EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USAWS Organizations
AWS Provides a structural methodologies including AWS Cloud Adoption Framework (CAF) , to help you for your Cloud Journey.
AWS Organizations is a centralized Management of Multiple AWS Accounts. It has two main features.
Service Control Policy:
It enables designated Master account
- To define the policies that restrict, at account level.
- Services are actions for member-account users, group and role they assume.
Programmable Support:
Creates programmatic account creation. When we use the AWS Organizations to create a new account within an organization, the new account is created with administrative role called OrganizationAccountRole, which user will assume to access new account.
Security for Edge Locations:
AWS provides various services from edge locations across the globe. These AWS Edge Location Infrastructure is also capable of detecting, preventing, and Mitigating the impact of DDOS attack on your environment. These Edge location implements Confidentiality, Integrity and Availability of your network.
All Edge Locations include Built-in Layer -3 and layer-4 network Mitigations. These Infrastructure continuously analyze traffic for anomalies and provides built-in-defense against common DDOS attacks, such as SYN floods, UDP Floods, and reflection attacks. Many services at edge locations have the ability to apply geographic isolation and restriction.
A well-formed UDP or TCP packet are serviced by edge locations. All traffic is scored across a set of dimensions to prioritize the flow of legitimate traffic.
Amazon Route 53 Security
Amazon Route 53 is a highly scalable and Available DNS service offered by AWS. Route 53 uses different mechanism to protect itself from DDoS attack, fault isolation, Performance Scaling or Any-Cast Striping.
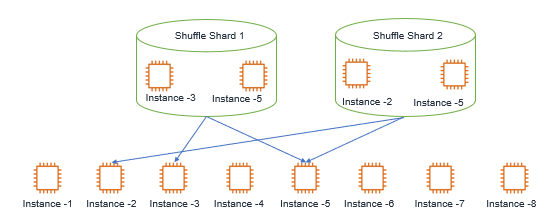
Shuffle Sharding is a technique used by Route 53 to minimize correlated failures such as fault isolation, Performance Scaling and the effects of randomized or shuffled assignment.
Let’s understand as an example that Route 53 uses ten instances to create 5 shards that means each shards has one pair of instance. For internal redundancy. Now let’s suppose if each customer is assigned one particular shards (customer 1 – Shards 1 and Customer -2 shards-2 likewise), and in case if Shards-1 comes under DDoS attack, in that case Customer-1 will face DNS and Operational Issues.
But if we took the 10 instances and randomly assigned customers to a pair of instances, then correlated failures would significantly decrease.
With this method, customer1 Would be on shuffle shard composed on Instance 3 and 5, likewise customer -2 is on shuffle shard composed on instance 2 and 5. These shuffle shards will mitigate the impact of an availability loss to instance 5 as shown in figure.
AWS Certificate Manager
AWS Certificate manager is a certificate Service which is used to create and Manage TLS certificate for your AWS Websites and applications. AWS Certificate Manager is supported on Amazon CloudFront, Elastic load balancing, AWS Elastic Beanstalk, Amazon API gateway.
When AWS certificate manager generates the Certificates, AWS provides you with a domain validated RSA-2048, SHA-256 Certificate, which is valid for 13 Month. Now this service will auto-renew the certificate, typically 30 days before expiration.
The Certificate generated must include one FQDN and you can also add additional name like wildcards names such as *.dclessons.com. The Certificate generated are free and you cannot download the private key. The Private key is encrypted and at rest with the AWS –KMS.
Certificates in AWS certificate manager are regional resources and if we want to use same FQDN in multiple regions, you need to request or import a certificate in each region.
AWS WAF:
AWS WAF is web application firewall that allows us to protect AWS resources from common Web threats.
When we implement AWS WAF service, we implement Web Access Control lists (ACLs), in order to control your HTTP and HTTPs Service.
Web ALCs are composed of rules and rules are composed of conditions.
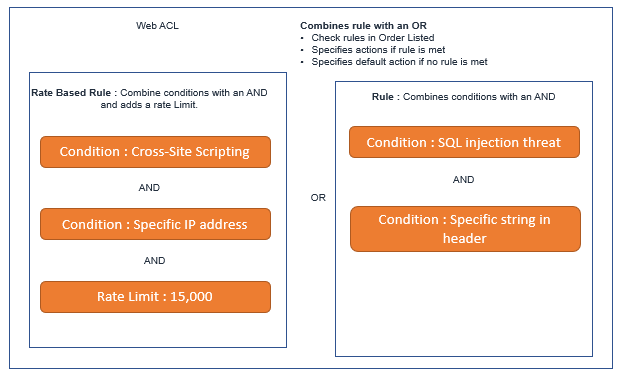
Below are some Six Types of conditions that are commonly supported. Let’s understand the conditions one by one.





LEAVE A COMMENT
Please login here to comment.