EMAIL SUPPORT
dclessons@dclessons.comLOCATION
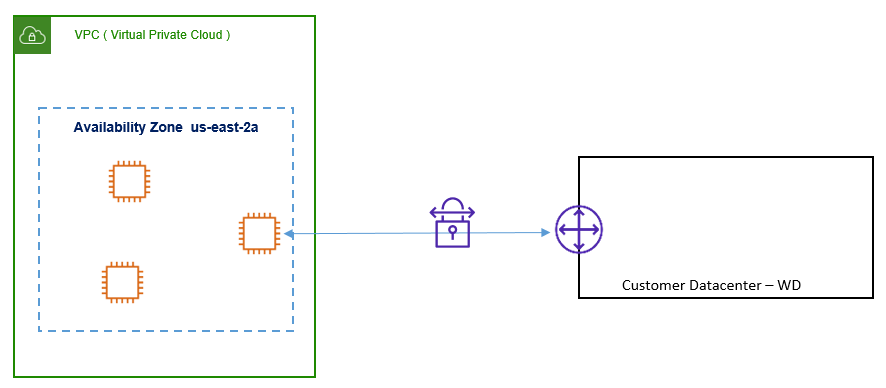
USAmazon EC2 VPN Termination Endpoint
Instead of using VGW, we can also use the EC2 instance running VPN Software as VPN termination point.
Below are some scenarios, where we can use the EC2 instance as VPN termination point.
- Requirement of special feature like advance Threat protection, Transitive Routing Capabilities.
- On-Prim Router has DM-VPN or GRE VPN Setup
- Requirement of Complex Networking use cases like connecting two network with overlapping CIDR ranges, Multicast traffic between Two Instances, Transitive Routing.
Below figure describes the VPN termination in an Amazon Instance.
High Availability
In order to achieve High Availability, you must use two EC2 instance (Primary & Secondary) and use the VPN termination in an active and standby mode.
Now if want to achieve the failover from primary EC2 instance to Secondary, you have to automate it by using script. The Script will detect the failure of VPN tunnel and will make necessary changes to subnet route table to point to secondary Instance.
Below figure describes High Availability mode, when VPN is terminated to two EC2 instance using automated failover.
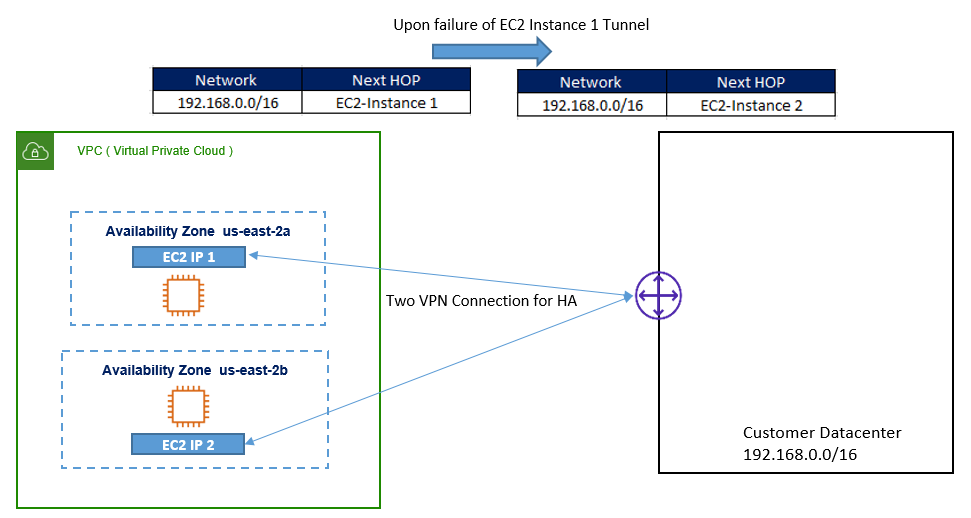
As soon as script have done changes to route table, data traffic will be shifted from primary EC2 instance to Secondary EC2 instance VPN tunnel.
Monitoring
Matrices of EC2 Instance like – health, network traffic, can be easily watched using Cloud Watch. Cloud Watch will not be able to watch the OS or Software related issue like VPN Software, OS etc.
Vertical Scaling
At the time of VPN Termination on EC2 instance, we must choose EC2 instance with good configuration.
If we will go for Vertical Scaling, we may require downtime, as new EC2 instance needs to be restarted. In that case, we should use EC2 instance in Active/Backup mode, to avoid downtime.
After a certain threshold, VPN throughput becomes fairly constant even with an increase in the Amazon EC2 instance size. This is because there is a limit in IPSEC Packet processing performed in Software.
So Inorder to increase the VPN throughout above this threshold, we can offload the encryption to multiple EC2 instance. Here you will have to configure one EC2 instance as next hop for all VPN traffic. This EC2 instance, which is acting as next hop of all VPN traffic will not be terminating any VPN tunnel, but responsible for load balancing traffic to a fleet of EC2 instances.
