EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USAzure VPN Gateway
VPN gateway is used to provides secure connectivity between Vnet or between Vnet to On-Premises and send the encrypted traffic between them. It uses the Public Internet for sending traffic between Vnet and On-Premises network and uses Microsoft network for sending traffic between Vnet in Azure if connectivity between Vnet is done via VPN gateway.
Each Virtual network can have only one VPN gateway, and with same VPN Gateway, multiple connection can be done, in which all VPN tunnels will share the same available gateway bandwidth.
In Order to configure VPN gateway, you need to configure Virtual Network Gateway and select the gateway type as ‘vpn’. The gateway type ‘vpn’ will specifies that the type of virtual network gateway created is a ‘VPN Gateway’.
A Virtual network can have two type of Virtual Network gateway: One VPN gateway and one ExpressRoute Gateway.
When we create a VPN gateway, Gateway VMs are installed to the gateway subnet and configured with setting that you specified. Once Gateway has been created, you can create an Ipsec/IKE tunnel connection between VPN Gateway and another VPN gateway (Vnet to Vnet ) or create a cross-premises Ipsec/IKE VPN tunnel connection between VPN gateway and on-premises VPN device (Site to Site ).
Deploying VPN gateways in Azure Availability Zones , provides resiliency , Scalability , and higher Availability to virtual network gateways. It also protect your on-premises network connectivity to Azure from Zone level failures.
Options to provide VPN connectivity
Below are three options that Azure provides for Connectivity.
- Site to Site VPN connection
- Point to Site VPN connection
- Vnet to Vnet Connection.
VPN Connection planning
In order provide the Connectivity type as discussed above, below table will help you to choose or decide best connectivity option for your Solutions.
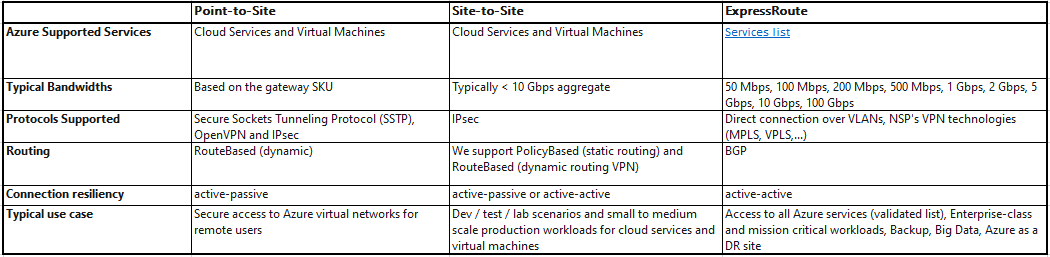
Gateway SKU
When we create a Virtual network Gateway, we must specify the gateway SKU that we want to use. A proper SKU must be selected that satisfy our requirement based on types of workloads, throughputs, feature, and SLA.
Below table explains the Gateway SKU by tunnel, Connection and Throughput.
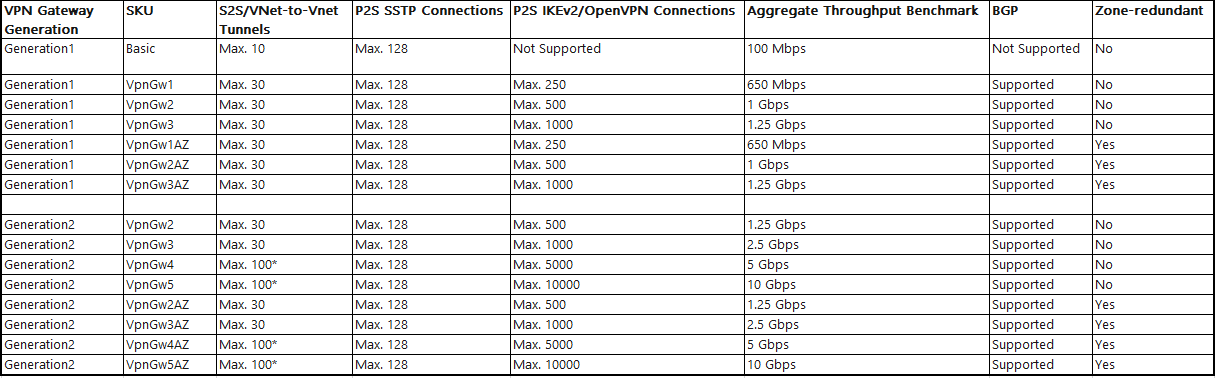
(*) Use Virtual WAN if you need more than 100 S2S tunnels.
