EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USGoals of Authorization Policies
The Goal of Authorization policies to allow users or devices after authentication: What they are authorized to do. In this they examine the condition and send the authorization result to Network Access Device (NAD).
These Authorization result may be standard RADIUS Access-Accept or Access-Reject message. It also includes advance item like VLAN Assignment, dACLs, SGT, URL redirection and a lot more.
Basic Authorization policy rule are as follows:
IF Condition THEN Assign these Permission
These policies are evaluated from top to bottom and whenever first match is found, next evaluation is stopped. ISE already have some predefined policy like: Smart Objects, Blacklist device policy (named as Wireless Blacklist Default), Cisco IP Phones policy, Non Cisco IP Phones. There are also some predefined rules that are disabled but can be used on BYOD and Guest Access.
Here we will see an example, about Cisco IP phones and wireless List Default, to see how authorization policy works in detail.
Cisco IP Phone Authorization Policy
In order to configure, use below path:
Work Centers | Network Access | Policy Sets | Default.
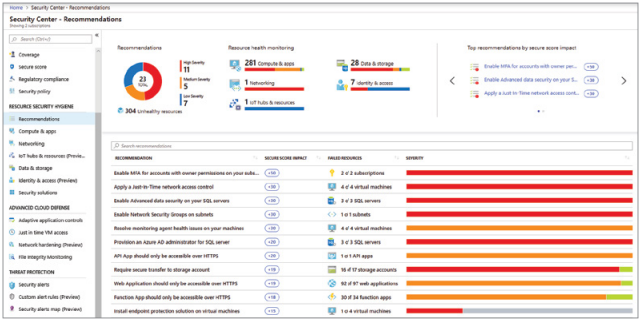
Click on Edit and provide rule name Profiled Cisco IP Phones. Select the Cisco IP Phones in Identity Group details. As this rule is prebuilt, says that permit any device that is profiled as Cisco IP phones, send an Access-Accept and attribute-Value-Pair that will permit the Phone in to Voice VLAN.
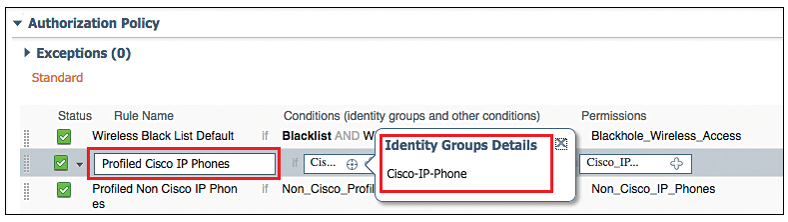
Now let’s verify the permission (Condition) that is sent. Go to Work Centers | Network Access | Policy Elements | Results | Authorization Profiles.
This Authorization Profile, is set of authorization result that is sent together. Below figure shows default authorization profile.
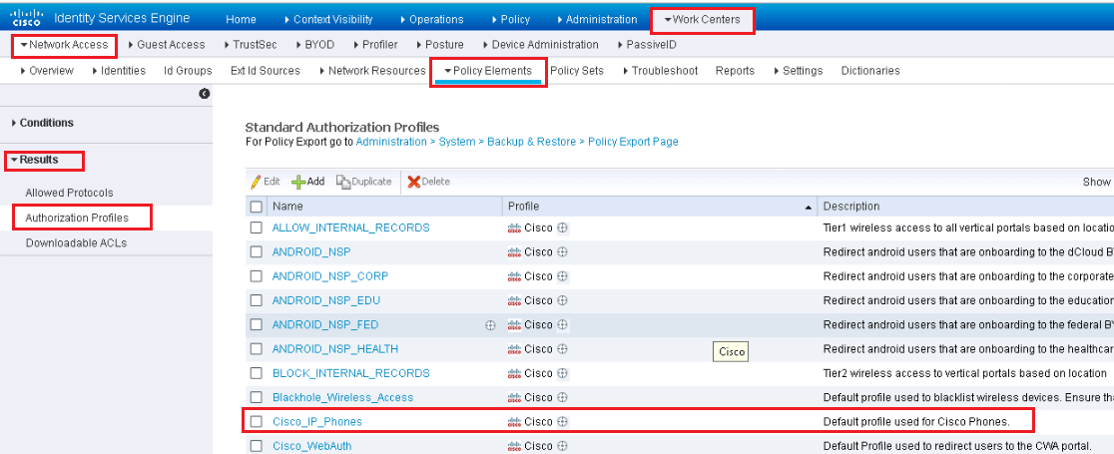
Click on Cisco_IP_Phones Authorization Profile and in Attributes details section, you will see raw RADIUS result is sent.
