return traffic in the flow can have the NAT reversed. The return traffic must come through the interface that has the NAT rule that was applied to the flow.
NSX EDGE Load balancer:
NSX Load Balancer is the method of load balancing the destination traffic among various internal servers when the traffic hits on VIP.
The VIP is mapped in the load balancer to an application that represents the service, called the application profile. The application profile is load balanced to a list of servers running the workload, called the server pool. The IPs in the server pool act as the equivalent of the translated destination IPs in a DNAT rule. Traffic that matches the criteria included in the application profile triggers ingress traffic to be load balanced.
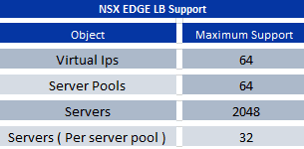
Once a VIP is mapped to an application profile and server pool, it is called a virtual server. The NSX Edge can have virtual servers that trigger load balancing based on Layer 4 information, TCP and UDP, Layer 7 information, and HTTP and HTTPS. Below Table shows the maximum number of VIPs, server pools, and servers that the Edge supports.
Below figure shows an example of an NSX Edge load balancer. The Edge has a VIP of 10.10.10.3, a server pool that includes IPs 10.10.11.3, 10.10.11.4, and 10.10.11.5, and an application profile that matches destination TCP ports 80 or 8080. In Figure, any user that wants to reach a web page on ports 80 or 8080 at 10.10.10.3 is redirected to one of the three servers in the server pool. The redirection happens by doing a DNAT on the user packets. The source IP of the packets is not altered.
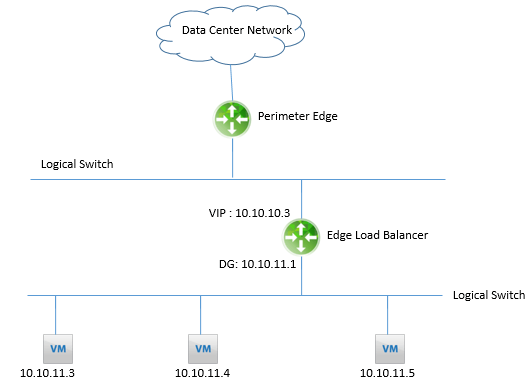
The load balancer configuration shown in above Figure is called In-Line or Transparent Mode. When deploying the load balancer in Transparent Mode, the Edge must have an interface directly connected to the segment where the members in the server pool are located, and the Edge must be the default gateway for the servers.





LEAVE A COMMENT
Please login here to comment.