There are two ways to perform this scenario:
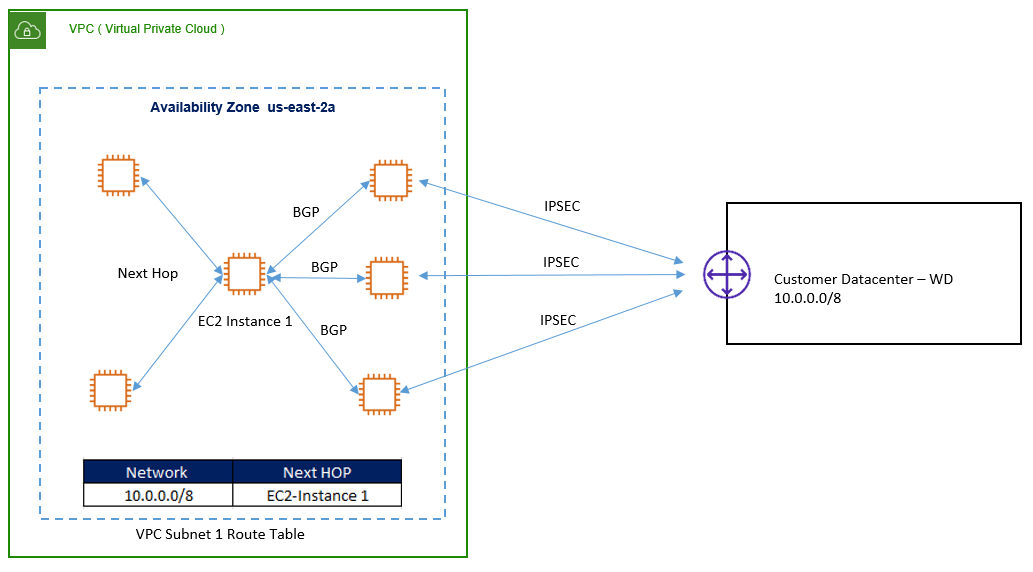
Single Availability Zone:
In a single subnet, Central EC2 instance will run BGP for L3 load balancing & Routing with fleet of EC2 VPN instances, so that for all VPN traffic, Next hop would be VPN instance for all remote network.
Below figure describes the Vertical Scaling with load balancing – Single Availability Zone.
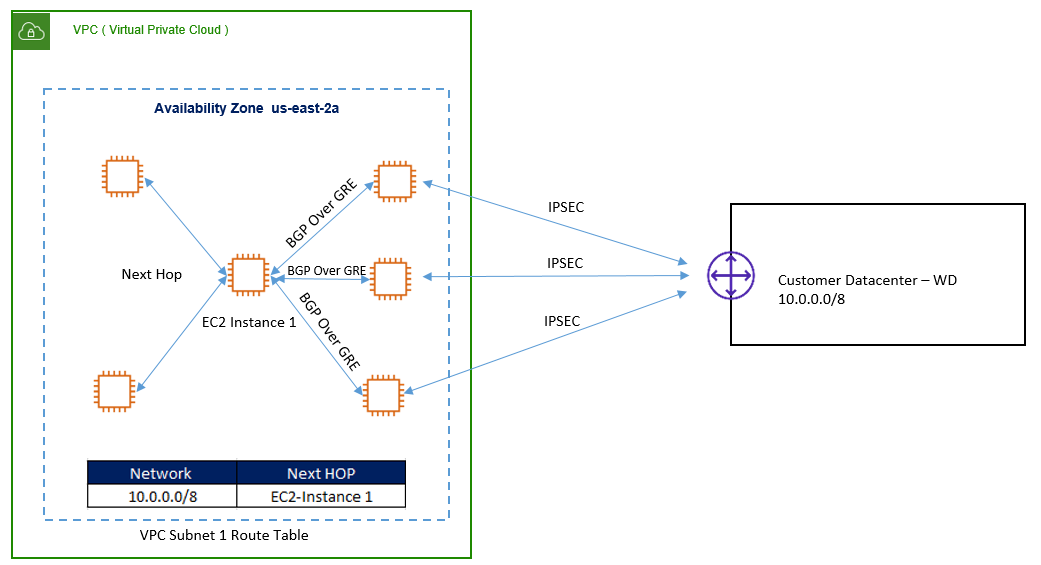
Multiple Availability Zone:
Here, VPN EC2 instance are placed in different AZ and establish GRE tunnel to central EC2 instances.
GRE tunnel are used to establish BGP peering with an instance in a different subnet.GRE tunnel creates a virtual network connecting two instances in same virtual network.
Here, for all remote network, next hop will be central EC2 instance as described in below figure.
Horizontal Scaling
In the horizontal Scaling, we can launch Multiple EC2 instances and can using all in Active / Active Mode. Here we can use one VPN instance as next Hop for particular Prefix.





LEAVE A COMMENT
Please login here to comment.