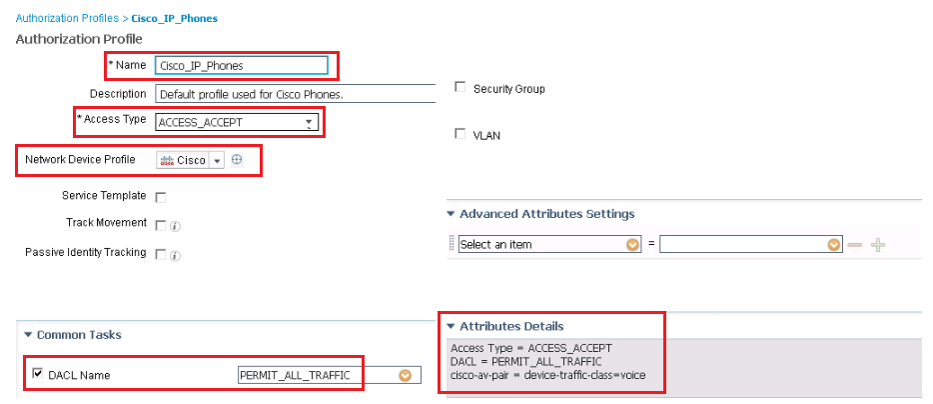
In the above figure, in DACL task list, you have to select the dACL that is created and stored in ISE. Voice Domain Permission is required, for switch to allow IP phones in to Voice VLAN and will actually translates the cisco-av pair = device-traffic-class = voice.
In Attributes Details section, shows the Raw RADIUS result, that will be sent to NAD.
Wireless Black List Default Authorization Rule
In order to see and verify this policy go to Work Centers | Network Access | Policy Sets | Default.
Select the Rule Wireless Black List Default and Edit. Here Identity group is selected as Blacklist and next field populated with pre-built condition, which specify wireless connection. The Purpose of this rule is to prevent devices that has been marked list or stolen.
To verify the authorization condition, go to Work Centers | Network Access | Policy Elements | Conditions | Authorization Compound Conditions
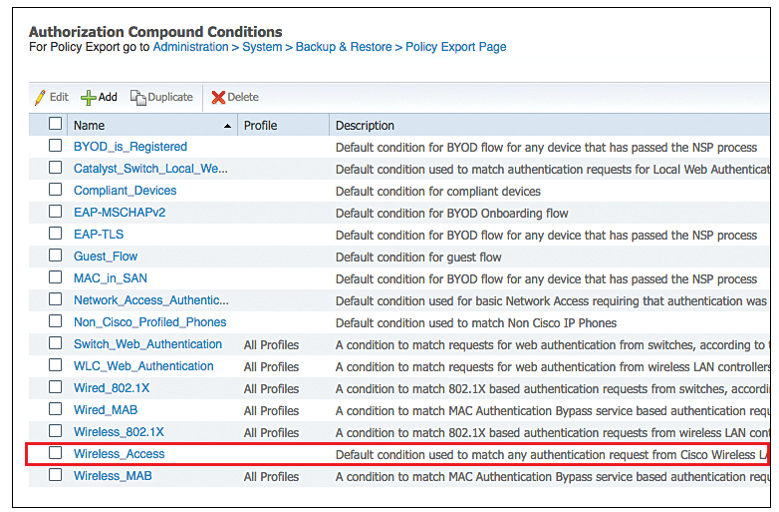
Above figure shows all default compound conditions.
Now click on Wireless Access, where it shows that this compound conditions reference to RADIUS attribute of NAS-port-Type = Wireless-IEEE-802.11.
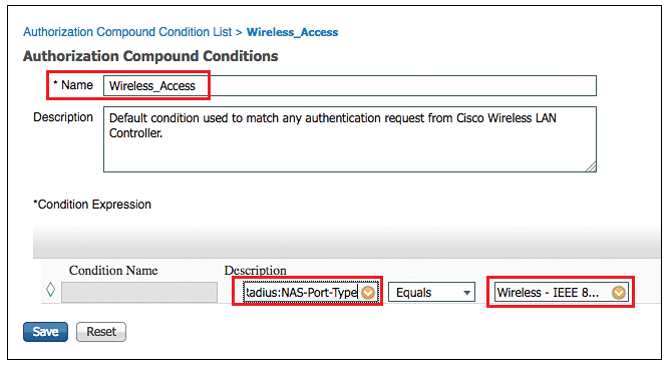
Now examine the authorization result that will be sent for this authorization rule.
