EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USConfiguring ISE for Onboarding
Here we will see all list of configuration that is essential to learn Configuring BYOD in ISE.
Configure Native Supplicant Profile
NSP defines the network setting for endpoints that will go through onboarding. Native Supplicant profile defines the following:
- One or more wireless SSIDs
- EAP type to use (PEAP or EAP-TLS)
- Key size for certificates
- Level of wireless security
- If it applies to wired, wireless, or both
- Proxy configuration, if any
- Whether or not to connect to the SSID if not broadcasting
Beginning with ISE 2.0, NSP is preinstalled, below path will let you go to see the latest Client Provisioning resources from cisco site and you can then edit them to prebuilt native supplicant profile.
Work Centers | BYOD | Client Provisioning | Resources
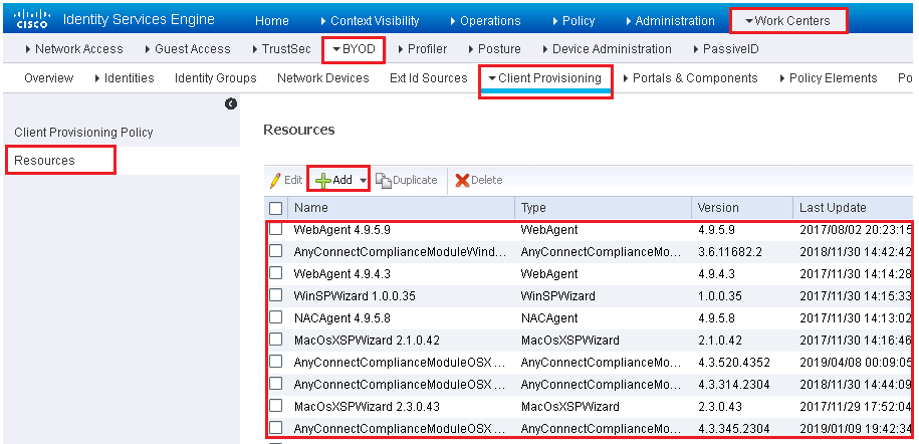
If you want to download newer choose Add | Agent Resources from Cisco Site
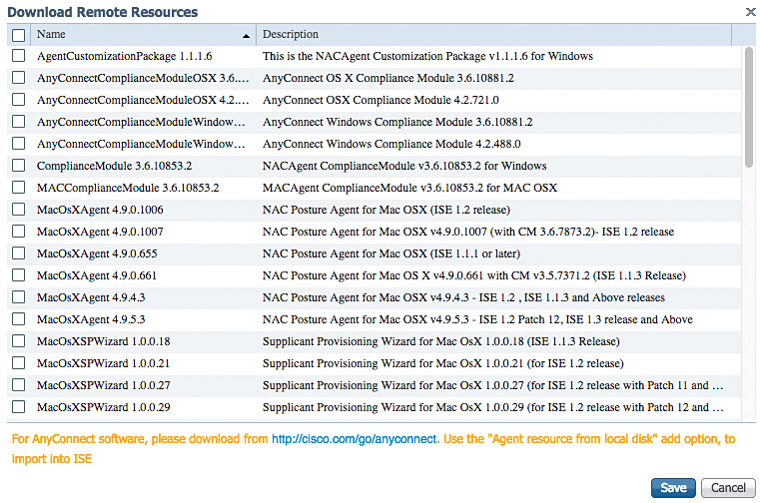
Make sure to enable Proxy setting in ISE. Below is the list of all version of Clients, select any one of them to download and save.
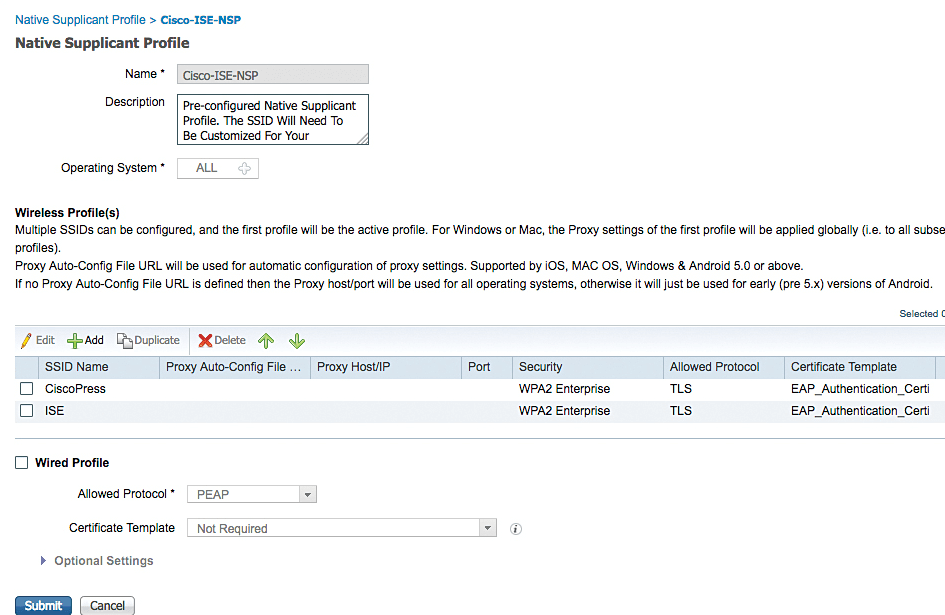
On the resource screen, Select the Pre-Configured NSP Cisco-ISE-NSP | Edit.
