EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USSSL Introduction
SSL was first developed by Netscape Communication in 1994, to secure communication over WWW. After SSL 3.0 Version, IETF started working to make open standard protocol TLS (Transport Layer Security) which is more secure than SSL and proving same function as SSL, and used SSL 3.0 as basis.
TLS and SSL both secure HTTP and they are also used to secure application layer protocol like FTP, LDAP, and SNMP.
Each F5 Appliance comes with SSL accelerator card, which handles SSL encryption, and decryption. This helps F5 to perform both SSL key exchange and bulk crypto work using its hardware, which makes F5 work faster. These all device requires license that states how many SSL transaction per second it handles.
SSL Terminology
Below are some BIG-IP F5 SSL Configuration & Terminology used to understand the SSL Concepts.
Certificate Authority
Below are some Functions of Certificate Authority.
- CA verify the identity and authority of the requestor before issuing a Certificate
- CA also verify the ownership of resource for which the certificate will be issued.
- Once the Identity and Authority of the requestor is successfully verified by CA, CA issue a certificate for a user, Computer, Network Device, or Service Certificate. Based on the certificate type requirement, certificate will have different set of options.
- CA Also manages Certificate Revocation
Certificate Signing Request
A certificate Signing Request is the encoded text that is provided to CA when we apply for a SSL Certificate. A CSR is generated on the device on which certificate will be installed.
When a CER is generated on F5, A Key is also silently generated first, the information present in CSR is used to by CA to create the matching certificate, and once Certificate is issued, we can import that certificate to that particular device. CSR contain information which will appear in final Certificate like Organization name, Common name (domain name), Locality, Country, Email Address etc.
When a CSR is generated, its corresponding Private Key never leaves the device, below is the complete process of generating a Certificate and key pair using a CSR as follows.
- Generating a CSR on Device: CSR will contain all necessary information, in order for CA to issue a Certificate, this will also create the Matching key pair.
- Upload the CSR to CA: CA can be internal or external, once CSR is uploaded to CA, CA will use the Information present in CSR to create a matching certificate that you can download.
- Importing a Certificate to the device: Once Certificate is created, Certificate is to be imported from CA, and will be imported to device, where Certificates needs to be installed.
SSL Certificate Management from F5 Web-GUI
BIG-IP F5 SSL Configuration Profiles used to manage the SSL traffic going inbound and outbound. Before SSL Profile is created, it is necessary to import the SSL & Key pair to Device. SSL Certificate can be either Self Signed or created by trusted certificate Authority.
A self-Signed Certificate is created on F5 and is signed using own Private Key. Self-Signed Certificate are not trusted by web browser because they are signed by F5 now by trusted CA. Whereas Certificate Created by CA is trusted by Web-Browser because , they are validated and signed by trusted CA private Key.
All the certificate and keys are stored in F5 device and are found under system | File Management | SSL Certificate List
SSL/TLS Offloading
F5 has ability to perform a SSL Offloading. F5 system has an SSL accelerator card, which helps in encrypting & Decrypting SSL traffic very fast.
SSL Offloading is also referred as Client Side SSL Termination as SSL Session is terminated on BIG IP System.
Below are some benefits of SSL Offloading
- It avoids End-Server SSL processing Overhead.
- Easier SSL Certificate Management. Only a single Certificate is needed for one pool of end servers
- Helps in viewing & manipulating the traffic at application protocol level.
Below figure displays how traffic flow when SSL offloading is used.
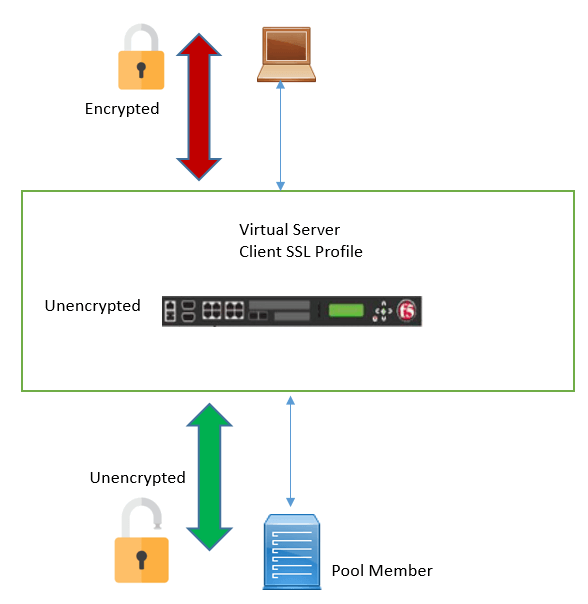
Client SSL Profile
Client SSL Profile is used to activate SSL offloading. In Client SSL Profile, both Certificate & key are used to encrypt and decrypt traffic. Once Profile is ready, it is assigned to Virtual Server.
A Custom Client SSL Profile is created to configure Certificate Key chain setting. This Custom SSL profile will also inherit its setting from default Client SSL profile, so in order to break this inheritance, we must enable the Custom setting specified in below figure
F5-7.2 (From Lab GUI)
Once this setting is enabled, we will be able to specify the certificate and Key that we want to use. Now once Custom SSL Profile is created, it can then be applied to Virtual Server and then SSL offloading and terminating SSL Session of F5 can be performed.
SSL Bridging
Some business organization have high security requirements and they do not allow unencrypted traffic to their real servers, and want encrypted traffic end to end.





LEAVE A COMMENT
Please login here to comment.