EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USExternal Traffic Enforcement
When traffic is enforced to External network and is externa to Fabric, there are following options available for enforcement of policy based on SGT.
- Enforce policy at Fusion Firewall serving as an SGFW.
- Enforce policy either at destination or somewhere in the path.
- Enforce policy at Border node.
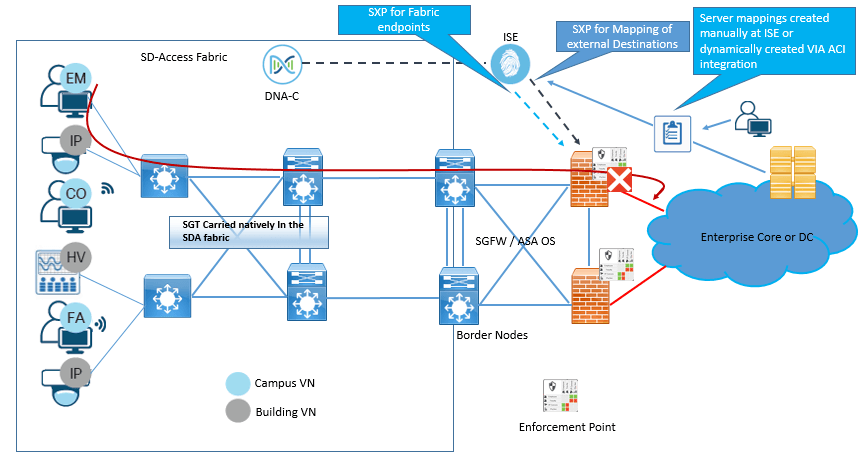
Whatever option is to be taken in to consideration, SGT propagation for fabric endpoints is propagated in to VXLAN header for traffic reaching at border node. Now at border node SGT of destination is not known, so Cisco ISE advertises the Destination SGT by SXP, which is only applicable to Cisco Router and Switch and not on Cisco Firewalls, as Cisco FW are not supported on border node.
Policy Enforcement at Fusion Firewall acting as SGFW.
In this option, for all traffic leaving the SD-Access fabric, Policies are enforced at Fusion SGFW. In this option ISE will advertise IP-to-SGT mapping of authenticated endpoints to SGFW. Now at FW it is to be decided that policies will use SGT of destination or IP address of destination.
Now if you are using ASA OS, any combination of SGTs or IP address can be used regardless of source & Destination.
If policy consist of source SGT and Destination IP address at SGFW, with any OS, Source SGT is propagated by SXP or pxGrid between ISE and SGFW and then policies can be easily created.
Now If SGFW is running ASA OS, and policies to be created between Source and Destination SGT only, whether for External network or internal fabric Network, IP-to-SGT mapping of destination needs to be advertised to SGFW with SXP.
Rule: Enforcement of policy based on SGT will happen only at first network device that has IP-to-SGT mapping for destination.
There are two ways to populate destination IP-to-SGT mapping on SGFW running ASA OS .
- Static Mapping in SGFW
- Advertisement via SXP
Recommended approach is to configure these mapping manually on ISE and then advertise then to SGFW.
IF you have DC with ACI as SDN solution , ISE can be integrated with APIC , which enables dynamic creation of IP-to-SGT mapping for the servers in ACI fabric and these mapping can be automatically advertised to SGFW.
Below figure explains about SGFW enforcement for external traffic.
Policy Enforcement at Destination or in path to destination.
When Enforcement is to be done at destination or in path to destination, The IP to SGT mapping of destination endpoint must be present to device where enforcement has to be enforced. If Enforcement is to be done at network device where destination is attached, then the destination must be classified or associated to SGT. Classification or IP-to-SGT mapping can be done locally on network device by 802.1X or MAB, or Statically through IP-to-SGT, Subnet-to-SGT, VLAN-to-SGT, and Port-to-SGT via CLI. Or destination mapping can be created on ISE and advertised through SXP to destination switch.
But if Enforcement of policies is required on device which is in path to destination, SXP advertisement or static mapping at intermediate node will be required.
Now to advertise the IP-to-SGT mapping at enforcement point , either enablement of Cisco TrustSec Inline tagging at egress from the fusion FW or use SXP to propagate the SGT of source to destination or enforcement point.
In Order to support Inline tagging all links between Fusion FW and enforcement point for destination must be manually enabled for TrustSec and is done hop by hop basis.





LEAVE A COMMENT
Please login here to comment.