It should have pre-configured wireless network SSID of ISE, below figure shows content of Cisco-ISE-NSP.
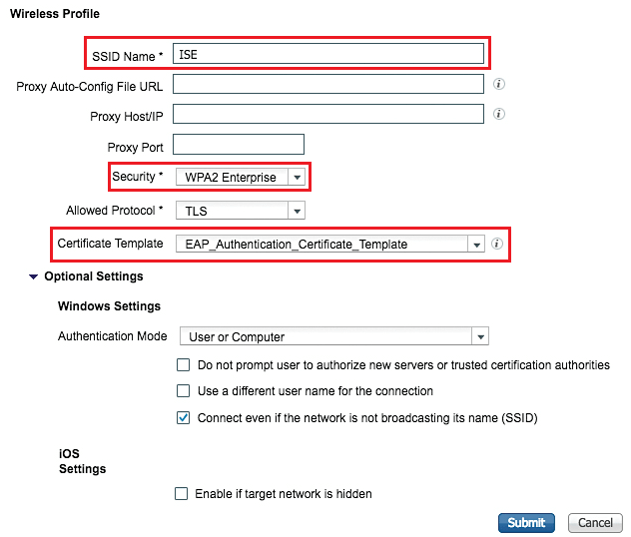
Select ISE and Edit, it will show you pre-configured wireless profile with SSID named ISE with WPA2 and TLS that leverages the EAP_Authentication_Certificate_Template and will connect even if the network is not broadcasting.
Verify Certificate Template
ESP-TLS is very common and when TLS is used, a certificate must be issued to endpoints. Certificate template provides information about certificate content, its strength, and CA information that has issued this certificate.
Verify default EAP_Authentication_Certificate_Template that is used in the default Cisco-ISE-NSP native supplicant profile.
Work Centers > BYOD > Portals & Components > Certificates > Certificate Templates | select EAP_Authentication_Certificate_Template | Edit
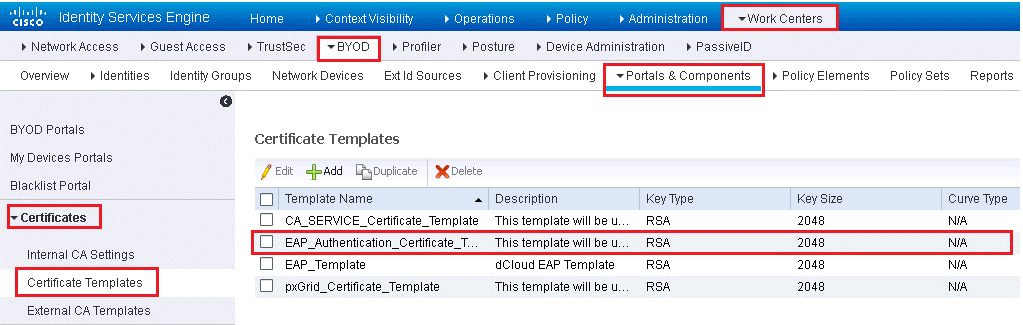
Here you will see, Certificate template is configured with following fields:
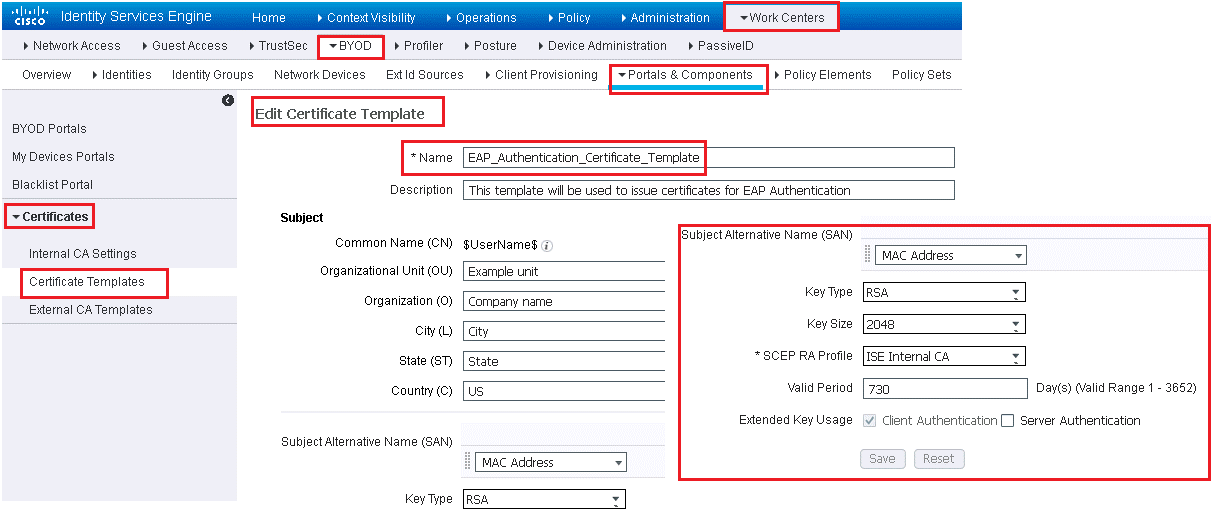
- Common name (CN) set to the $UserName$ variable. This is automatically substituted with the username of the employee performing the onboarding. organization (O) and organizational unit (OU)
- Subject Alternative Name (SAN) field. The drop-down box has only one choice, which is MAC Address; because this cannot be changed or removed
- Default template is configured to use RSA as the key type with default RSA key size is 2048, but that size can be changed to 1024 or 4096.
