EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USNSX Layer 2 Extention
Layer 2 VPN is used to extend the Layer 2 Broadcast domain, and can be used for following:
- Extend a Layer 2 between a remote office and the main office.
- Extend a Layer 2 between virtual machines in different data centers.
- Extend a Layer 2 between a private and a public cloud.
The NSX Edge supports Layer 2 VPN over Secure Sockets Layer (SSL), port TCP 443. If the NSX Edge is extending a VLAN, the VLAN must be configured in a distributed portgroup.
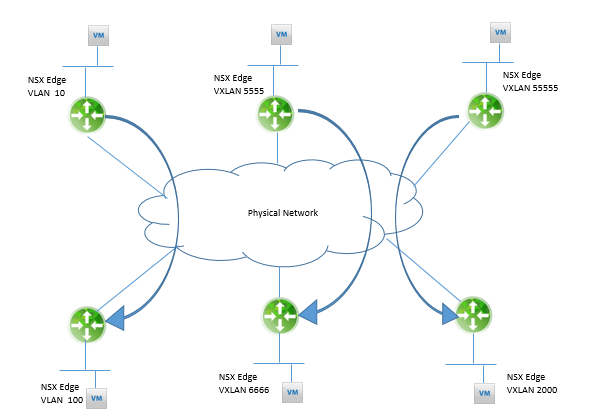
Below figure shows logical view of multiple pairs of NSX Edges creating a Layer 2 VPN between VXLANs, VLANs, and a VXLAN and a VLAN.
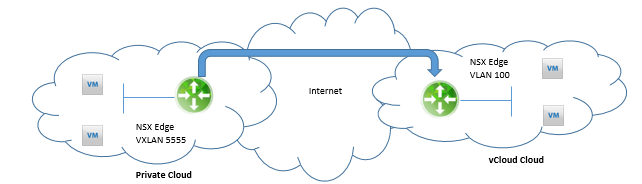
The NSX Edge can also be used to extend a VLAN between a private cloud and vCloud Hybrid Services, vCloud Air as shown below:
The NSX Edge supports Layer 2 VPN in a point-to-point deployment, and it must be with another NSX Edge in a server-client relationship
The NSX Edge can be used to extend a VLAN or VXLAN between two data centers even if the NSX Edges are managed by different NSX Managers or one of the Edges is a Standalone Edge.
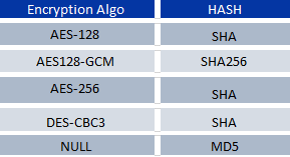
The encryption algorithms supported by the NSX Edge for Layer 2 VPN. The Layer 2 VPN Server dictates the encryption algorithm upon tunnel negotiations with the Layer 2 VPN Client.
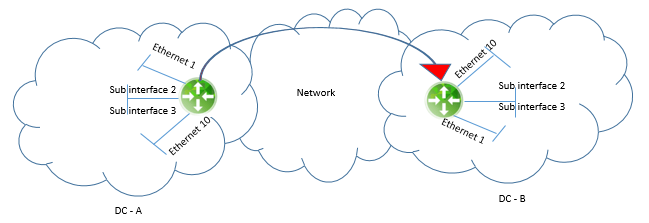
An NSX Edge can only support being either a client or a server at one time, but not both, and requires a Trunk interface with sub interfaces. A pair of Edges can only do a Layer 2 VPN for 200 pairs of Ethernet domains, as shown in below figure. The path from the Layer 2 VPN Server and the Layer 2 VPN Client must have an MTU of 1600 or higher.
Layer 2 VPN Traffic Flow:
To understand the packet walk, let’s suppose the first ping sent from Virtual Machine ServerApp02 to ServerApp01. To understand we have to assume the following:





LEAVE A COMMENT
Please login here to comment.