EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USVPC Components
Amazon VPC Consists of the following components
- Subnets
- Route tables
- IP Addressing
- Security Groups
- Network ACL
- Internet gateways
- NAT Instance & NAT Gateway
- Egress Only Internet Gateways
- Virtual Private network
- VPC Endpoints
- VPC Peering
- Placement group
- DHCP Option Sets
- Amazon DNS Server
- VPC Flow logs
We will Discuss these options one by one and understand the basic concepts. And Each Topic will be discussed in Point wise.
Subnets
- It is a network segment resides with in a single Availability Zone and can span across multiple AZ.
- When we create a subnet, we have to specify the AZ and should allocate the contiguous block of IPv4 address from VPC CIDR block.
- When a Subnet is created, AWS reserve first four IP and last IP address of every subnet for internal networking.
- Within VPC Broadcast and Multicast packet are not forwarded.
All Subnets which has been created, can be categorized in public, private or VPN Subnet only. Even though you can categorize a subnet as public or private or VPN, the internal IPV4 address will always be private only.
- Public Subnet: Subnets whose associated route table consist a route entry pointing to internet gateway
- Private Subnet: Subnets whose Route table does not contain route to an internet gateway, but may contain route to NAT Instance ort NAT gateway.
- VPN-Only Subnet: Subnet whose associated route entry points to VPC VGW.
Default VPC contains one public subnet in every AZ with in a region.
Route Tables:
- Each Subnet in VPC contains a logical construct called Implicit Router and each Router have Route Table Associated to it- said to be Subnet Route table.
- Subnet Route table contains Route entries of that particular Subnet.
- Each Route table has entry of Destination and a target. Destination can by any IPV4 Subnet, Prefix list and target can be Internet Gateways, NAT Gateways, EIGWs, VGW, VPC End Points, VPC Peer, EIN.
- Each Route table, also contains entry of defined CIDR ranges with a target of “Local” and these entries cannot be removed.
- A Custom Route table can also be created with specific routing policies and can be further associated to one or more subnets.
- Each VPC contain a main Route table, which is used for all subnet by default.
When an implicit Router receives the packet, next hop target is determined by specific route priority. Each route in route table can be static, Local and dynamic. Explicitly configured routes are static. Dynamic Route originates through route propagation from a VGW.
Below is list that defines Route Priority.
- Priority 1: Local Route
- Priority 2: Most Specific Route
- Priority 3: Static Routes
- Priority 4: Dynamic Routes (Propagated from AWS Direct Connect)
- Priority 5: Static Routes configured on VGW VPN.
- Priority 6: Dynamic Routes propagated from a VPN.
IP Addressing:
- A set of CIDR block in IPV4 or IPv6 Format.
- IP address are required by each services in AWS VPC, Inorder to communicated to each other.
- In Order to connect your instance to internet, or to enable communication between your instances and other AWS resources that have public end point, assign Public IPV4 address to your Instance.
- Private IP address is assigned by using CIDR Block of your VPC (automatically at launch or dynamically after launch), whereas Public IP address are assigned from pool of routable IPv4 IP address administrated by Amazon.
- At launch, Each EC2 Instance is assigned a primary IP address to its primary Interface and it is retained until it is terminated.
- An EC2 Instance can have multiple Elastic Network Interfaces and can also have multiple secondary IP address.
- Elastic IP address are static public IP address, that you can allocate to your account and then can attach to your Instances. The Elastic IP address comes from pool of Regional IPV4 address that AWS manages.
- EIP in one region cannot be assigned to an instance with in VPC in a different Region.
- There is One to one relationship between private IPv4 IP address and EIP.
- Elastic IP address will keep associated to your AWS account until you explicitly release them.
Security Groups:
- Security group also acts as a Stateful Virtual Firewall, which is used to control inbound and outbound network traffic to different AWS resources and EC2 instance.
- We say that SG is stateful, because for inbound traffic we have to have inbound rule and for response to inbound traffic, we don’t require outbound rule.
- Whenever a EC2 Instance is launched, it has one Security group attached to it while launching. If at the launch, SG is not mentioned, then EC2 will be launched using default SG for VPC.
- Default Security group allow communication between all resources within SG and allow all outbound traffic, whereas all other traffic is implicitly denied.
- In Each VPC, you can create up to 500 SG and can add 50 inbound and 50 outbound rules per SG.
- We can associate up to 5SG per network Interface and can only edit to allow rules but not deny rules.
- By default, no inbound traffic is allowed until you add inbound rules.
