EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USTransitive Routing
The customer can define its subnets in the VPC, provide Internet access within it, and grant connectivity for the resources from VPC to on premise data centres or to other locations (may that be another AWS VPC or another cloud provider).
Until recently, AWS did not allow to connect a VPC from one region to a VPC from another using the VPC Peering feature. VPC Peering is a network connection between two VPCs that allows to route IPv4 and IPv6 traffic between them. Means Transitive Routing is not supported in AWS.
AWS has some unsupported VPC Peering configurations and one among them is Transitive Peering. Let’s suppose that you have VPC-A connected to VPC-B using a peering connection, and you have another peering connection between VPC-A and VPC-C.
There is no direct peering connection between VPC-B and VPC-C. Although both are connected to VPC-A, they cannot use VPC-A to communicate with each other.
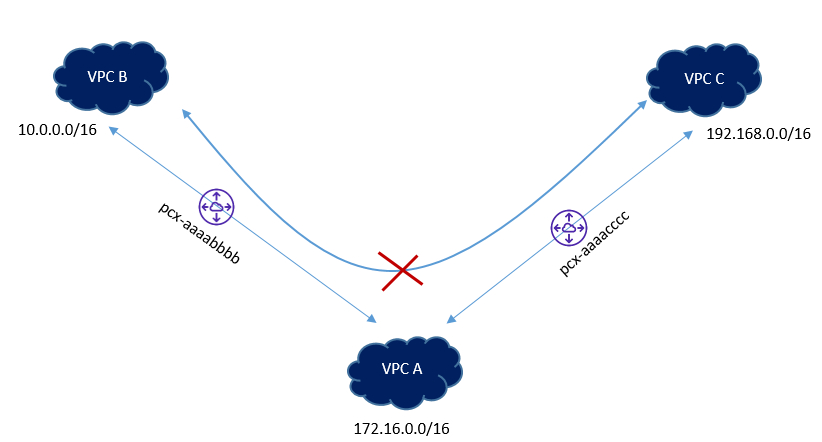
A transit VPC simplifies network management and minimizes the number of connections between VPCs. A full-mesh peering between four VPCs will require N*(N-1)/2 links (where N is the number of the VPCs), which in this case is six, in order to communicate to each other.
Imagine what this would mean if there are 100 VPCs. Not to mention the time and costs involved to deploy such a solution.
In the case of Traffic passing between VPC peers, there is always Source/Destination check, means If the Source Packet is not an interface in your Local VPC, the destination of the connection must be a network interface IP address, local to the VPC. Either the destination or source of the packet must be an interface local to VPC.
Even though, for any external connectivity to VPC and from that VPC to another VPC, this rules prevails, in order to overcome this issue, we can better use the Proxies routers, EC2 VPN, NAT instances, and when these devices receive packets and forwards it to next hop, it will change the source Address of the packet and this behavior requires disabling the Source/Destination check.
This Source/ Destination check will not allow an instance to receive a packet if destination does not match one of the assigned IP address. Also it will not allow an instance to send a packet with the source IP address that it has not been assigned.
Below are some transitive Routing Examples:
Example 1: Let’s suppose, you are trying to access the S3 Endpoint, over AWS VPN, the source Packet will come from outside VPC, and the destination will be Amazon S3 Address. Here the packet will be dropped as per VPC Rule check. Now if we are using the destination as Proxy instated, the destination will be local to network interface.
Example 2: Let’s suppose there are two VPC peered with each other, and an internet gateway is attached to one of the VPC. The VPC without internet gateway has a default route pointing to peering connection. Now the Peered gateway will not be able to access the internet via peering connection.





LEAVE A COMMENT
Please login here to comment.