EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USSite-to-Site VPN
This Service is used to connect sites, branches, offices to Datacenter or Cloud Network Securely over an untrusted network like Public Internet. In order to connect these sites to each other over Internet, via VPN connection, a VPN termination endpoint is required at each site. This endpoint will run all the Encryption, Authentication Protocols and does encapsulation and decapsulation of encrypted traffic.
A VPN Connection in VPC to AWS can only be used to access resources inside a VPC and excludes services like Amazon S3, which resides outside to the boundaries of a VPC.
There are two ways to terminate VPN connection inside a VPC:
- Via Virtual Private Gateway
- Via Amazon EC2 Instance
Virtual private Gateway:
It is the managed Gateway Endpoints and is used to terminate VPN connection or AWS Direct Connect Connection.
Once this VGW is created, it can be attached to your VPC, and each VPC can have only One VGW attached at any given point of time.
When we start creating the VGW, we get an option to define ASN for the AWS side of external Border Gateway Protocol (BGP Session). Range for Private ASN is in between 64512-65534. But if we do not choose the ASN of our own, AWS will provide it on behalf of you.
As soon as VGW is created, we can now terminate the VPN connection on it. This VGW only supports IPsec VPN and use ESP mode.
Below figure provides a VPN termination view point.
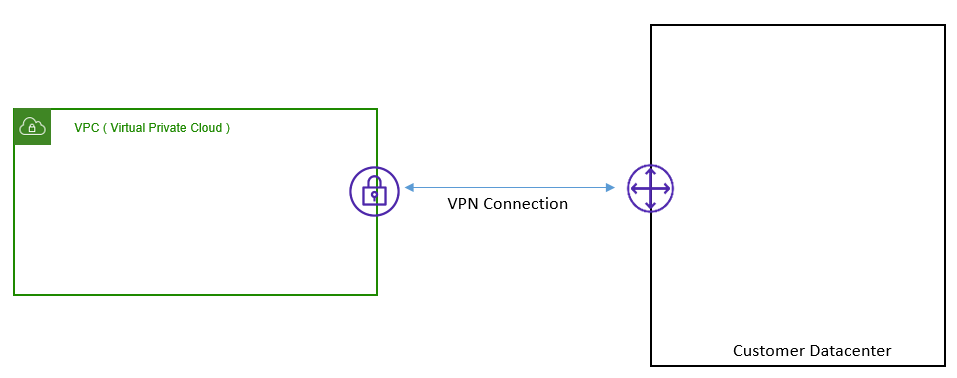
Upon VPN Creation, AWS automatically creates two high available endpoints, each in a different AZ. Each Endpoint has IP address associated with it, which is used to terminate VPN connection on it. These Endpoints are highly available and used to setup VPN tunnel in Active/Active mode. These two tunnels are collectively denoted as a Single VPN Connection.
Below Figure describes, VGW HA Endpoints
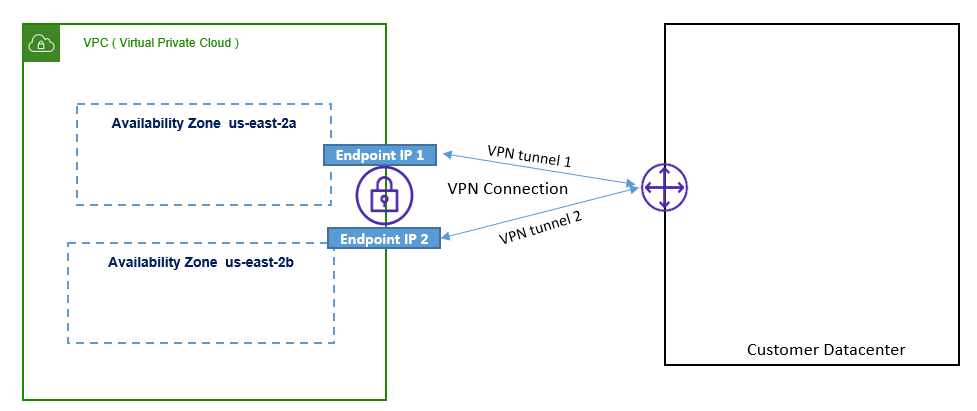
Each tunnel has IKE (Internet Key Exchange) Security Association – names as IPsec SA. Here you can have one unique SA pair per tunnel (One Inbound and One Out bound) so for two tunnel, total 4 SA is required. BGP peering can also be used which is Optional and can be used for Route Based VPN.
VGW VPN features:
Below are some VGW VPN features that are supported in AWS Environment.
Security
Below are some Cryptography protocols supported by VGW in AWS.
- Advance Encryption Standard (AES) 256
- Secure hash Algorithm SHA-2
- Phase 1 Diffie Hellman (DH) Groups: 2,14-18,22,23,24
- Phase 2 DH groups: 1,2,5,14-18,22,23,24
- VGW also has backward compatibility for older Cryptography protocols. These are used in IKE phase 1 and Phase 2 SA Negotiation.
Routing:
VGW supports both Static Routing & Dynamic Routing – BGP.





LEAVE A COMMENT
Please login here to comment.