- When a new SG is created, by default it has an outbound rule that allow all outbound traffic. This outbound rule can be edited as per requirement.
Network Access Control List (NACL)
- NACL is a stateless firewall, which is used on subnet level, which is looked from lower value to higher value and in between if any matches found, the evolution stops there.
- Each NACL has final deny at last, which cannot be changed.
- In a VPC, once subnet is created, a default NACL get attached to every subnet. Default NACL allow all inbound and outbound traffic for IPv4. As per AWS best practice, every Subnet must be associated to NACL (default NACL or Custom NACL)
Difference between SG and NACL:
Security Group:
- SG Operates at network interface level.
- It Supports allow rule only
- It was as Stateful Firewall
- AWS evaluates all rule to decide whether to allow traffic
Network NACL:
- NACL Operates at subnet level
- It supports both allow and deny rules
- It was as Stateless Firewall, means returning traffic must be allowed in NACL.
- NACL gets evaluated in order one by one.
Internet Gateways
- It is highly available VPC components, which allow your instance to communicate to Internet.
- When your EC2 instance starts sending traffic to internet, Internet gateway translate the private Source IP of your Instance to associated Public IP address. Internet gateways keeps the mapping of instance IPv4 address to Public IP address.
- When an instance receives traffic from internet, internet gateways translates the destination address (Public IPv4 address) to instance Private IPv4 Address.
- EC2 Instance can also get the Public IP address either automatically at launch or dynamically using IPv4 Elastic IP address.
In Order to provide Internet access to your Public Subnet, follow below rules:
- Create an Internet Gateway and attach it to your VPC.
- Create a default Route in your Public Subnet Route table with next hop or target to Internet gateway.
- Configure NACL and Security group to allow internet related traffic (inbound and outbound)
- Assign public IPv4 or Elastic IP address to EC2 Instance.
Let’s Understand the Internet configuration flow with respect to below figure
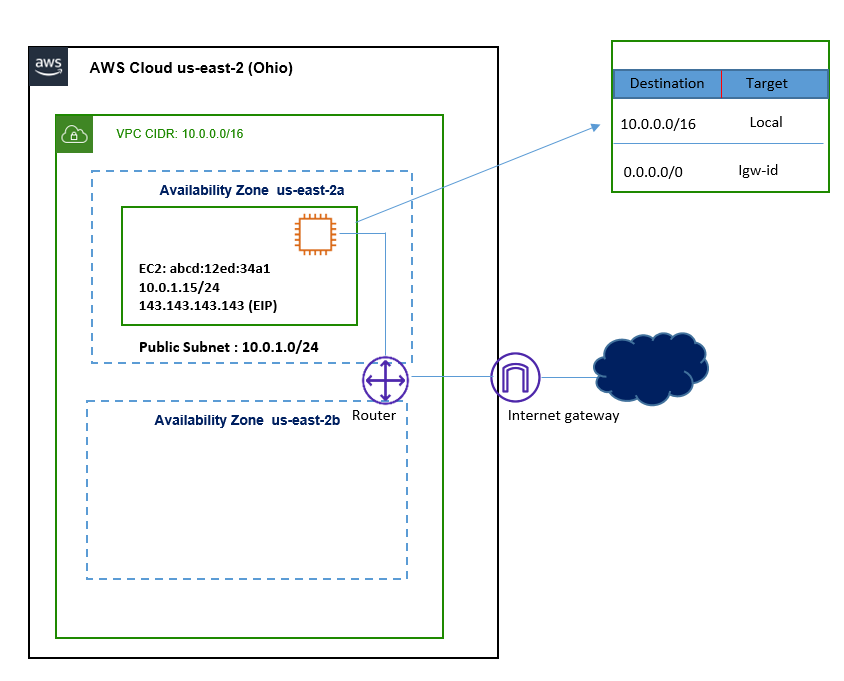
- In Above figure, A VPC is configured with CIDR block of 10.0.0.0/16 and having a public Subnet 10.0.1.0/24.
- As we know that each subnet has Implicit Router, having a Route Table. The VPC has Internet Gateway attached to it.
- A Single EC2 instance is also launched, which is having a private IP address and an Elastic IP address (EIP can also be used to access instance from Internet also)
- Route Table of Public Subnet (10.0.1.0/24) has two routes, 10.0.0.0/16 as local routes, which permits intra-VPC Communication and a default route pointing to internet gateway.





LEAVE A COMMENT
Please login here to comment.