EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USAzure WAF on Azure Front Door
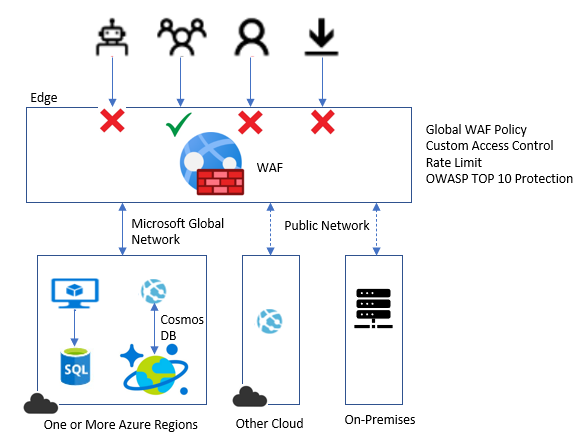
Azure WAF on Azure Front door provides centralized protection for your web applications. WAF defends your Web services against common exploits and Vulnerabilities.
This Solution is deployed on all edge locations around the globe, which enables web application inspection to every incoming request delivered by Front Door at the network edge.
WAF prevents malicious attacks close to attack source before they enter to your network. A WAF policy can be easily linked to any Front Door profile in your subscription, and new rules can be deployed in minutes, to quickly respond to changing threat pattern.
Azure Front door has two tiers: Front Door standard and Front Door Premium. WAF is natively integrated with Front Door Premium with full capabilities.
WAF Rules:
A WAF Policy consist of two type of security rules:
- Custom Rule: That is created by admin or yourself.
- Managed Rule set: Azure Preconfigured rule sets.
Custom Rule set: below are some custom rule sets that can be configured.
- IP Allow list and blocklist: Source IP can be allowed or blocked to your web applications based on list of clients Ip address or their ranges.
- Geographic based access control: Control access to your web applications based on the country code that associated with client IP address.
- HTTP parameter-based access control: You can create rules on string matches in HTTP/HTTPS request parameter. Example: Query, Strings, POST args, Request URI, Request Header, and Request Body.
- Request method-based access control: You can create rule based on HTTP request method of the request like GET, PUT or HEAD.
- Size Constraint: You can create rule based on lengths of specific parts of the request such as query string, URI, or Request Body.
Azure Managed Rule set: These Rules provide easy way to deploy protection against a common set of Security threats. These rules are managed by Azure and are updated as needed to protect against new attacks signatures. These Azure managed default rule set includes rules against following threat categories:
- Cross-Site Scripting
- Java Attacks
- Local File inclusion
- PHP injection attacks
- Remote command execution
- Remote File inclusion
- Session fixation
- SQL injection protection
- Protocol attackers.
As soon as new attacks signature are added to rule set , default rule set version number increases. Default rule set is enabled by default in Detection mode in WAF policies. You can also enable or disable individual rule with in Default rule set , in order to meet your application requirement.





LEAVE A COMMENT
Please login here to comment.