EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USUnderstanding Segmentation Overview
In this SD-Access Segmentation overview, we will learn about all concepts that are required for Segmentation in SD-Access fabric.
Virtual network:
Virtual network help in achieving isolation between traffic between different VNs. In SD-Access traffic is identified in particular VN by VNI which is present is VNI field of VXLAN header.
This is shown in below figure
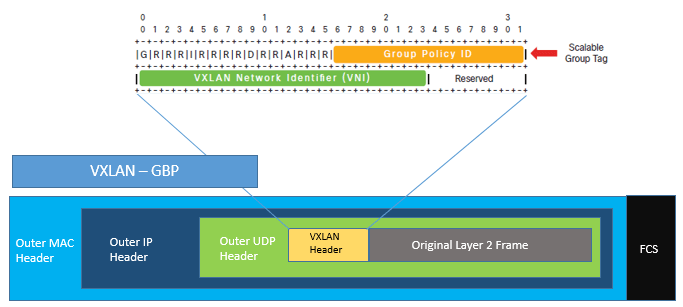
SD-Access does not require separate routing table per Virtual network. In SD-Access fabric LISP is used to provide control plane forwarding information. For traffic going external to fabric, border node is used to directly map the VN to VRF instance and isolates communication between them by using separate routing table per VRF.
By default DNA Center has a single virtual network called DEFAULT_VN and all endpoints belong to this virtual network. Once the ISE is integrated to DNA Center, default VN is then populated with scalable group from ISE. Now these scalable groups can be used in DEFAULT_VN or new virtual network can be defined.
Scalable Group Tags:
SGTs are 16 bit group identifier which is associated with scalable groups. These Scalable groups are mostly based on business requirement, Functions or Object similarity. By default large number of predefined scalable groups along with associated hexadecimal tag ID is present. A new Scalable Groups along with Tag ID of business choice can also be defined.
DNA Center is used to define SGTs and is used to map Virtual network based on organization requirement. These SGTs are not propagated hop by Hop in SD-Access fabric, but with the help of TrustSec inline tagging, it can be carried within VXLAN header along with VNI.
In SD-Access, Segmentation can be done by two method with help of VN and SGTs.
- Macro Segmentation
- Micro Segmentation.
By Default all Endpoints within VN are able to communicate each other, achieving micro-segmentation with in VN will prevent Endpoints to communicate with each other. Whereas Macro Segmentation means Endpoints will not talk to each other via different VNs. As each VNs has its own routing instance, an external device (Layer 3), non-fabric device commonly called as Fusion router or firewall is used to provide inter-VRF forwarding necessary for communication between different VNs.
At this Fusion router Policy required for communication between VNs and also Policies can be defined at DNA Center and then is enforced for traffic within VNs based on SGTs. These Policies are configured on DNA center will be then sent to ISE via REST API. ISE will then updates policy to the Edge Nodes only whose SGTs are associated with attached device. Enforcement of policies only occurs at egress where destination is attached.
Below figure describes use of fusion Firewall for communication between VNs as well as traffic destined outside to fabric network. The Policies are configured in this FW is based on IP ACL not based on SGTs
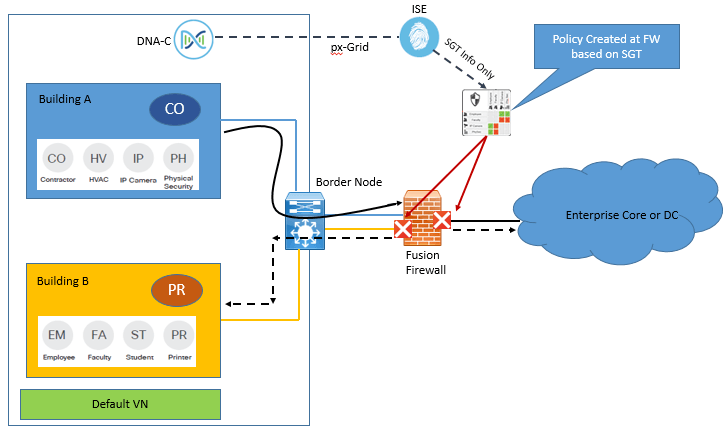
In the above figure traffic source from Building A and destined to Campus B or external to fabric, can either be forwarded or dropped based on rules implemented on FW based on SGTs.
With Help of Standard ACL or group based policies with SGTs firewall rules are populated to control traffic between endpoints.
Using TrustSec on Firewall has following benefits.
- It provided ability to define and enforce policies for either externally bound traffic or Inter-VN traffic based on SGTs.
- It helps in propagating tagged traffic beyond SD-Access fabric if Inline tagging is enabled in your network.
When Firewall used to define SGTs based policy or rules, these are called as Scalable Group Firewalls (SGFWs).These SGFW only receives the names and Scalable groups tags value from ISE and don’t receive any actual policies or rules. SGTs based rules are defined locally at SGFW either via CLI or with help of any other management tools.
An important point to note is that, if you want to enforce policy at SGFW using SGTs only, the destination IP-SGT mapping needs to be required also.
Propagating Scalable groups tags for Enforcement:





LEAVE A COMMENT
Please login here to comment.