Work Centers | Network Access | Policy Elements | Results | Authorization Profiles.
Select Blackhole_Wireless_Access.
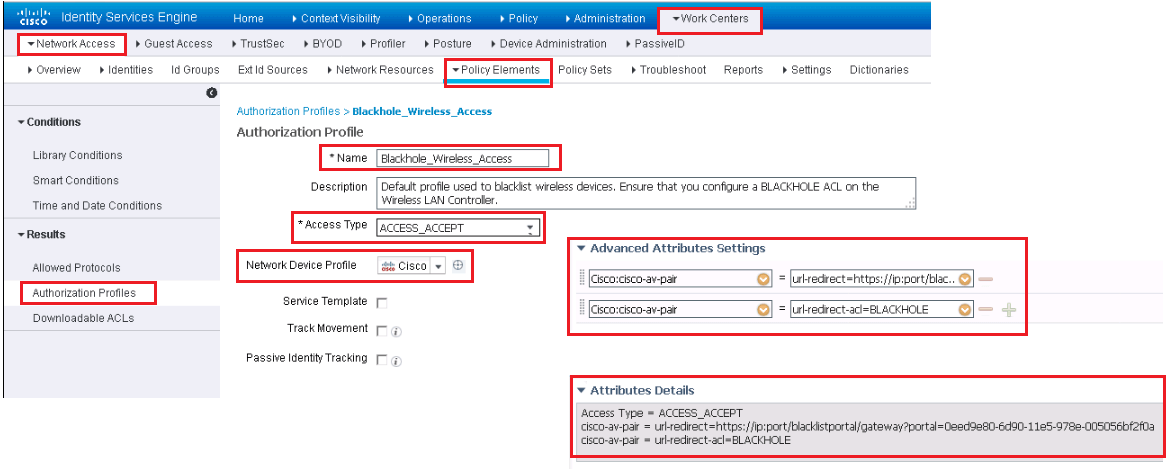
Here it shows in advance attribute setting, it sends the URL redirect and URL-Redirect-ACL result to WLC along with Access-Accept. Due to this result, it allows device on to the network, but forces all traffic to redirect to a webpage describing that device is blacklisted.
Employee & Corporate Machine Full Access-Rule
The objective of this rule is to assign full access permission to an employee who has login from valid corporate asset.
Go to Work Centers | Network Access | Policy Sets | Default
In the Authorization Policy section, create a new rule named Dclessons-Employee above rule name Basic_Authenticated_Access. This Basic_Authenticated_Access rule enables the default behavior of ISE that once any successful authentication happens, access to network is provided.
- In Condition Section, Click on + sign to create new Condition.
- Select Network Access | EapChainingResult equals User and Machine Both Succeeded.
- Click on cog icon on right and choose Add Attribute/Value
- Select AD1 | External Groups Equals “Employees”
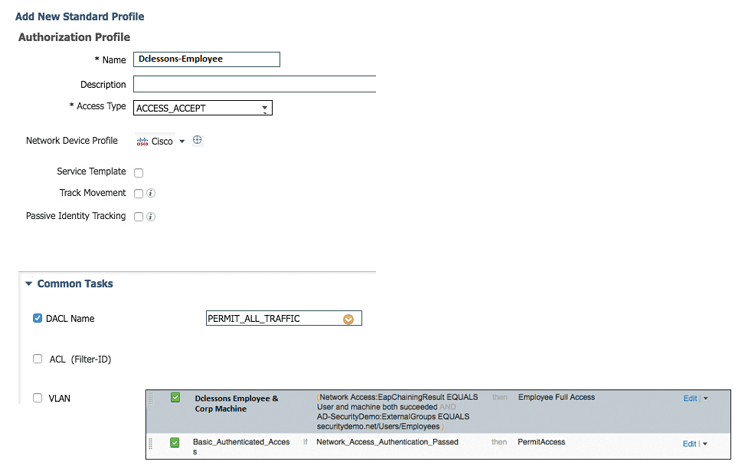
- For the AuthZ Profiles, click the + sign and select Add New Standard Profile, which is found at upper-right corner.
- Provide name Dclessons-Employee and in Access Type, choose ACCESS_ACCEPT.
- In DACL field, select PERMIT_ALL_TRAFFIC
Below figure shows Dclessons-Employee Full access Profile.
Now Click on SAVE | Done | Save to finally completing Authorization policy.
Authorization Rule to Provide Internet Access to Mobile Device
In this rule, we will allow internet access to Mobile device only. To start with create the DACL that will be applied to Switch and then create the authorization result and then authorization Policy needs to be created along with its defined rule.