The Resizing of VpnGw is allowed within same Generation, except resizing of the basic SKU. The Basic SKU is the legacy SKU that has limited features. When we want to move from basic KSU to another SKU , we must delete the basic SKU VPN gateway and create a new gateway with desired Generation and SKU Size Combination.
The Connection Limits are separate, example you can have 128 SSTP connection and 250 IKEv2 connection on a VpnGw1 SKU.
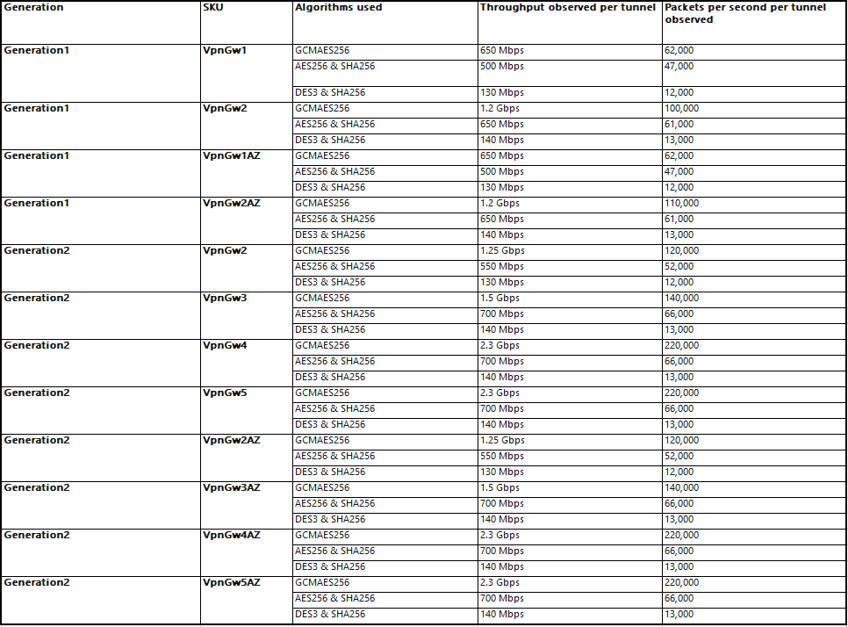
In order to understand the performance of different SKUs using different Algorithms, you should use publicly available tool like iPerf and CTSTraffic, in order to measure performance for Site to Site VPN connections.
Below table shows observed bandwidth and packets per second throughput per tunnel for different Gateway SKU. All testing was performed between gateways (endpoints) within Azure across different regions with 100 connections and under Standard Load conditions.
Site to Site VPN
A Site-to-Site VPN gateway provides Ipsec/IKE (IKEv1) VPN tunnel connection between Vnet to Vnet or between Vnet to On-premises. A S2S connection requires a VPN device located on-premises that has public IP address assigned to it.
Below figure describes the S2S VPN Connection between On-Premises and Vnet.
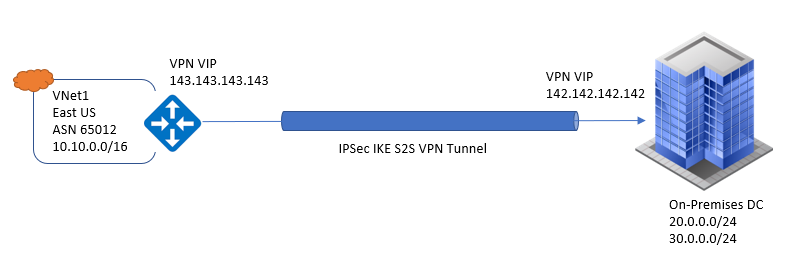
VPN gateway can be configured in active-standby mode using One public IP or in Active-active mode using two public IPs. Active-Active VPMN tunnel is recommended option, with data flowing through both tunnel at same time and provides higher throughput to customers.





LEAVE A COMMENT
Please login here to comment.