EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USAWS Use-cased & Security Solutions
In this section we will provide Some use-cases and will discuss the possible solutions related to these use-cases.
Use-case 1:
When a Series of failed login attempt indicating an active intrusion threat.
Solution:
In order to provide the Security Solution related to able use-case, below are AWS Services needs to be integrated.
Amazon Cloud Watch:
This Services Not only monitors the AWS resources and application in real time, but also collect and track metrics, logs and events.
Amazon Cloud Watch alarm service send notification or automatically make changes to resources that are being Monitored based on rule that you define.
AWS Cloud Trail:
It is used to record, document the history of AWS API calls and related events in your account. AWS Cloud Trail delivers these records in a log file to the Amazon S3 specified by you. Now you can also configure AWS Cloud Trail to encrypt logs and generate an integrity digest file.
IAM:
This service is used to securely control access to AWS resources. IAM is used for WHO, HOW and WHAT resources can be accessed.
AWS Lambda:
AWS Lambda, lets you run Code without provisioning or managing servers. It executes your code only when it is required and it scales automatically. AWS lambda is used to run your code in response to events generated.
AWS Simple Notification Service:
It is used for delivery of message to subscribing endpoints. It enables communication between publishers and subscribers. Publishers like Cloud Watch Alarms communicates with Subscribers asynchronously by producing and sending message to a topic. Subscribers like AWS lambda functions, receive the message when they are subscribed to the topic.
Below Figure describes the Architecture for mitigating the SSH multiple login attempts.
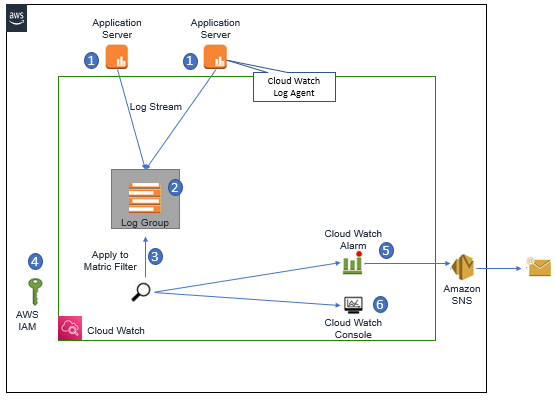
Solution Description:
Let’s suppose, your application runs on Linux Instances. Now on each instance you run the Amazon CloudWatch log agents and also has an IAM instance Role assigned to EC2 instance, Inorder to allow the agent to write to Amazon CloudWatch.
As soon as SSH daemon updates its logs, information is sent from the instance to Amazon CloudWatch logs.
Logs for each instance are represented in Amazon CloudWatch logs as a unique Log Stream and these log stream are aggregated in to logs group.
Once Logs groups are done, we need to create a metric Filter. Matric Filter expresses how Amazon CloudWatch should Extract information and correct observation from Log groups and represents them as data points. Here we need to configure the metric filter to match the specific strings sequence in log file that indicate a login failure.
Here we also specify the Amazon CloudWatch Alarm to indicate the when allowed number of failed login attempts happened per unit time and then you must specify an Amazon SNS topic on which to publish the alarm.
In order to automate the response, we must subscribe the AWS lambda function to alarm topic in SNS. The Subscribed Lambda function contain your code for processing the Source IP address, that has started SSH logins and using an IAM role, for AWS lambda execution. Lambda will update the VPC network ACL to deny incoming requests from those invalid sources.
Use-Case 2:
Detecting Network Anomalies for understanding traffic flow patterns. Example : Sudden changes in Top Talkers , Denied Data Flows , Unused Security Groups and Ports.
Solution Components:
Below are solution components used to facilitate this use-case.





LEAVE A COMMENT
Please login here to comment.