EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USNetwork Security Groups
Azure NSG is used to filter Network traffic to and from Azure resources in an Azure Virtual Network. NSG contains the security rules that is used to allow or deny any traffic from different Azure Resources.
A NSG contains Zero or as many as rules as we need within Azure Subscription limit.
Below are some fields that are used to create Rules:
- Name: A Unique name with in NSG.
- Priority: Priority defines order in which rules are processed. It is number between 100 and 4096. Lower number have high priority and are processed first. Once rule matches, Processing stops.
- Source or Destination: Any or individual IP address, CIDR block, Service tag, or Application Security group.
- Protocol: TCP, UDP, ICMP, ESP, AH or Any.
- Direction: Inbound or Outbound.
- Port-Range: Can specify Specific Port or range of Port. (Eg: 80, or 100-2345)
- Action: Allow or Deny
Security rules are evaluated and applied based on five-tuple (Source, Destination , Source Port , Destination , Destination port , Protocol ).
A Flow record is created for existing connections and communication is allowed or denied based on connection state of the flow record. Flow records are stateful in Nature.
If Inbound port is allowed over a port, it is not necessary to specify an outbound security rule to respond to traffic over the port.
Default Security Rules
Azure has following default rules in each network security group you create. Below are default security rules:
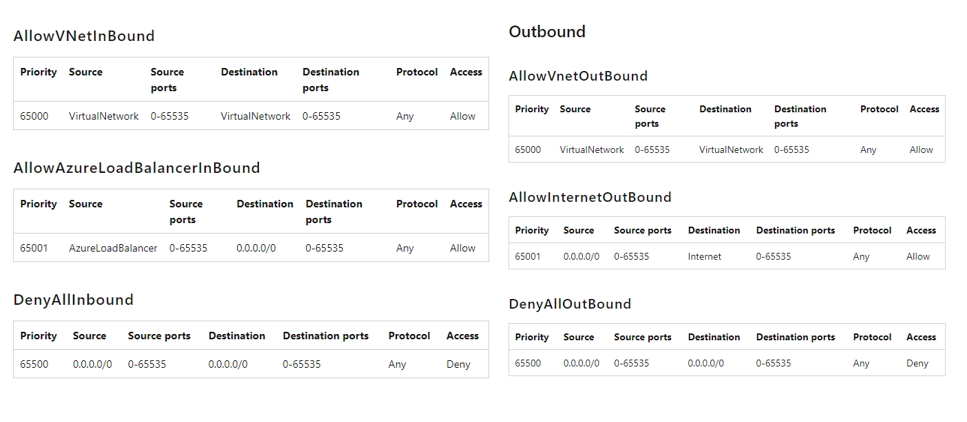
You cannot remove default rules, but you can override them by creating rules with higher Priorities.
Augmented Security Rules
Augmented Security Rules are security definition for Virtual networks, allowing you to define larger and complex network security policies with fewer rules. In this you can combine multiple ports and multiple explicit IP address and ranges in to a single, easy understood rule.
Service Tags
It represents a group of IP address prefixes from a given Azure Service. It helps to Minimize the complexity of frequent updates on Network Security rules.





LEAVE A COMMENT
Please login here to comment.