EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USCross-Premises Azure Virtual Network
A Cross-Premises Azure Virtual Network is connected to your On-Premises Network, extending your network to include subnets and virtual machine hosted in Azure.
In Order to connect your On-Premises network to Azure Virtual Machine, you should configure a cross-Premises Azure Virtual Network.
Below diagram shows the components required to deploy the Cross-Premises Azure Virtual Network with a Virtual machine in Azure.
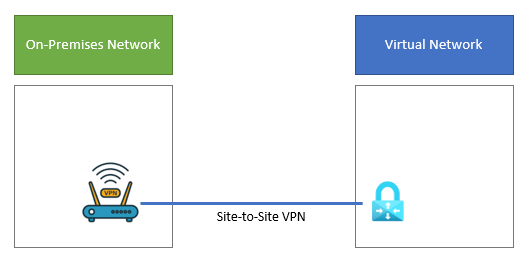
In above figure, Two networks are connected via Site-to-Site VPN Connection over Public Internet. VPN is terminated on VPN Device on On-Premises Network and Azure VPN gateway on Azure Virtual Network.
In Order to set up the VPN Connection between your Azure Virtual network and On-premises network, you must follow the following steps:
- On-Premises: Define and Create an On-Premises Network route for subnets of the Azure Virtual network that points to your On-Premises VPN Device.
- Microsoft-Azure: Create an Azure Virtual Network with a Site-to-Site VPN Connection.
- On-Premises: Configure your On-Premises Hardware or Software VPN device to terminate the VPN Connection, which uses Internet Protocol Security (IPsec).
Once Site-to-Site VPN is established, you can add Azure Virtual machine to subnets of the Virtual network.
How to Plan your Azure Virtual network
Prerequisites:
- You must have an Azure Subscription.
- An Available IPV4 address Space (Subnets) for Azure VNet.
- An Available VPN device in your On-Premises network to terminate the Site-to-Site VPN Connection that supports requirements of IPsec.
- Change your Routing Infrastructure so that traffic routed to the address space of Azure Virtual network gets forwarded to VPN device that hosts the Site-To-Site VPN Connection.
- A Web-Proxy that routes On-Premises Computers and Azure VNet access to Internet.
Solution Architecture Design Assumption
This Solution uses Single Azure VNet with Site-to-Site VPN Connection. Single VNet uses a single subnet that host multiple Virtual Machine.
You should use Routing and remote Access Service (RRAS) in Windows Server 2016 or Windows Server 2012 to establish an IPsec site-to-site VPN connection between On-Premises network and the Azure Virtual network. You can use other option like Cisco, Juniper VPN device.
On-Premises Network might have services like Active Directory domain service , Domain Name System, Proxy Servers. Based on your requirement , it can be useful to place some of the these service in Azure VNet.
Plan Routing for Azure VNet
On-Premises Network must be configured to route traffic destined for Azure Vnet Subnets towards VPN device hosted on On-Premises Network.





LEAVE A COMMENT
Please login here to comment.