Go to Work Centers | Network Access | Policy Elements | Results | Downloadable ACLs. | Click ADD | Name ACL Internet Only
In DACL content pane, add the ACL that permits traffic that needs internet access and denies traffic for corporate network
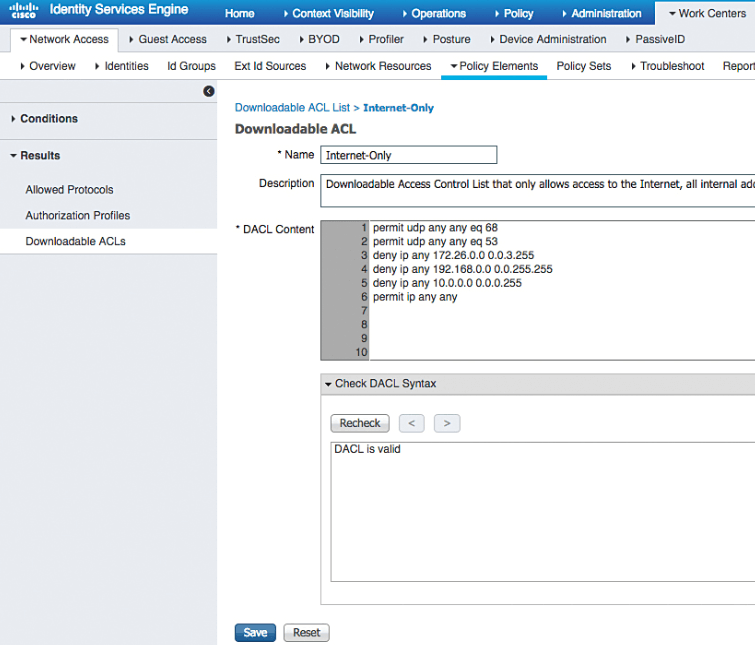
Click Submit.
Now once DACL is created, the another step is to create Authorization Profile.
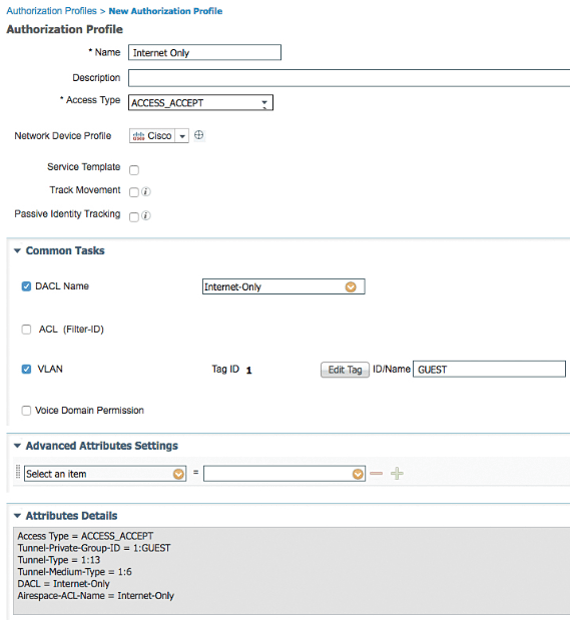
Now Go to Work Centers > Network Access > Policy Elements > Results > Authorization Profiles | Click ADD | name the authorization profile Internet Only.
In Access Type, select ACCESS _ACCEPT and check DACL Name: Internet Only
Provide the VLAN ID and name used for traffic, Select Airspace ACL Name and fill in the name of the ACL on the controller that provides Internet-only access.
Click Submit
The above configuration is shown in below figure.
Here we will use the pre-defined logical profile, for all mobile device, this profile can be viewed by following path.
Work Centers | Profiler | Profiling Policies | Logical Profiles.
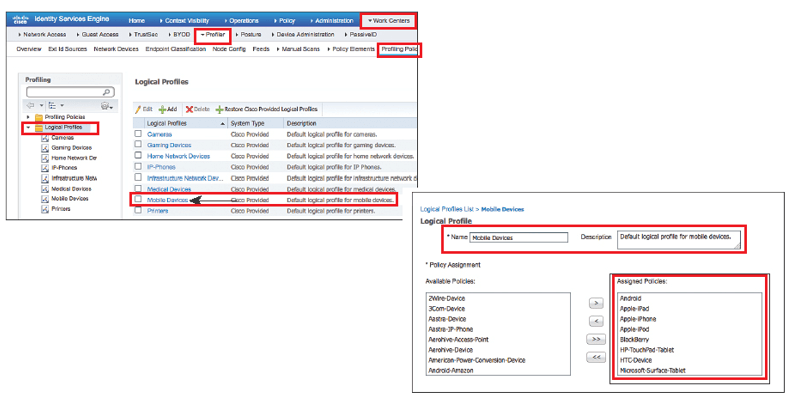
Now click on Mobile Device profile and here you will see this profile is grouping various mobile types like Apple-iPad, Android, Samsung-Phone, and others.
