EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USVPNs & Tunnelling
VPN:
It enables host to access the private network of company via public network or Internet via secure connection.
There are two types of VPN connection.
- SSL VPNs
- IPSEC VPNs
SSL VPN:
In SSL VPN, the upper layer protocol and Transport layer protocols is replaced with another delivery protocols SSL/TLS.
The TLS (Transport Layer Security) and other protocols like Secure Socket Layer are cryptographic protocols based on X.509 digital certificates. It is like client – server process and below is the step of operation.
- A host starts website requiring SSL Connection.
- Server will send SSL certificates including server public key
- Clients verify the certificates and if valid creates the symmetric key which is encrypted with server public key and send back to server.
- Server decrypts the symmetric session key using private key and send back acknowledgement.
- All subsequent data is now encrypted with session key.
There are two modes of SSL VPN configuration.
- Web-only mode
- Tunnel Mode.
SSL VPN with Web-only Mode:
In web-only mode, user creates the VPN connection via web browser which has built-in SSL encryption and supported Java runtime. Before SSL VPN is created, User must be authorised.
As soon as SSL VPN session is established with fortinet unit, a web portal will be available which list all the supported services like HTTP, HTTPS, and TELNET, SSH etc. just like below screen shot.
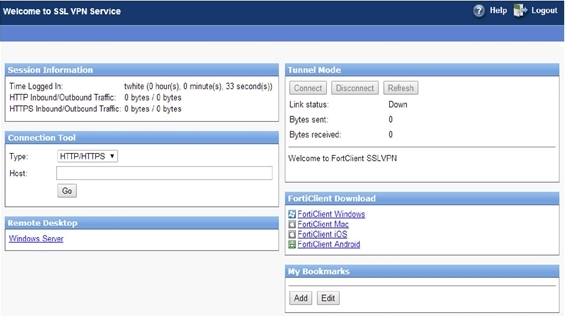
SSL VPN with Tunnel Mode:
In this mode VPN tunnel will be created by logging in to Web SSL VPN Portal. In this mode following are the steps.
- Fortinet unites authenticates host or client via Radius or AD services.
- The Browser redirects it to portal page
- A verification of installed VPN client occurs and plugin will be installed if needed.
- Clients receives VPN address from pool and SSL VPN tunnel is established.





LEAVE A COMMENT
Please login here to comment.