EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USAccessing Endpoints over AWS Direct Connect
We use Gateway VPC Endpoints and Internet VPC Endpoints to access AWS Cloud Services without using internet or NAT device in your VPC. Customer Hosted Endpoints is used to expose your own service behind NLB as an endpoint to other VPC.
Gateway Endpoints use the AWS Route Table and DNS to route traffic privately to AWS Cloud Services and this gateway Endpoints are not accessible from Out Side AWS like AWS Direct Connect, AWS Managed VPN. How Ever EC2 Proxy Form, we will be able to access the Gateway Endpoints over AWS Direct Connect Private VIF and VPN.
Interface Endpoints and Customer-Hosted Endpoints are powered by AWS private Link and can be accessed over AWS Direct Connect. As soon as Interface Endpoints or Customer Hosted Endpoints are Created, AWS Cloud Service creates a regional and Zonal DNS name that resolves to Local IP address with in your VPC. This IP address will be reachable to AWS Direct Connect Private VIF. How Ever Accessing Interface Endpoints and Customer Hosted End Points via VPN or VPC Peering is not supported.
Encryption on AWS Direct Connect:
If you want to Encrypt all application traffic, you can use TLS at application layer, this approach is more scalable and does not impose any challenges related to High Availability, Throughput and Scalability.
But if your application is not able to encrypt data using TLS, then in that case you can setup Site to Site VPN over AWS Direct Connect.
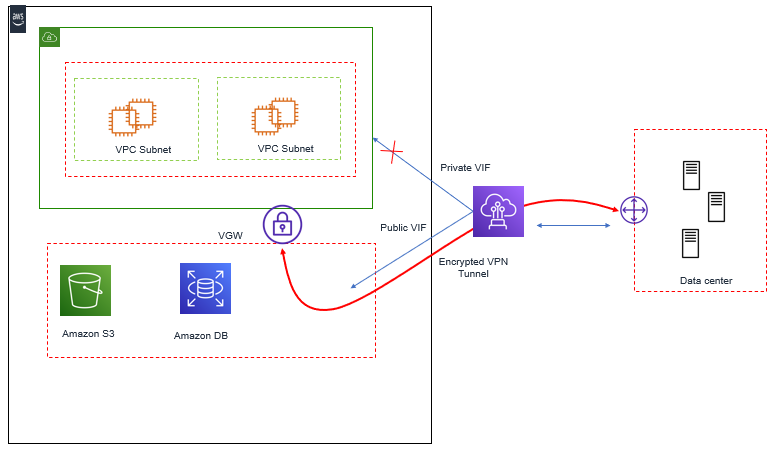
In Order to set up the IPsec VPN over AWS Direct Connect, terminate VPN on the AWS managed VPN Endpoints – VGW. When VPN Connection is created, VGW provides two Public IP Endpoints for VPN Tunnel termination. These Public IP can be accessed over AWS Direct Connect Public VIF.
Below Figure describes VPN to VGW Over AWS Direct Connect Public VIF.
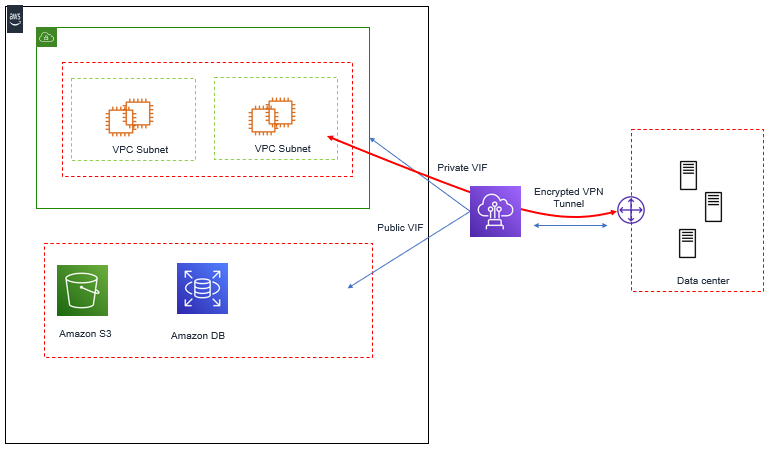
There is another solution available to encrypt traffic over AWS Direct Connect, that is set up Site to Site VPN to an Amazon EC2 Instance inside VPC. Here EC2 Instance Private IP can be used to terminate VPN tunnel over AWS Direct Connect Private VIF. AWS Direct Connect Private VIF is used to access the EC2 Instance Private IP in VPC.
Below figure explains VPN to Amazon EC2 Instance over AWS Direct Connect private VIF.
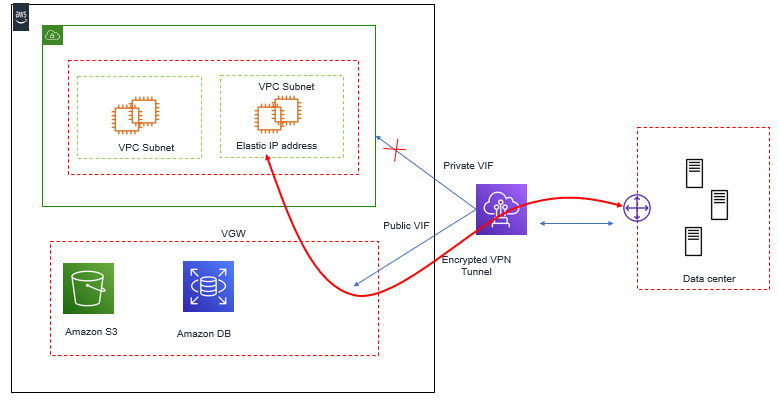
We can also use the Amazon EC2 Instance Elastic IP address via AWS Direct Connect Public VIF to terminate VPN. Here you can configure your On-premises router to filter routes received from AWS Router over AWS direct Connect public VIF and allow only Ec2 Instance Elastic IP address through it. Doing this all other traffic for other AWS Public IP spaces will be blocked.
Below Figure describes VPN to Amazon EC2 Instance Over AWS Direct Connect Public VIF.
In order to achieve High Availability, you should use Amazon Ec2 Instance in different AZ for VPN termination.





LEAVE A COMMENT
Please login here to comment.