- SCEP RA Profile to configure which CA should be used to sign the certificates. The default configuration is to use the internal CA; if an external CA is configured in ISE, it will also be in the drop-down list
- Valid Period setting determines how long the certificate is “warranted” by the CA
- The default setting for Extended Key Usage (EKU) of an endpoint certificate is Client Authentication only
Verify Client Provisioning Policy
You need client Provisioning policy (CPP) in order to send NSP to clients. CPP instruct, which software and profile needs to be downloaded and installed based on OS of endpoints.
There is one CPP per OS using the preinstalled native supplicant wizards, native supplicant profiles, and certificate templates. To examine these preconfigured policies, navigate to Work Centers | BYOD | Client Provisioning
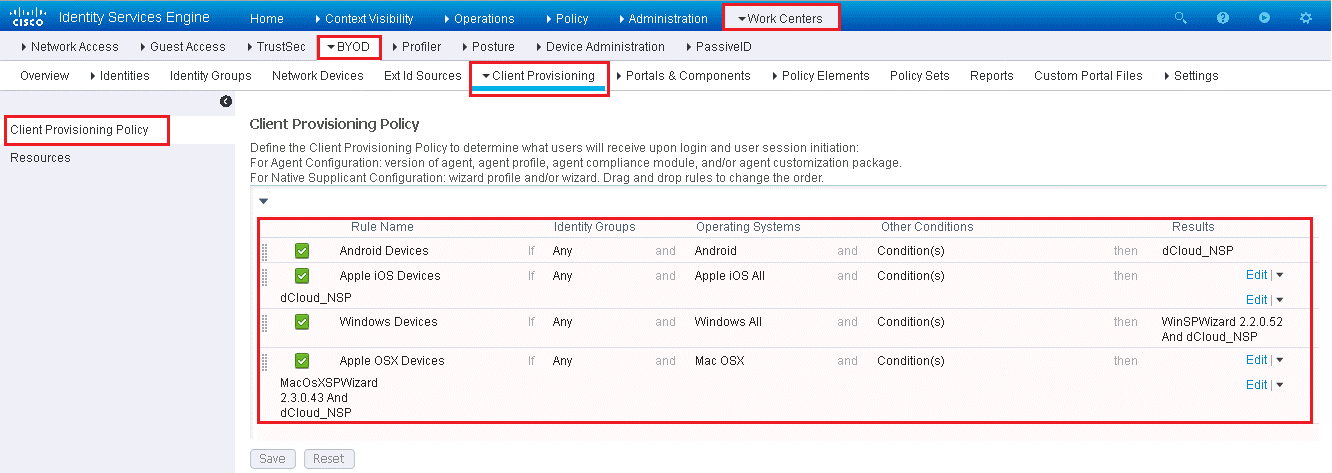
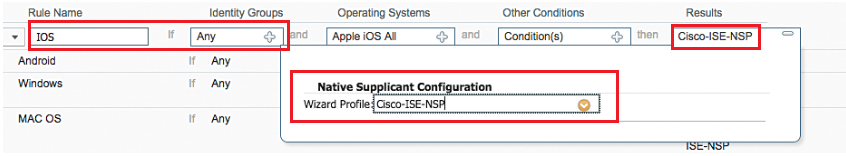
As an example, see how to very CPP for Apple iOS and then you can by your own verify CPP for Android.
- On rule name IOS , Click Edit at right end of the row
- Note , this rule can apply to specific user or endpoint identity groups, Specific OS and other conditions are configured in CPP
- Click on + on result column, here you will see Cisco-ISE-NSP profile is selected , due to which ISE BYOD portal uses the OTA provisioning process that is native to Apple iOS.
BYOD and WebAuth Portals
These portals represents client, when they login via Single SSID or Dual SSID. For Single SSID, BYOD portal is used, and for Dual SSID, WebAuth Portal is used.





LEAVE A COMMENT
Please login here to comment.