EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USLAB NSX Edge Service Gateway Configuration
Task:
- Configure and deploy a new Edge Services Gateway and Configure Load Balancing on the Edge Services Gateway
- Verify the Load Balancer's configuration and test the load balancing traffic.
Topology:
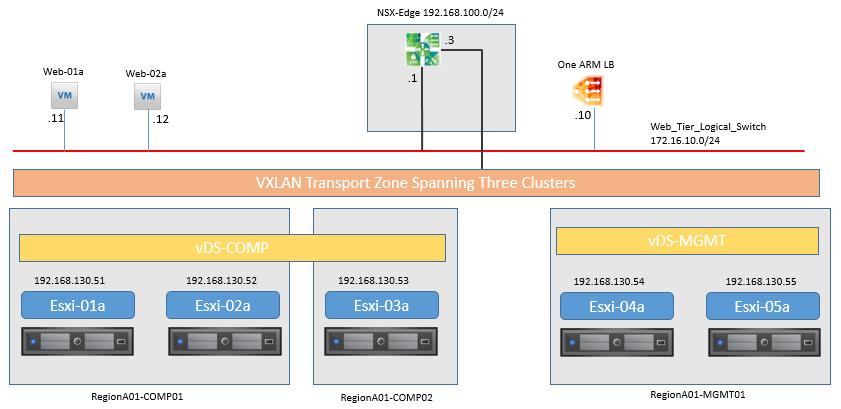
DEPLOY EDGE SERVICES GATEWAY FOR LOAD BALANCING in ONE ARM MODE
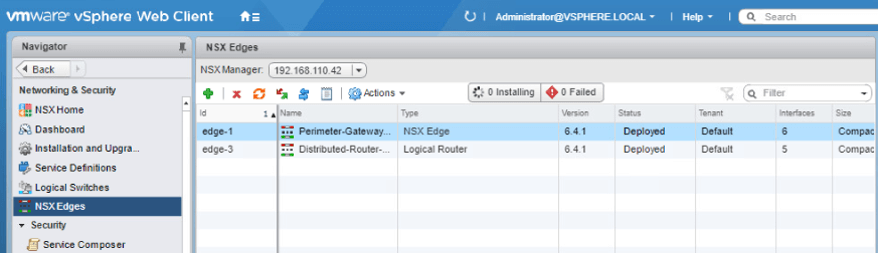
- Click on Home icon | Click Networking & Security |Click NSX Edges | Click the Green Plus icon.
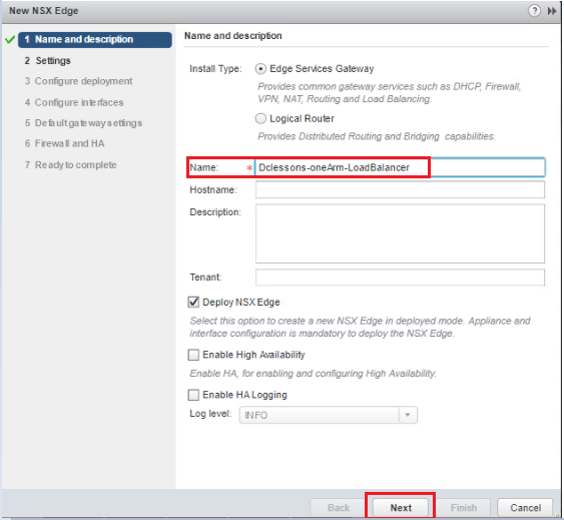
- Enter Dclessons-OneArm-LoadBalancer as the Name | Click Next.
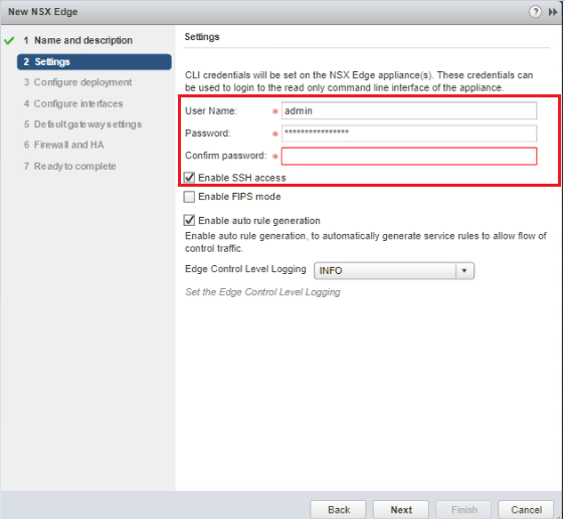
- Enter XXXXXXXX as Password and confirm it again
- Check Enable SSH access option and then click Next
Click Green Plus icon | Select RegionA01-MGMT01 as Cluster/Resource Pool.
- Select RegionA01-ISCSI01-COMP01 as Datastore | Select esx-05a.corp.local as Host | Click
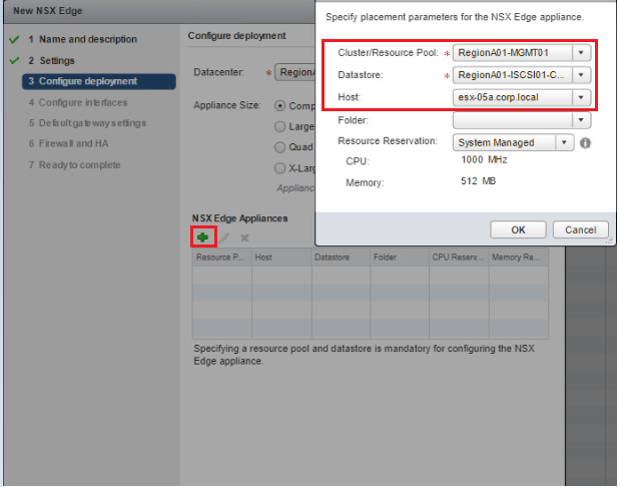
Click Next.

Comment
You are will be the first.




LEAVE A COMMENT
Please login here to comment.