Now we will come to our original Authorization Policy, and will create the authorization rule.
Work Centers | Network Access | Policy Sets | Default
Choose Equals | Select Mobile Devices| Click the cog icon on the right side and choose Add Attribute/Value
Select AD-Security Demo |External Groups Equals “Employees”| in AuthZ Profiles, click the + sign. | Choose Standard | Internet Only| Click Done | Save.
With this we have now completed the Authorization policy which provides Internet access to Mobile Users.
Authorization Rule to Provide Employee Limited Access Rule
Here, we will be configuring the authorization policy that provides limited access to employee who are authenticating from any other device.
We will first create the DACL.
Work Centers > Network Access > Policy Elements > Results > Downloadable ACLs.
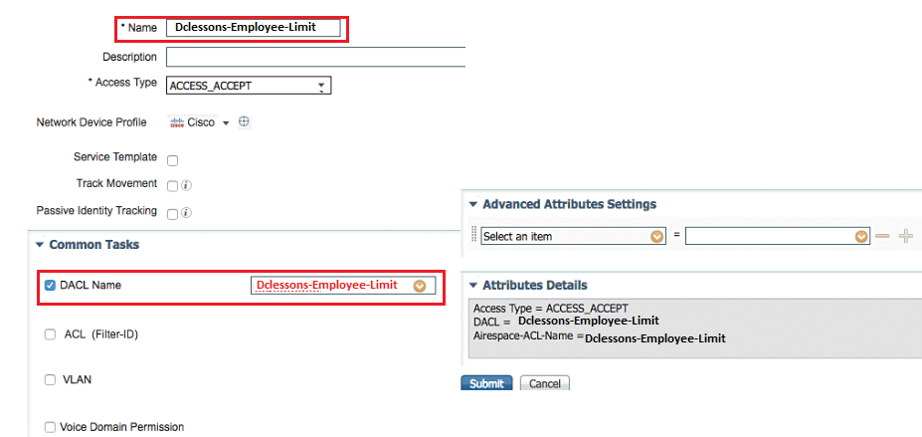
Click Add.| Name the ACL Dclessons-Employee-Limit.
In DACL pane, provide ACL that permits required traffic and denies traffic destinated to corporate network. | Click Submit.
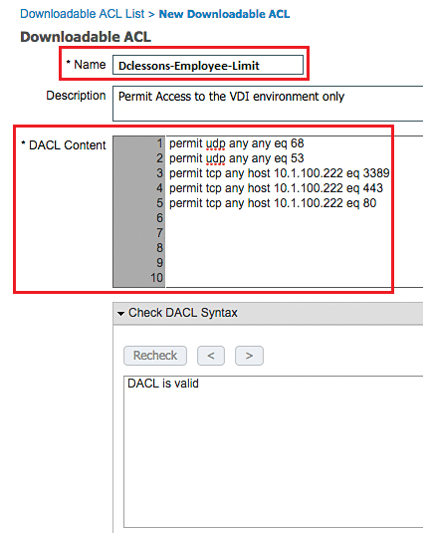
Now build the authorization policy, to permit network access and apply DACL.
Work Centers | Network Access | Policy Elements | Results | Authorization Profiles | Click Add.
Name the authorization profile Dclessons-Employee Limit.
In Access Type |choose ACCESS_ACCEPT | In DACL Field Name choose Dclessons-Employee-Limit | Do not assign a different VLAN for this authorization.
Select Airespace-ACL-Name and fill in the name of the ACL on the controller that provides Internet-only access | Click Submit.
Now create the Authorization rule and assign it to Authorization Profile.
Work Centers > Network Access > Policy Sets > Default. In the Authorization Policy section, insert a new rule above the Basic_Authenticated_Access rule.
Name the Rule DCLESSONS-VDI_Only | Click the + | Select AD-Security Demo > External Groups Equals “Employees”
For the AuthZ Profiles, click the + sign | Choose Standard > Dclessons-Employee-Limit.
Click Done.| Click Save.
Now once completed, we have completed the Authorization policy.




LEAVE A COMMENT
Please login here to comment.